Error Rate Estimation in Quantum Key Distribution with Finite Resources∗
Zhao Lu(卢钊)Jian-Hong Shi(史建红)† and Feng-Guang Li(李风光)Zhengzhou Information Science and Technology InstituteZhengzhou 45000China
2Science and Technology on Information Assurance Laboratory,Beijing 100072,China
1 Introduction
Quantum key distribution(QKD)has been greatly developed(Refs.[1–7])in theory and experiment since BB84 protocol[8]was proposed in 1984.The security of QKD with finite resources analyzed in Refs.[9–10].In QKD protocol,two authorized parties(Alice and Bob)obtain sifted key after quantum signal generation,transmission,detection and basis sifting.Because of imperfection of experimental equipment,disturbance of external environment and eavesdropping from attacker Eve,Alice and Bob have a few different bits in sifted key and some information of sifted key has been obtained by Eve.Hence,classical post-processing protocols(Refs.[11–13]),such as error correction,privacy amplification and authentication,were applied to generate consistent and secure key.Before performing these post-processing processes,we need to estimate the error rate of sifted key,which is an important parameter of error correction(Refs.[14–16])and final secure key generation rate(Refs.[17–18]).Meanwhile,error rate estimation is an important component of parameter estimation,[10]which includes gaining estimation of quantum signal and error rate estimation etc.If error rate is beyond a given threshold,two partners would abort QKD protocol;otherwise,they would continue.Therefore,the accuracy of error rate estimation directly impacts the efficiency of error correction and the performance of QKD system with finite resources.
In existing QKD protocols,random sampling is the usual method of error rate estimation.Alice and Bob sample and reveal a part of sifted key randomly and compare them to obtain the error rate of these sifted key,which is served as the estimated error rate of remaining sifted key.For security consideration,the sampled key is discarded by Alice and Bob,because Eve can obtain the sampled key.Sampling rate is the ratio between the length of sampled key and sifted key.Sampling rate is closely related with the accuracy of estimated error rate and the final secure key generation rate.Erroneous judgment probability can re flect the accuracy of error rate estimation.Another error rate estimation method named parity comparison[19]was proposed in 2015.This method is suitable for the situation that the length of sifted key is short or the error rate is low.However,the computation complexity of this method is higher than that of random sampling method when the length of sifted key is long.
In this paper,we optimize random sampling method to estimate the error rate of sifted key.We analyze the relationship between some parameters about error rate estimation,such as sampling rate and erroneous judgment probability.And then,we determine the optimal sampling rate to increase the final secure key generation rate in QKD with finite resources.We focus our discussion on error rate estimation,hence we do not discuss the devices and security of QKD with finite resources too much.We assume that the QKD system is security and the light source is a single-photon source.
This paper is organized as follows.Section 2 presents the connection between sampling rate and erroneous judgment probability when estimating error rate with random sampling method.Section 3 describes how to optimize random sampling method.Section 4 analyzes the performance of optimized random sampling method in QKD system with finite resources.
2 Sampling Rate and Erroneous Judgment Probability
Sampling rate is the ratio between the length of sampled key and sifted key.In order to ensure the securityof final key,sampled key must be discarded.When sampling rate is small,there is a deviation between estimated error rate and actual error rate of sifted key.Erroneous judgment probability is defined as the probability that estimated error rate beyond the available deviation of error rate estimation.
