Secrecy Outage Probability for Two-Way Integrated Satellite Unmanned Aerial Vehicle Relay Networks with Hardware Impairments
Xiaoting Ren and Kefeng Guo
1College of Public Management,China University of Mining and Technology,Xuzhou,221116,China
2School of Space Information,Space Engineering University,Beijing,101407,China
ABSTRACT In this paper,we investigate the secrecy outage performance for the two-way integrated satellite unmanned aerial vehicle relay networks with hardware impairments.Particularly,the closed-form expression for the secrecy outage probability is obtained.Moreover, to get more information on the secrecy outage probability in a high signalto-noise regime, the asymptotic analysis along with the secrecy diversity order and secrecy coding gain for the secrecy outage probability are also further obtained,which presents a fast method to evaluate the impact of system parameters and hardware impairments on the considered network.Finally, Monte Carlo simulation results are provided to show the efficiency of the theoretical analysis.
KEYWORDS Integrated satellite unmanned aerial vehicle relay networks; two-way unmanned aerial vehicle relay; hardware impairments;secrecy outage probability(SOP);asymptotic SOP
1 Introduction
It is reported that satellite communication (SatCom) is considered to be a wishing way for the sixth generation (6G) and beyond next generation (BNG) wireless communication system for its special characters,such as the wide coverage and particular services[1-5].Owing to similar reasons,it can make up for the shortage of unmanned aerial vehicle(UAV)networks along with the high data transmission and wide coverage.Based on this foundation,to both utilize the advantage of the SatCom and UAV networks,the framework for the integrated satellite UAV relay network(ISUAVRN)appears,which is considered the major part of the future wireless communication networks [6,7].Besides,owing to the transmission beam’s wide coverage, many users or relays existed in one beam [7-11].In[7],a selection scheme based on the threshold was provided to keep the balance between the system performance and system complexity for the considered network.Furthermore,the outage probability(OP)was studied.In[8],one partial selection scheme was utilized to enhance the system performance for the considered networks.In [9], the authors studied the OP for the cognitive networks, which combined the satellite and the terrestrial networks.In[10],the OP was researched for the considered networks along with the secondary network selection scheme under the cognitive technology.In[11],the authors gave a terrestrial and user scheduling scheme based on the maximal performance for the ISUAVRNs in the presence of many terrestrial relays and many users.In[12],the ergodic capacity for the ISUAVRNs with a selection scheme and multiple terrestrial relays was researched.In[13],the OP was investigated for the ISUAVRNs with multiple users and an opportunistic user scheduling scheme.To enhance the spectrum efficiency and time utilization, a two-way relay technique is proposed for the ISUAVRNs[14].In[15],the OP was researched for the ISUAVRNs with hardware impairments(HIs)and the two-way terrestrial relay.In[16],the OP was analyzed for the ISUAVRs in the presence of many two-way terrestrial relays and a partial selection scheme.In [17], the OP was investigated for the considered ISUAVRNs with multiple terrestrial relays and an opportunistic selection scheme under the non-orthogonal multiple access scenario.However,due to the inherent characters of wireless communications particularly for the SatCom,the secrecy issue has been regarded as the major point for the SatCom[18].The physical layer security(PLS)is considered as the hopeful method to investigate the difference between the eavesdroppers’and legitimate channels,which is a popular research issue over recent years[19,20].In[19],a proposed beamforming(BF)scheme was utilized for the cognitive ISUAVRNs to enhance the secrecy performance.In [21], the authors researched the secrecy-energy efficient hybrid BF scheme for the ISUAVRNs.In [22], the non-ideal channel state information(CSI)and cognitive technology were both investigated for the secrecy ISUAVRNs along with secrecy performance.In practical systems,all nodes are not often ideal,which means they always suffer the I/Q imbalance, phase noise, and amplifier non-linearities [23-25], which results in the HIs in the transmission nodes.In [26], all the HIs issues are concluded, which leads to a general HIs model,widely utilized for many former works[27-31].Above all,to the authors’best effort,the investigation for the effects of two-way terrestrial relays on the secrecy ISUAVRNs with HIs is still not published,which motivates our paper.
