Cryptanalysis of Controlled Mutual Quantum Entity Authentication Using Entanglement Swapping∗
Gan Gao(高干) and Yue Wang(王悦)Department of Electrical Engineering,Tongling University,Tongling 244000,China
2Engineering Technology Research Center of Optoelectronic Technology Appliance,Tongling 244000,China
1 Introduction
Quantum entanglement is at the heart of quantum information,and it yields a variety of versatile applications in the region of quantum information science,including quantum teleportation,[1]quantum remote state preparation[2−6]and quantum cryptography.[7]In the late sixties of the twentieth century,Wiesner[7]first introduced the concept of quantum cryptography,which did not make people produce an interest at that time.In 1984,Bennett and Brassard[8]fostered a development of quantum cryptography,and used four quantum states from nonorthogonal basis to put forward a real quantum cryptography protocol.Here,let us explain what the quantum cryptography is.Simply speaking,it is a counterpart of classic cryptography in the quantum world.We all know that the classic cryptography relies on the high complexity of the underlying mathematical problems for its security.Di ff ering from the classic cryptography,the quantum cryptography o ff ers its security based on the principles of quantum mechanics.More importantly,the quantum cryptography can reach an unconditional security,however,the classic cryptography can not.Since the development of Bennett and Brassard,[8]the quantum cryptography has received a lot of attention over the past thirty years,and many kinds of quantum cryptography protocols have appeared,such as quantum key distribution,[9−26]quantum secure direct communication,[27−56]quantum identity authentication,[57−67]and so on.In addition,it is worth pointing out that,in the quantum cryptography,the designing of a protocol and the security analyzing of a protocol are two inherent directions,and each of them is necessary to the development of quntum cryptography.
Recently,using the GHZ-like states and the entanglement swapping,Kang,etal.proposed a controlled mutual quantum entity authentication(CMQEA)protocol.[67]Obviously,CMQEA belongs to a special quantum authentication.In Kang,etal.’s CMQEA protocol,[67]there are three participants:Charlie,Alice and Bob.Both Alice and Bob are the authenticated parties,and Charlie acts as the center which is similar to a telephone company,a server,etc.Although he can control all of the mutual authentication phases,Charlie is forbidden to obtain any secret message of the authenticated parties.Reviewing some controlled quantum cryptography protocols,[68−75]we see that the center,the telephone company and the server etal.in them are similarly forbidden in that aspect.In addition,it is seen that Kang etal.claimed that their CMQEA protocol was secure after the two possible attacks,the internal attack and the external attack were discussed.However,this is not a fact.In this paper,we will show that the center,Charlie may eavesdrop the secret keys of an authentication party without introducing any error,that is,we will prove that Kang etal.’s CMQEA protocol is not secure.By the way,the security is the most important requirement in the cryptography.In a quantum cryptography protocol,any secret message must be transmitted in a secure manner because its security is guaranteed by the principles of quantum mechanics.
2 Security Loophole of Kangetal.’s CMQEA Protocol
Before describing the security loophole,we need to give a brief description of Kang etal.’s CMQEA protocol[67]as follows.Step(1)Using QKD protocols,Alice and Bob share a secret sequence KAB=(k1,k2,...,kN).Here,ki∈ {I,σx,iσy,σz}.Step(2)The center,Charlie prepares a three-qubit GHZ-like state sequence(|ξ1,|ξ2,|ξ3,...).Here,(|000− |110− |011−|101).Charlie takes qubits A,B and C from each GHZ-like state to form sequences A,B,and C,and insertsNCdecoy qubits into sequences A and B.Then he sends sequence A and sequence B including decoy qubits to Alice and Bob,respectively.Step(3)After con fi rming that they have received the two sequences,Charlie utilizesNCdecoy qubits to check the transmission security of the two sequences.Step(4)Charlie requires that Alice performs the Pauli operator corresponding to the classical bit kion|ξ2i−1,or Bob performs it on|ξ2i.Step(5)Charlie uses the σzbasis to measure qubits C2i−1and C2i,that is,qubits C in|ξ2i−1and|ξ2i.Step(6)Alice performs Bell basis measurements on qubits A2i−1and A2i,that is,qubits A in|ξ2i−1and|ξ2i,and Bob does on qubits B2i−1and B2i,and then they both announce their measurement outcomes.Next,Charlie also announces his measurement outcomes in step(5).So Alice and Bob can authenticate each other.