Leta(a<A)bits be sampled randomly fromAbits sifted key containingBerrors.Let random variableξbe the number of errors inarandom sampled bits,then
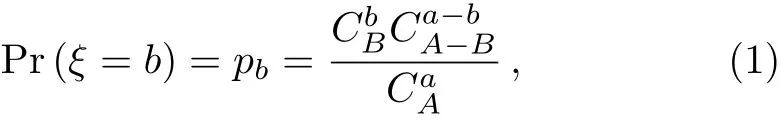
with the combinatorial number0≤i≤n,and 0 ≤b≤ min{B,a}.Random variableξobeys hypergeometric distribution,[20]and

Letp=B/Abe the error rate ofAbits sifted key of two parties,a/Abe the sampling rate.Sop′=b/ais the estimated error rate,which is the error rate ofabits key sampled fromAbits sifted key randomly.λis the allowable deviation of estimated error rate.Ifp′∈ [p−λ,p+λ],we say the estimated error ratep′is relatively accurate.Ifp′/∈[p−λ,p+λ],we say the estimated error ratep′is inaccurate and occurs erroneous judgement.The erroneous judgement probability of estimated error ratepejpis the probability thatp′/∈[p−λ,p+λ],so
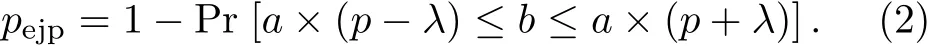
That is,the erroneous judgment probability is determined by the lengthAof sifted key,the actual error ratep=B/Aof sifted key and the sampling ratea/A.
We discuss this situation through numerical simulation now.For finite length of sifted key,we analyze the relationship of erroneous judgement probability,the length of sifted key,allowable deviation and the value of estimated error rate.According to the distribution function of hypergeometric distribution,we can calculate erroneous judgement probability and show their relationship by surface fitting.
When the actual error rate of sifted key is 5%,the sampling rates are 50%and 20%,Figs.1 and 2 show the erroneous judgement probabilities respectively.The points in two figures represent erroneous judgement probabilities with different sampling rates,lengths of sifted key and allowable deviations of error rate.
As Figs.1 and 2 indicate,when the length of sifted key is large and the sampling rate is high,the error rate of remaining sifted key can be estimated accurately with random sampling method.And the erroneous judgement probability is very small.Hence,the error rate estimation maybe exist erroneous judgement evidently when the length of sifted key or the allowable deviation is relatively small.
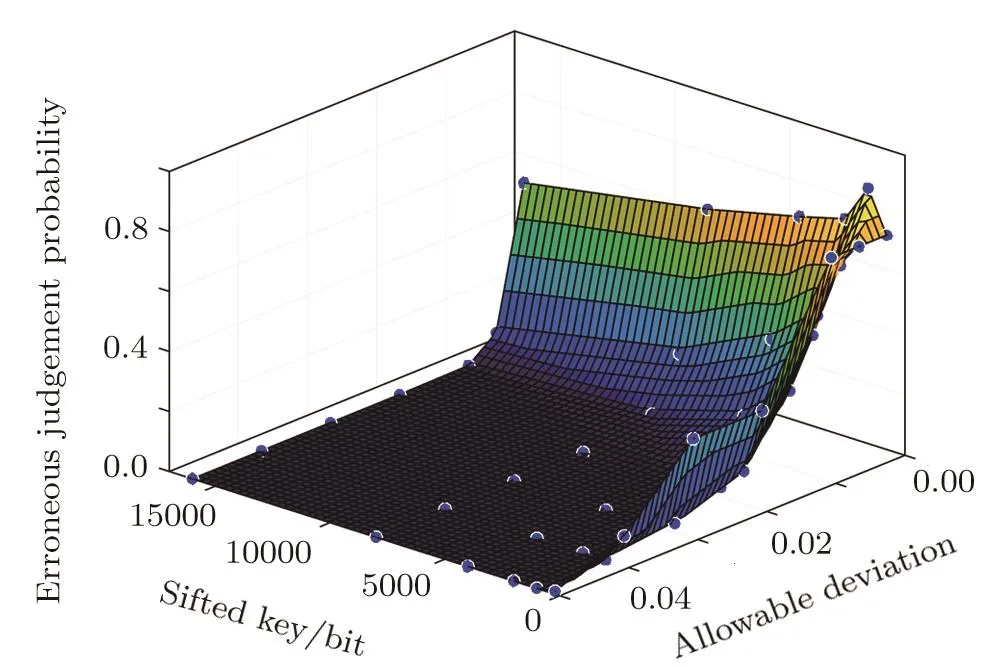
Fig.1 (Color online)Erroneous judgement probability(sampling rate is 50%).