From the former discussions, by considering the two-way UAV relay and an eavesdropper into our sight, we investigate the secrecy performance for the considered network.The contributions of this paper are presented in the following:
• By utilizing the two-way UAV relay and an eavesdropper into consideration,the framework for the secrecy ISUAVRN is founded.Besides,the decode-and-forward(DF)mode is used in the UAV to help the source to transmit the signals.Due to the heavy fading and other obstacle reasons, no direct link is assumed for the legitimate transmission link for the two sources.In addition,all the nodes are assumed to suffer from the HIs.
• Based on the considered system model,the detailed analysis for the secrecy outage probability(SOP)is obtained,which gives the easy method to investigate the SOP.Besides,these theoretical results can direct the engineering guide.
• To derive the further results of the system parameters on the SOP for the system,the asymptotic behaviors for the SOP are derived, which provide the secrecy diversity and order secrecy coding gain.
The remaining of this paper is shown in the following.A detailed illustration for the considered system is given in Section 2.The analysis for the secrecy OP is derived in Section 3.Some computer simulations namely Monte Carlo (MC) results are given in Section 4 to show the efficiency of the analytical results.The conclusion of the work is provided in Section 5.
Notations:|·|represents the absolute value of a complex scalar.E[·]is the expectation operator,C N (a,B)denotes the complex Gaussian distribution of a random vector a and covariance matrix B.Fy(·)andfy(·)represent the cumulative distribution function(CDF)and probability density function(PDF)the of random variabley,respectively.The abbreviations are given in Table 1.
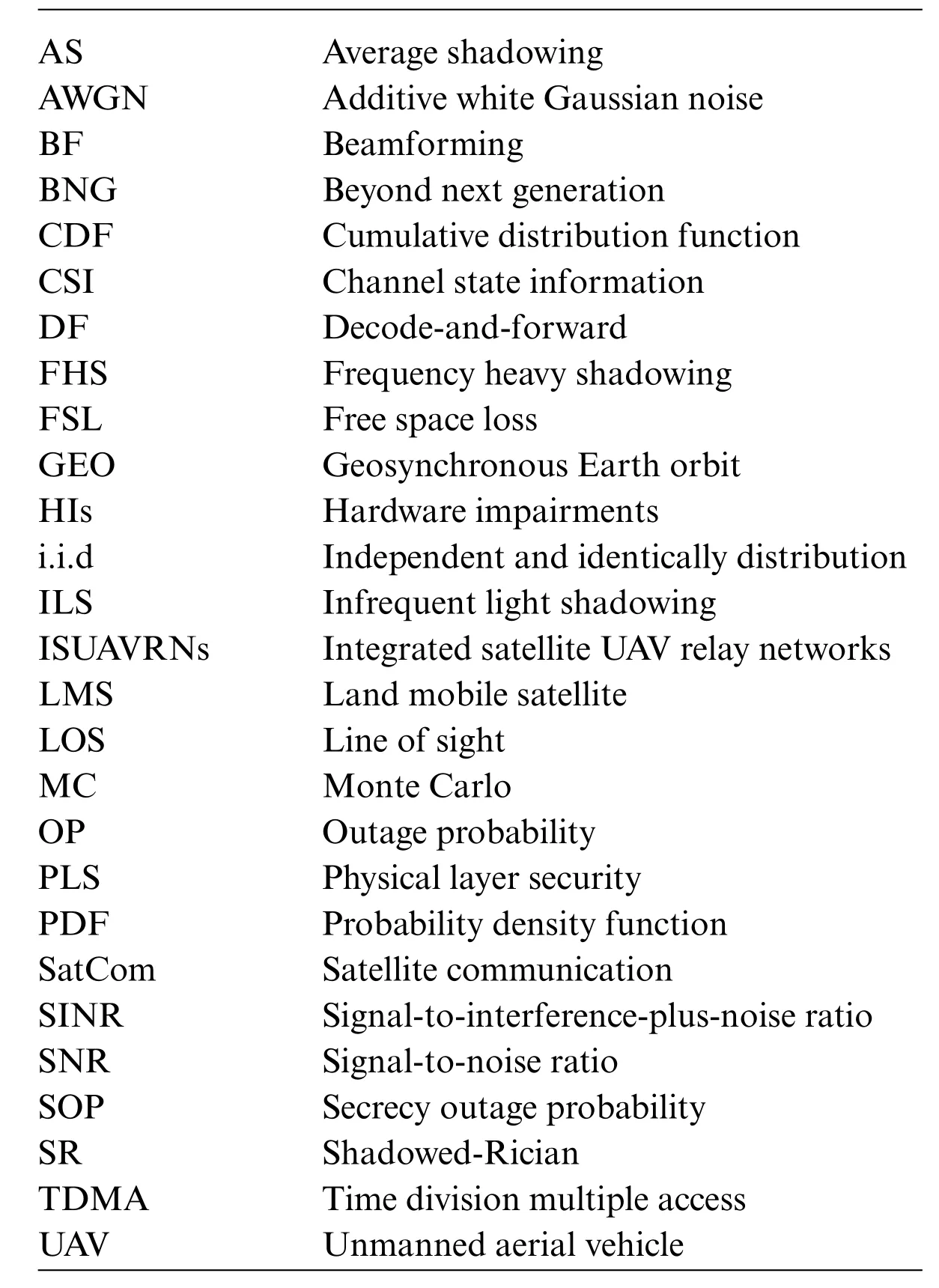
Table 1: Abbreviations
2 System Model
As plotted in Fig.1,we consider an ISUAVRN with HIs in this paper,which contains a satellite sourceS1, one terrestrial userS2, a two-way UAVRand an eavesdropperE.The two-way UAVRworks in DF mode.The whole nodes are considered to have one antenna and suffer from the HIs1We should know that,during this paper,only one antenna is assumed,however the derived results are still fit for the case with many antennas..At the same time,an eavesdropper UAVE2Although this paper just considers one eavesdropper,the derived results are still fit for