一种基于前端JS的CSRF防护设计
郑苏宁


关键词: 跨站请求伪造; 前端JS; 令牌; Web应用防火墙
Abstract:CSRF (Cross-Site Request Forgery) is a very popular Web attack method. At present, there are some problems in the universality and effectiveness of the solutions to protect CSRF, which can not achieve good protection effect. Therefore, a CSRF protection design based on JavaScript is proposed. By executing JS (JavaScript) files, the client can add and refresh cookie tokens or URL tokens for POST requests, making the attacker's malicious request unable to refresh the tokens and finally the attack fails. The design can be applied to Web application firewall to defend CSRF attack more effectively.
1 引言
跨站请求伪造[1](Cross-Site Request Forgery,CSRF)攻击是一种常见的Web攻击,容易在用户不知情的情况下进行转账、修改密码等各种敏感操作,造成巨大的危害。
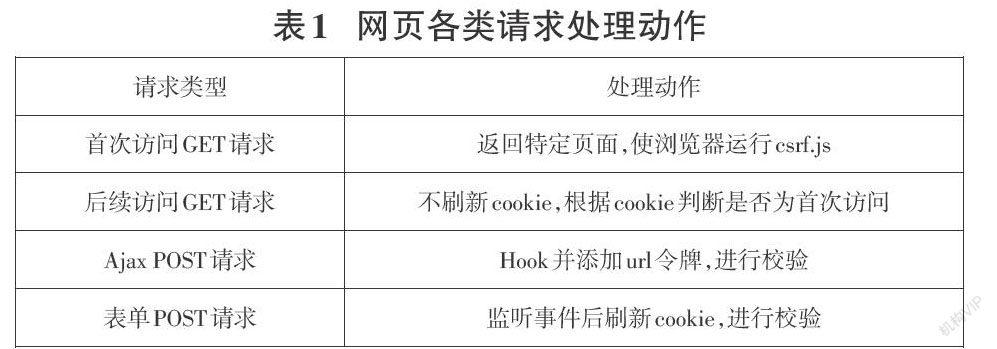
2 基于前端JS的CSRF防护设计
2.1 CSRF攻击及防御现状
CSRF攻击主要有标签类GET请求、POST请求、链接类GET请求三种方式。标签类GET请求攻击是一种比较简单的方式,常常利用恶意网页的标签src属性发出GET请求,攻击示例有,