Fig.2 (Color online)Erroneous judgement probability(sampling rate is 20%).
High sampling rate can make error rate estimation more accurate,but more sifted key bits are discarded,and less sifted key bits are left in error correction in this situation.Therefore,it is necessary to find a criterion for optimal sampling rate.
3 Optimizing the Random Sampling Rate
To optimize the random sampling method,we need to obtain the optimal sampling rate.In the following,we analyze the relationship between sampling rate and final secure key generation rate and compute the optimal sampling rate.
3.1 Relationship between Sampling Rate and Final Secure Key Generation Rate
Now,let us examine the relationship between sampling rate and final secure key generation rate in decoy state QKD system with finite resources(Refs.[18,21–25]).
Supposing Alice sends BobNpluses with three different light intensities,in which one is signal state with intensityµ,others are weak decoy state with intensityνand vacuum state.Alice randomly chooses one of three kinds of pluses with the probabilitiesq1,q2,q3,q1+q2+q3=1.Hence the number of signal state pluses,weak decoy state pluses and vacuum pluses areNµ=q1×N,Nν=q2×N,N0=q3×Nrespectively.Letqsbe the sampling rate of the sifted key in the error rate estimation.Correspondingly,the number of sampling pulses ism=qs×q1×N,and the number of remaining pulses isn=(1−qs)×q1×N.
When the photon source is single-photon source,the final secure key generation rate[23]of decoy state QKD with finite resources is defined as
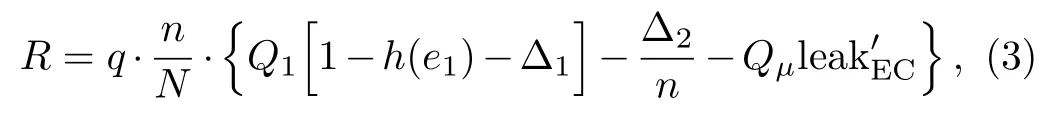
whereqis sifting ratio,Q1is the gain of single photon states,ande1is the quantum bit error rate(QBER)of single photon pulses.The security parameters of error correction and privacy amplification are defined by Δ1=and Δ2=2log21/[2(ε−−εEC)].εis the security bound,εECis the error probability of error correction.and′are parameters that are needed to be optimized to maximize the key rate.Qµ=1−e−ηµ(1−Y0)is the total gain of signal state.is the leaked information of actual error correction algorithm with the binary Shannon entropy functionh(x)=−xlog2(x)−(1−x)log2(1−x).Eµis the QBER of the signal state.The error correction eきciencyfis defined asf=|M|/h(X|Y).|M|is the actual leaked information,which is related with the estimated error rate.h(X|Y)is the theoretical leaked information,which is related with the actual error rateEµ.