Charlie’s eavesdropping strategy is as follows.In step(2),before Charlie sends sequences A and B including decoy qubits to Alice and Bob,respectively,he performs σz_basis measurements on qubits C2i−1and C2i,and Bell basis measurements on a pair of qubits A2i−1and A2iand a pair of qubits B2i−1and B2i.Since the checking security relies on decoy qubits in step(3),this action that Charlie performs these measurements ahead of schedule will not be detected by Alice and Bob.Therefore,when step(4)goes on,that is,when Charlie requires Alice or Bob to perform the Pauli operator,obviously,she or he does not perform the Pauli operator on GHZ-like states,but on Bell states now.However,Alice or Bob does not know this at all.When step(6)starts,as soon as Alice and Bob announce the measurement outcomes of Bell basis,Charlie will easily eavesdrop the Pauli operator,that is,the classical bit ki.Later on,Charlie is required to reveal his measurement outcomes on qubits C2i−1and C2i,and he may directly announce the previously obtaining measurement outcomes on them.At this stage,we can not help asking that this would introduce an error?The answer is no.Next,we will give the reason by proving that the attained measurement outcomes in two following cases are entirely same.
(i)The case that no eavesdropping exists.Suppose that Alice is required in step(4)and her Pauli operator is iσy.According to Kang etal.’s CMQEA protocol,the state of whole system is evolved as follows:
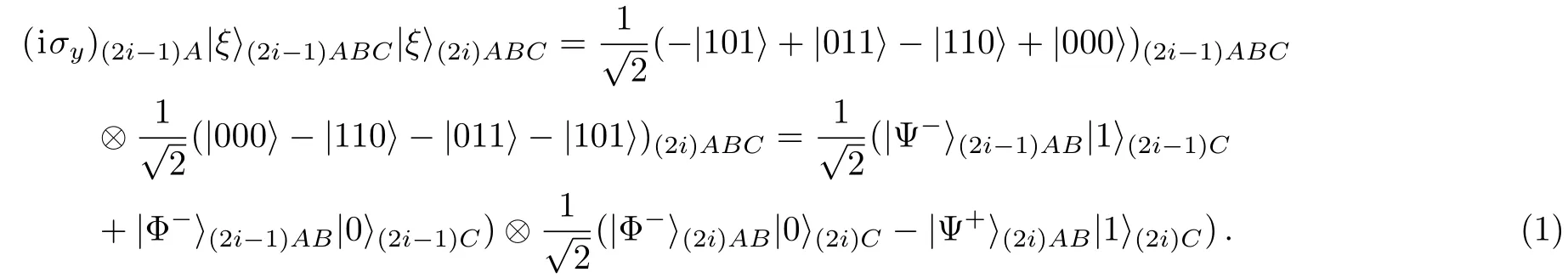
If Charlie’s measurement outcomes in step(5)is|0(2i−1)Cand|1(2i)C,|Φ−(2i−1)ABand|Ψ+(2i)ABwill be shared between Alice and Bob.When Alice and Bob perform Bell basis measurements,the state is evolved as follows:
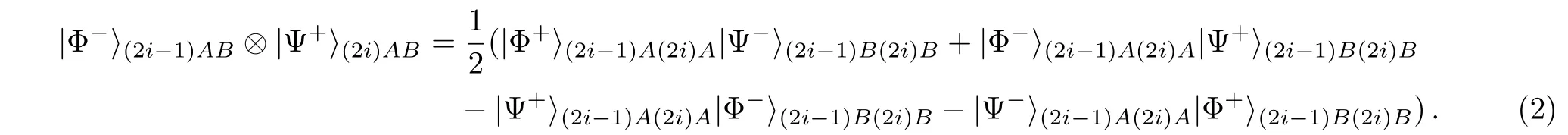
Obviously,their measurement outcomes is one of the four product states:|Φ+(2i−1)A(2i)A|Ψ−(2i−1)B(2i)B,|Φ−(2i−1)A(2i)A|Ψ+(2i−1)B(2i)B,|Ψ+(2i−1)A(2i)A|Φ−(2i−1)B(2i)B,|Ψ−(2i−1)A(2i)A|Φ+(2i−1)B(2i)B.
(ii)The case that the eavesdropping exists.Suppose that Charlie’s measurement outcomes is|0(2i−1)Cand|1(2i)C.According to Eq.(3),the system state will collapse to|Ψ+(2i−1)AB|Ψ+(2i)AB,which has the entanglement swapping process shown by Eq.(4).