the model with multiple eavesdroppers.Besides,the model with multiple eavesdroppers will be investigated in our near future.exist in the similar transmission beam withRand wants to overhear the transmission signals fromS1,S2andR.Due to the high building and the other reasons,no direct transmission link is considered between theS1andS2, which results in that the signal can only be transmitted byR3Owing to some reasons,direct transmission link between two sources is not available..
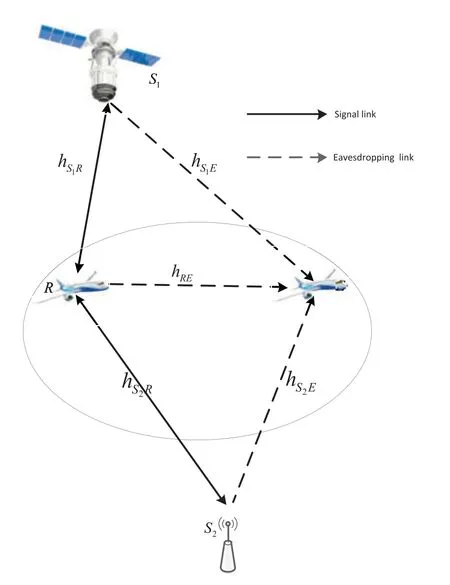
Figure 1:The system model description
It will use two time slots for the whole transmission.During the first time slot,S1andS2send its own symbols in the same time slot,i.e.,s1(t)withands2(t)withtoR,respectively.So,the obtained signal atRis shown as
wherePS1represents the transmitted power ofS1,PS2represents the power for theS2.hS1Rdenotes the channel coefficient for theS1→Rtransmission link with modeling as the shadowed-Rician (SR)fading.hS2Rrepresents the channel coefficient for theS2→Rlink with Rayleigh shadowing.As presented before, the transmission nodes suffer from the HIs;η1(t) andη2(t) denote the distortion noise due to HIs atS1andS2, respectively, which are shown asandη2(t) ~k1andk2represent the HIs level at theS1andS2, respectively [2].nR(t) represents the additive white Gaussian noise(AWGN)atRwith modeling as
SinceEandRare located in the same transmission beam,the overhear signal atEin the first time slot is shown as
whereySpE(t) represents the signal received atEfrom thep-th source,PSpdenotes thep-th source’s power,hSpEis the channel fading between thep-th source andEwith SR and Rayleigh fading,respectively.nE(t)denotes the AWGN atEwith modeling as
In the second time slot,owing to the utilized DF protocol,the UAV relay will use some techniques to decode the signals received and then re-transmit the re-encoded signal toSp,respectively.SinceSpknows their own signals,and they can know its signals and delete the self-interference,the obtained signal atSpis shown as
wherePRrepresents theR’s power,ηR(t) is the distortion noise which comes from the HIs withkRis the impairments’level atR[2].nSp(t)denotes the AWGN atSpwhich has the presentation as
As the same assumption,RandEare located in the similar transmission beam.Thus,the obtained signal atEin the second time slot is represented as
wherehRErepresents the channel coefficient betweenEandR,which is shown as Rayleigh fading.