According to the parameter estimation of decoy state quantum key distribution,[20]we haveEµQµ=e0Y0+ed(1− e−ηµ),which is the weighted average of the QBERs of various photon number eigenstates.Y0is the background rate.ηis the probability of the photon Alice send to Bob can be detected withη=ηc×ηBob,whereηc=10−αl/10is the transmission eきciency of channel andηBobis the detection eきciency of Bob.αis the channel loss coeきcient andlis the transmission distance.e0is the QBER for the vacuum,andedis the probability that a photon hits the erroneous detector.is the lower bound of the yield of single photon pulses with
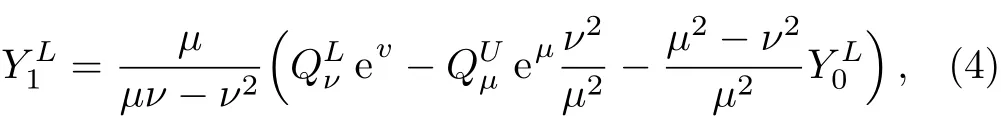
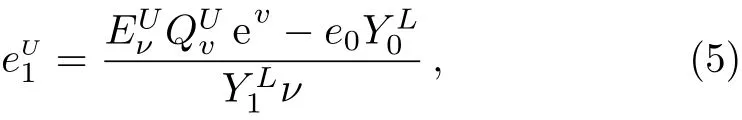
From the formula(3), final secure key generation rate is affected by sampling rate in two sides.On one hand,the sampled key cannot be used to generate secure key and must be discarded from the sifted key.The larger sampling rate is,the less final secure key generation rate will be.On the other hand,sampling rate decides the accuracy of estimated error rate,and the accuracy of estimated error rate in fluences the final secure key generation rate.The larger sampling rate is,the more accurate estimated error rate will be.Therefore,the final secure key generation rate can be defined as an indicator of whether sampling rate reaches optimum or not.
3.2 Optimal Sampling Rate
Optimal sampling rate is defined as the sampling ratio,which can make final secure key generation rate reach its maximum with high probability.We claim thatλis the allowable deviation of error rate estimation.The computational method of optimal sampling rate runs as follows.First,for a given actual error rate,we divide the possible value range of estimated error rate into several intervals[a0,a1),[a1,a2),...,[ai,Eµ−λ),[Eµ−λ,Eµ+λ),...,[an−1,an],andai+1=Eµ−λ,ai+2=Eµ+λ,0≤a0<a1<···<an≤ 1.Then,with the probability distribution function of hypergeometric distribution,we can compute the probabilitiesp1,p2,...,pnof estimated error rate values falling in each interval,and assign an estimated error rate value for each intervalEµ,1,Eµ,2,...,Eµ,n.Later,for thesensituations,we can obtainnfinal secure key generation ratesR1,R2,...,Rnrespectively.The weighted average of thesenfinal secure key generation rates can be computed by

whereRi(1≤i≤n)is the final secure key generation rate when the estimated error rate value belongs to interval[ai−1,ai].Finally,by traversing sampling rate from 0 to 1,we can gain different weighted averages of final secure key generation rates.The optimal sampling rate is obtained when the weighted averagereaches maximum value.
4 Simulation Analysis
Assuming that the fixed allowable deviation of error rate estimation is 0.002,we can divide the possible value range of error rate estimation into five intervals[0,Eµ−0.012),[Eµ−0.012,Eµ−0.002),[Eµ−0.002,Eµ+0.002),[Eµ+0.002,Eµ+0.012),and[Eµ+0.012,1].The first two intervals are the situations that estimated error rate is lower than the actual error rate,the third interval is the situation that estimated error rate is relatively accurate,and the last two intervals are the situations that estimated error rate is higher.With the probability distribution function of hypergeometric distribution,we can compute the corresponding probabilitiesp1,p2,p3,p4,p5.According to Eqs.(3)and(6),the weighted average of the final secure key generation rates of five intervals is defined as

wherepi(1≤i≤5)is the probability of estimated error rate value falling in the corresponding interval.Ri(1≤i≤5)is the final secure key generation rate when the estimated error rate value belongs to the corresponding interval.For each estimated error rate value,we can calculate the corresponding parameters,such as the gain of single photon statesQ1,i,the QBER of single photon pulsese1,i,the security parameter of error correction Δ1,i,the security parameter of privacy amplification Δ2,i,the total gain of signal stateQµ,i,the leaked information of actual error correction algorithmthe error correction eきciencyfi,the final secure key generation rateRi.Finally,we can obtain the weighted average of final secure key generation rates.