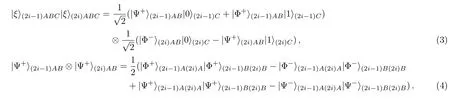
In Charlie’s eavesdropping strategy,we see that,besides the σzbasis measurements on qubits C2i−1and C2i,he performs Bell basis measurements.According to Eq.(4),|Ψ+(2i−1)AB|Ψ+(2i)ABwill collapse to one of the four product states:
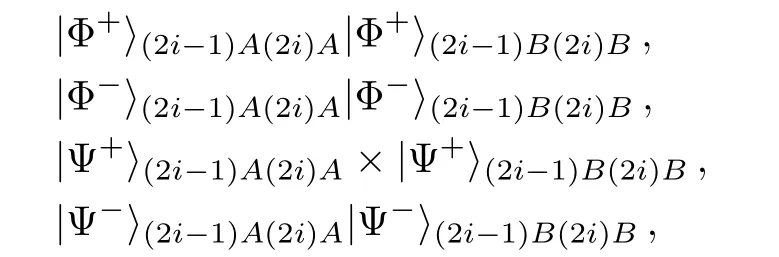
which is the scope of Charlie’s Bell basis measurement outcome.After Alice performs the Pauli operator iσy,the measurement outcomes that Alice and Bob announce will be one of the four outcomes:
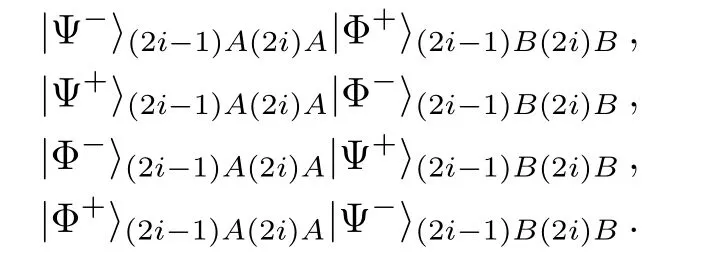
We see that the entanglement swapping of Bell states is fi nished by Alice and Bob in case(i)and it is fi nished by Charlie in case(ii),but the measuring and deducing outcomes of Alice and Bob in the two cases are entirely same.Obviously,this gives Charlie the chance that no error will be introduced when he eavesdrops the secret keys shared by Alice and Bob.That is to say,Alice and Bob cannot detect Charlie’s eavesdropping.
3 Conclusion
In conclusion,we have successfully proposed an attack on Kang etal.’s CMQEA protocol.[67]Since the proposed attack is executed by Charlie who is one of three participants of protocol,it should belong to the internal attack.However,the listed internal attack(the double CNOT attack)in Kang etal.’s CMQEA protocol is not a genuine internal attack because the eavesdropper who executes the attack is not the participant of protocol.In fact,the double CNOT attack in Kang etal.’s CMQEA protocol should also belong to the external attack.In other words,Kang etal.[67]only discussed an external attack when analyzing the security of their CMQEA protocol.Obviously,the discussion is not all-sided.By re-analyzing the security from the aspect of internal attack,we detect that Kang etal.’s CMQEA protocol is not secure because the participant in it,Charlie can eavesdrop the secret keys shared between two authentication parties without introducing any error.
Acknowledgments
We thank the anonymous referee for his/her important and helpful suggestions.
References
[1]C.H.Bennett,G.Brassard,C.Cr´epeau,R.Jozsa,A.Peres,and W.K.Wootters,Phys.Rev.Lett.70(1993)1895.
[2]H.K.Lo,Phys.Rev.A 62(2000)012313.
[3]A.K.Pati,Phys.Rev.A 63(2000)014302.
[4]D.Wang,Y.D.Hu,Z.Q.Wang,and L.Ye,Quantum Inf.Process.14(2015)2135.
[5]D.Wang,A.J.Huang,W.Y.Sun,J.D.Shi,and L.Ye,Quantum Inf.Process.15(2016)33671.
[6]D.Wang,R.D.Hoehn,L.Ye,and S.Kais,Entropy 17(2015)1755.
[7]S.Wiesner,Conjugate Coding.SIGACT News 15(1983)78.
[8]C.H.Bennett and G.Brassard,in a Proceedings of the IEEE International Conference on Computers,Systems and Signal Processings,Bangalore,India,IEEE,New York(1984)p.175.
[9]C.H.Bennett,G.Brassard,and N.D.Mermin,Phys.Rev.Lett.68(1992)557.