By utilizing Eqs.(1)and(3),the obtained signal-to-interference-plus-noise ratio(SINR)atRfrom thep-th source is obtained as
The derived signal-to-noise ratio(SNR)atSpis given as
With the help of Eqs.(2)and(4),the obtained SNR atEis,respectively,obtained as
According to[32],the capacity for secrecy performance has the definition which is shown as the difference between the capacity of the legitimate users’channel and the eavesdroppers’channel.By utilizing Eqs.(5)-(9),the secrecy capacity for the considered network is represented as
3 Secrecy System Performance
The detailed analysis for the SOP will be obtained in this part.At first,the channel model for the transmission link is presented.
3.1 The Channel Model
3.1.1 The Terrestrial Transmission Link
The channel model for the terrestrial transmission link is modeled as independent and identically distribution(i.i.d)Rayleigh fading.From[33],the PDF and CDF ofγX,X∈{2S2R,RRE,RRS2,2S2E},are respectively derived as
3.1.2 The Satellite Transmission Link
The geosynchronous Earth orbit (GEO) satellite is taken for the analysis.In addition, we also consider the satellite having multiple beams for the considered system model.Particularly, time division multiple access (TDMA) [34] scheme is utilized in the considered model, which means that only one UAVRis suitable to forward the information signal at the next time slot.
The channel coefficienthV,V∈ {1S1R,1S1E,RRS1} between the downlink on-board beam satellite and UAV is presented as
wherefVrepresents the random SR coefficient,CVrepresents the effects of the antenna pattern and free space loss(FSL),which can be re-given by
whereλdenotes the frequency carrier’s wavelength,dis the length between UAV/eavesdropper and the satellite.d0≈35786 km represents the antenna gain for UAV/eavesdropper andGRerepresents the satellite’s on-board beam gain.
With help of[35],GRecan be written as
whererepresents the maximum beam gain at the boresight,andϑdenotes the angle of the offboresight.RecallingGV, by consideringθkas the angle between UAV/eavesdropper position and the satellite.In addition,represents the 3 dB angle of satellite beam.The antenna gain can be shown as[2,35]
whereGmaxpresents the maximal beam gain,uk=2.07123 sinθk/sin,K3andK1denote the 1st-kind bessel function of order 3 and 1,respectively.In order to gain best performance,thus,θk→0 is set,which leads toGV≈Gmax.Relied on this consideration,we derive
ForfV, a famous SR model was proposed in [36], which fits land mobile satellite (LMS)communication[2].By utilizing[36],the channel coefficientfVcan be re-given aswhere the scattering componentsfollows the i.i.d Rayleigh fading distribution whilerepresents the element of line of sight(LOS)component which obeys i.i.d Nakagami-mdistribution4It should be mentioned that,the SR channel is a famous channel model[8,10],which comes from the practical estimation date[37,38]..
With the help of[8],the PDF foris given by
Relied on Eq.(17)and utilizing[11],the CDF ofγVis re-derived as
3.1.3 Secrecy Outage Probability
From[18],the SOP defined as
whereC0=log2(1+γ0)withγ0defined as the target threshold.