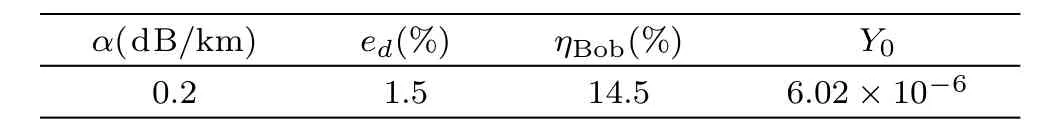
Table 1 Practical simulation parameters.[27]
Some practical numerical simulation parameters are defined by the 144 km QKD experiment reported from Ref.[26],and other parameters are defined asµ=0.48,ν=0.05,e0=0.5,q=0.5,q1=0.6,q2=0.3,q3=0.1,ε=10−9,εEC=10−10,=10−10,′=10−11.
The error correction is based on Cascade protocol(Refs.[28–30]),in which the block length of error correction is 105bits. For the error correction eきciencyf=|M|/h(X|Y),|M|is the actual leaked information in error correction,which is related with the estimated error rate and Cascade protocol.

Fig.3 (Color online)For each number of pulses,The relationship between optimal sampling rate and weighted average of final secure key generation rates.
When the actual error rate of sifted key is fixed,such asEµ=0.0352,Fig.3 shows us whatever the number of pulses is,we can obtain optimal sampling rate,the weighted average of final secure key generation rates is changed by the sampling rate increasing,and the maximal weighted average of final secure key generation rates corresponds to the optimal sampling rate.The red points represent the optimal sampling rates and the corresponding maximal weighted averages of final secure key generation rates.Such as when the number of pulses is 8×109,the optimal sampling rate is 24.74%,the weighted average of final secure key generation rates reaches 1.4708×10−6,and the final secure key generation rate can reach maximum value with high probability.Figure 4 presents the optimal sampling rates when the number of pulses changes.The coordinates of each point of line represent number of pulses,optimal sampling rate and weighted average of final secure key generation rates.We may obtain the optimal sampling rate in various circumstances.As Fig.5 shows,when the number of transmitted pulses is fixed,such asN=7×109,N=1.5× 1010,for different actual error rates of sifted key,we can obtain the optimal sampling rate to reduce the in fluence of parameter estimation for secure key generation.The red points represent the optimal sampling rates and the corresponding maximal weighted averages of final secure key generation rates.
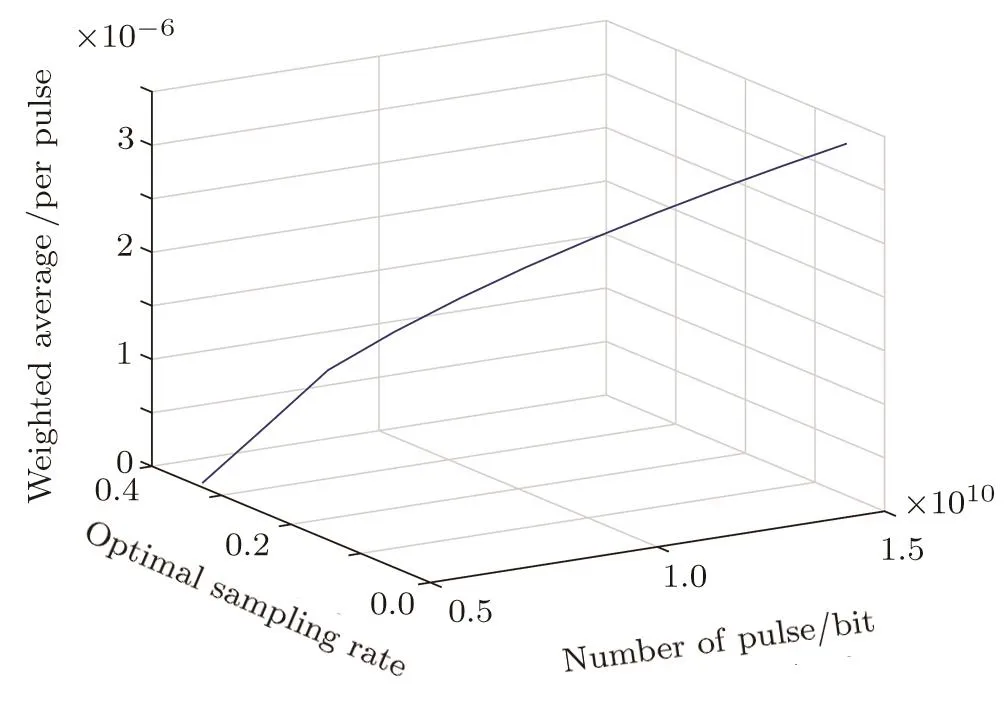
Fig.4 (Color online)The relationship between the number of pulses,optimal sampling rate and weighted average of final key generation rates.