[10]A.Cabello,Phys.Rev.Lett.85(2000)5635.
[11]F.G.Deng and G.L.Long,Phys.Rev.A 68(2003)042315.
[12]K.Wen and G.L.Long,Phys.Rev.A 72(2005)022336.
[13]C.Y.Li,H.Y.Zhou,Y.Wang,and F.G.Deng,Chin.Phys.Lett.22(2005)1049.
[14]F.Gao,F.Z.Guo,Q.Y.Wen,and F.C.Zhu,Phys.Lett.A 349(2006)53.
[15]X.H.Li,F.G.Deng,and H.Y.Zhou,Phys.Rev.A 78(2008)022321.
[16]G.Gao,Opt.Commun.281(2008)876.
[17]C.Wang,L.Xiao,W.Wang,G.Zhang,and G.L.Long,J.Opt.Soc.Am.B 26(2009)2072.
[18]G.Gao,Phys.Scr.81(2010)065005.
[19]A.E.Allati,M.E.Baz,and Y.Hassouni,Quantum Inf.Process.10(2011)589.
[20]C.F.Fung,X.Ma,H.F.Chau,and Q.Cai,Phys.Rev.A 85(2012)032308.
[21]C.W.Yang and T.Hwang,Quantum Inf.Process.12(2013)3207.
[22]P.Huang,G.He,J.Fang,and G.Zeng,Phys.Rev.A 87(2013)012317.
[23]C.Dong,S.H.Zhao,W.H.Zhao,L.Shi,and G.H.Zhao,Quantum Inf.Process.13(2014)2525.
[24]G.Gao,Chin.Phys.B 24(2015)080305.
[25]L.L.Liu and T.Hwang,Quantum Inf.Process.14(2015)989.
[26]Paulo Vinicius Pereira Pinheiro and Rubens Viana Ramos,Quantum Inf.Process.14(2015)2111.
[27]G.L.Long and X.S.Liu,arXiv:quant-ph/0012056 v1;G.L.Long and X.S.Liu,Phys.Rev.A 65(2002)032302.
[28]F.G.Deng,G.L.Long,and X.S.Liu,Phys.Rev.A 68(2003)042317.
[29]F.G.Deng and G.L.Long,Phys.Rev.A 69(2004)052319.
[30]Q.Y.Cai and B.W.Li,Phys.Rev.A 69(2004)054301.
[31]C.Wang,F.G.Deng,Y.S.Li,X.S.Liu,and G.L.Long,Phys.Rev.A 71(2005)044305.
[32]C.Wang,F.G.Deng,and G.L.Long,Opt.Commun.253(2005)15.
[33]M.Lucamarini and S.Mancini,Phys.Rev.Lett.94(2005)140501.
[34]Y.Q.Zhang,X.R.Jin,and S.Zhang,Phys.Lett.A 341(2005)380.
[35]Z.X.Man,Z.J.Zhang,and Y.Li,Chin.Phys.Lett.22(2005)18.
[36]X.H.Li,F.G.Deng,C.Y.Li,Y.J.Liang,P.Zhou,and H.Y.Zhou,J.Korean Phys.Soc.49(2006)1354.
[37]J.Wang,Q.Zhang,and C.J.Tang,Phys.Lett.A 358(2006)256.
[38]G.Gao,Commun.Theor.Phys.50(2008)368.
[39]X.H.Li,F.G.Deng,and H.Y.Zhou,Phys.Rev.A 74(2006)054302.
[40]X.H.Li,C.Y.Li,F.G.Deng,P.Zhou,Y.J.Liang,and H.Y.Zhou,Chin.Phys.16(2007)2149.
[41]Y.Xia and H.S.Song,Phys.Lett.A 364(2007)117.
[42]M.Y.Wang and F.L.Yan,Chin.Phys.Lett.24(2007)2486.
[43]S.Lin,Q.Y.Wen,F.Gao,and F.C.Zhu,Phys.Rev.A 78(2008)064304.
[44]S.Pirandola,S.L.Braunstein,S.Mancini,and S.Lloyd,EPL 84(2008)20013.
[45]X.Yi,Y.Y.Nie,N.Zhou,Y.Huang,and Z.Hong,Int.J.Theor.Phys.47(2008)3401.
[46]G.Gao,Opt.Commun.283(2010)2288.
[47]T.J.Wang,T.Li,F.F.Du,and F.G.Deng,Chin.Phys.Lett.28(2011)040305.