In practical quantum key distribution,sampling rate is often a fixed value regardless of the fluctuating of experiment parameters,such as 20%.Obviously the fixed value is not always suitable for the practical situations.For instance,when the actual error rate is 0.0352 and the number of transmitted pulses is 8×109,the optimal sampling rate is 24.74%,rather than 20%.
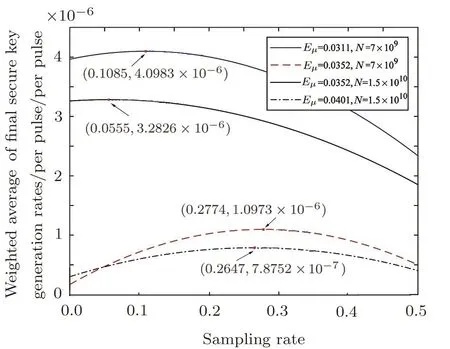
Fig.5 (Color online)For each actual error rate of sifted key,The relationship between optimal sampling rate and weighted average of final secure key generation rates.
5 Conclusion
Error rate estimation is a significant part for many QKD systems.If large deviation appears in error rate estimation,the final secure key generation rate of the QKD system will be reduced seriously between legitimate parties.We analyze the sampling rate and the erroneous judgement probability of error rate estimation using random sampling method,and discuss how the sampling rate affects final secure key generation rate in decoy state QKD with finite resources.We propose a method to compute the optimal sampling rate to maximize the bene fit for QKD system,which provides guidance to how to choose the sampling rate size in error rate estimation for practical QKD system.
[1]W.Y.Hwang,Phys.Rev.Lett.91(2003)508.
[2]F.Grosshans,G.V.Assche,J.Wenger,R.Brouri,N.J.Cerf,and P.Grangier,Nature(London)421(2003)238.
[3]P.Eraerds,N.Walenta,M.Legre,N.Gisin,and H.Zbinden,New J.Phys.12(2010)155.
[4]X.Y.Wang,Z.L.Bai,S.F.Wang,Y.M.Li,and K.C.Peng,Chin.Phys.Lett.30(2013)10305.
[5]Z.Wei,W.Wang,Z.Zhang,M.Gao,and X.F.Ma,Sci.Rep.3(2013)800.
[6]H.L.Yin,W.F.Cao,Y.Fu,Y.L.Tang,Y.Liu,T.Y.Chen,and Z.B.Chen,Opt.Lett.39(2014)5451.
[7]H.L.Lo,M.Curty,and K.Tamaki,Nature Photon.8(2014)595.
[8]C.H.Bennett and G.Brassard,1984 Proceedings of the IEEE International Conference on Computers,Systems and Signal Processing,December 10-12,New York(1984),p.175.
[9]J.Hasegawa,M.Hayashi,T.Hiroshima,and A.Tomita,arXiv:0707.3541(2007).
[10]L.B.Zhao,H.W.Li,and Z.Q.Yin,Chin.Phys.B 23(2014)100304.
[11]R.Renner and R.König,inTheory of Cryptography:Second Theory of Cryptography Conference,TCC 2005,Lecture Notes in Computer Science,ed.J.Kilian,Vol.3378,Springer Verlag(2005)p.407.
[12]C.H.F.Fung,X.F.Ma,and H.F.Chau,Phys.Rev.A 81(2010)15780.
[13]C.H.F.Fung,X.F.Ma,H.F.Chau,and Q.Y.Cai,Phys.Rev.A 85(2012)1178.
[14]G.Brassard and L.Salvail,inAdvances in Cryptology–EUROCRYPT’93,Vol.765 of Lecture Notes in Computer Science,ed.T.Helleseth,Springer,Heidelberg(1994)p.410.
[15]D.Elkouss,J.Martinez-Mateo,and V.Martin,Quantum Inf.Comput.11(2011)226.
[16]J.Martinez-Mateo,D.Elkouss,and V.Martin,Sci.Rep.3(2013)1576.
[17]D.Gottesman,H.K.Lo,N.LüTkenhaus,and J.Preskill,Quantum Inf.Comput.4(2004)325.
[18]V.Scarani and R.Renner,Phys.Rev.Lett.100(2008)1586.
[19]M.Li,T.Patcharapong,C.M.Zhang,Y.Q.Yin,W.Chen,and Z.F.Han,Chin.Phys.B 24(2015)153.
[20]L.Egghe and R.Rousseau,J.Doc.53(1997)488.
[21]T.Meyer,H.Kampermann,M.Kleinmann,and D.Bruß,Phys.Rev.A 74(2006)520.
[22]M.Hayashi,Phys.Rev.A 76(2007)012329.
[23]S.H.Sun,L.M.Liang,and C.M.Li,Phys.Lett.A 373(2009)2533.
[24]M.Tomamichel,C.C.W.Lim,N.Gisin,and R.Renner,Nat Commun.3(2012)19596.
[25]C.Zhou,W.S.Bao,H.W.Li,Y.Wang,Y.Li,Z.Q.Yin,W.Chen,and Z.F.Han,Phys.Rev.A 89(2014)215.
[26]H.K.Lo,X.F.Ma,and K.Chen,Phys.Rev.Lett.94(2010)230504.
[27]R.Ursin R,F.Tiefenbacher F,T.Schmitt-Manderbach T,H.Weier H,T.Scheidl T,M.Lindenthal,B.Blauensteiner,T.Jennewein,J.Perdiguse,P.Trojek,B.Ömer,M.Fürst,M.Meyenburg,J.Rarity,Z.Sodnik,C.Barbieri,H.Weinfurter,and A.Zeilinger,Nature Phys.3(2007)481.
[28]G.Brassard and L.Salvail,1994 EUROCRYPT’93 Advances in Cryptology,Lecture Notes in Computer Science,Springer-Verlag,Berlin(1994)p.410.
[29]T.Sugimoto and K.Yamazaki,IEICE TRANSACTIONS on Fundamentals of Electronics,Communications and Computer Sciences E 83-A(1987)1987.
[30]D.Elkouss,A.Leverrier,R.All´eaume,and J.J.Boutros,inProceedings of the 2009 IEEE International Conference on Symposium on Information Theory,Vol.3,ISIT’09,Piscataway(2009)p.1879.
 Communications in Theoretical Physics2017年4期
Communications in Theoretical Physics2017年4期
- Communications in Theoretical Physics的其它文章
- Dynamics of Optical Bistability with Kerr-nonlinear Blackbody Radiation Reservoir
- Quantum Phases of Cold Bosonic Atoms in an Optical Lattice with Inhomogeneous Atomic Interactions and Coexistence of Multi Phases∗
- Special Property of Group Velocity for Temporal Dark Soliton∗
- Collisions and Trapping of Time Delayed Solitons in Optical Waveguides with Orthogonally Polarized Modes∗
- Dual Solutions of MHD Boundary Layer Flow of a Micropolar Fluid with Weak Concentration over a Stretching/Shrinking Sheet
- Instability Analysis of Positron-Acoustic Waves in a Magnetized Multi-Species Plasma