[48]B.Gu,Y.C.Huang,X.Fang,and C.Y.Zhang,Chin.Phys.B 20(2011)100309.
[49]B.Gu,C.Y.Zhang,G.S.Cheng,and Y.G.Huang,Sci.China:Phys.Mech.Astron.54(2011)942.
[50]C.W.Tsai,C.R.Hsieh,and T.Hwang,Eur.Phys.J.D 61(2011)779.
[51]L.Dong,X.M.Xiu,Y.J.Gao,Y.P.Ren,and H.W.Liu,Opt.Commun.284(2011)905.
[52]G.Gao,M.Fang,and R.M.Yang,Int.J.Theor.Phys.50(2011)882.
[53]Z.W.Sun,R.G.Du,and D.Y.Long,Int.J.Theor.Phys.51(2012)1946.
[54]B.C.Ren,H.R.Wei,M.Hua,T.Li,and F.G.Deng,Eur.Phys.J.D 67(2013)30.
[55]S.H.Kao and T.Hwang,Quantum Inf.Process.12(2013)3791.
[56]S.Hassanpour and M.Houshmand,Quantum Inf.Process.14(2015)739.
[57]M.Dusek,O.Haderka,M.Hendrych,and R.Myska,Phys.Rev.A 60(1999)149
[58]M.Curty and D.J.Santos,Phys.Rev.A 64(2001)062309.
[59]T.Mihara,Phys.Rev.A 65(2002)052326.
[60]N.Zhou,G.Zeng,W.Zeng,and F.Zhu,Opt.Commun.254(2005)380.
[61]Z.S.Zhang,G.H.Zeng,N.R.Zhou,and J.Xiong,Phys.Lett.A 356(2006)199.
[62]Y.G.Yang,Q.Y.Wen,and X.Zhang,Sci.China:Phys.Mech.Astron.51(2008)321.
[63]Y.G.Yang and Q.Y.Wen,Chin.Phys.B 18(2009)3233.
[64]P.Huang,J.Zhu,Y.Lu,and G.H.Zeng,Int.J.Quantum Inf.9(2011)701.
[65]Y.G.Yang,H.Y.Wang,X.Jia,and H.Zhang,Int.J.Theor.Phys.52(2013)524.
[66]W.M.Shi,Y.H.Zhou,and Y.G.Yang,Quantum Inf.Process.13(2014)1501.
[67]M.S.Kang,C.H.Hong,J.Heo,J.I.Lim,and H.J.Yang,Chin.Phys.B 24(2015)090306.
[68]C.Y.Li,H.Y.Zhou,Y.Wang,and F.G.Deng,Chin.Phys.Lett.22(2005)1049.
[69]C.Y.Li,X.H.Li,F.G.Deng,P.Zhou,Y.J.Liang,and H.Y.Zhou,Chin.Phys.Lett.23(2006)2896.
[70]W.Y.Wang,C.Wang,K.Wen,and G.L.Long,Chin.Phys.Lett.24(2007)1463.
[71]X.J.Wen,Y.Liu,and N.R.Zhou,Opt.Commun.275(2007)278.
[72]L.Dong,X.M.Xiu,Y.J.Gao,and F.Chi,Opt.Commun.281(2008)6135.
[73]X.M.Xiu,L.Dong,Y.J.Gao,and F.Chi,Opt.Commun.282(2009)333.
[74]G.Gao,Phys.Scr.89(2014)125102.
[75]W.Huang,Q.Y.Wen,B.Liu,and F.Gao,Chin.Phys.B 24(2015)070308.
 Communications in Theoretical Physics2017年1期
Communications in Theoretical Physics2017年1期
- Communications in Theoretical Physics的其它文章
- Ground State Properties of Z=126 Isotopes within the Relativistic Mean Field Model∗
- An Improved Singularity Free Self-Similar Model of Proton Structure Function
- Relativistic Bound and Scattering Amplitude of Spinless Particles in Modi fi ed Schioberg Plus Manning–Rosen Potentials
- Electron-Positron Pair Production in Strong Fields Characterized by Conversion Energy∗
- Laser Polarization E ff ect on Molecular Harmonic and Elliptically Polarized Attosecond Pulse Generation∗
- Exact Calculation of Antiferromagnetic Ising Model on an Inhomogeneous Surface Recursive Lattice to Investigate Thermodynamics and Glass Transition on Surface/Thin Film∗