ForS1→S2transmission link:
ForS2→S1transmission link:
From Eq.(22),the first consideration is to obtain the CDF forγS1Rand PDF forγS1E.The PDF forγ1S1Ehas been give in Eq.(17)withV=1S1E,thus utilizing the Eqs.(8)and(17),the PDF forγS1Ecan be re-written as
Then by utilizing Eq.(5),the CDF forγS1Ris re-written as
With the help of Eq.(17)withV=1S1Rand Eq.(11)withX=2S2R,then we can get
Then,after some mathematic steps,I1is re-given by
Next,with the help of[39],I2can be obtained as
Then,recalling Eq.(22),Eq.(22)can be re-written as
Then,it should be mentioned that in Eqs.(23)and(24),yshould be satisfied with the following condition, which isNext, by submitting Eqs.(23) and (24) into Eq.(28),Eq.(28)is rewritten as
However, try the authors’best efforts, it is too hard to obtain the closed-form expression of Eq.(29), then by utilizing [35] and utilizing the Gaussian-Chebyshev quadrature [40], by inserting Eqs.(24)and(23)into Eq.(29),it can be derived as
andN1being the number of the terms,denotes thel-th zero of Legendre polynomials,wlrepresents the Gaussian weight,which can be found in[40].
By utilizing the similar ways,the closed-form expressions for theandare respectively obtained as
andN2being the number of the terms,represents thev-th zero of Legendre polynomials,ϖvis the Gaussian weight,which is shown in[40],and
andN3being the number of the terms,represents the-th zero of Legendre polynomials,represents the Gaussian weight,which can be seen in[40],and
andN4being the number of the terms,represents theμ-th zero of Legendre polynomials,ξμdenotes the Gaussian weight,which has the definition in[40],andThen,by substituting Eqs.(30)-(33)into Eqs.(19)-(21),respectively.The closed-form expression for the SOP will be obtained,which is omitted here.
3.1.4 Asymptotic SOP
In what follows, the asymptotic behaviors for the SOP is obtained.When→ ∞,L∈{2S2R,1S1R,RRS1,RRS2}, then utilizingEqs.(30)-(33)will be obtained as
Then by substituting Eqs.(34)-(37)into Eqs.(19)-(21),the asymptotic expression will be derived.
Then from the final asymptotic SOP expression, the secrecy diversity order and secrecy coding gain are respectively derived as
4 Numerical Results
During this part,some representative MC simulations are provided to prove the efficiency of the theoretical analysis.Through these results,the impacts of channel parameters are evaluated.Without loss of any generality, we setandThe system and channel parameters are shown in Table 2[35]and Table 3[7],respectively.
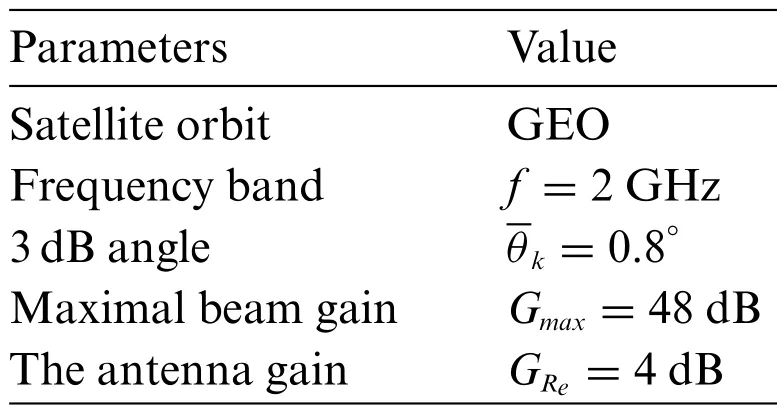
Table 2: System parameters

Table 3: Channel parameters
Fig.2 examines the SOPvs.for different shadow fading and impairments’ level with=0 dB andγ0=0 dB.From Fig.2,firstly,we can derive that the simulation results are tight across the theoretical analysis, which verify our analysis.In addition, in high SNR regime, the asymptotic results are nearly the same as the simulation results,which show the rightness of the analysis.Moreover,in this figure,it is very interesting that we find the SOP for AS scenario is lower than that of FHS,for the reason that when the channel suffers light fading,the system will have a better system performance.However,we find that the SOP for ILS scenario is the worst,which results in that when the channel is under ILS shadowing,the channel quality for eavesdropper is the best.In ILS scenario,the impact of channel quality on eavesdroppers is superior to that of legitimate users;thus the SOP is the highest.Finally,the lower hardware impairments’level leads to a lower SOP.
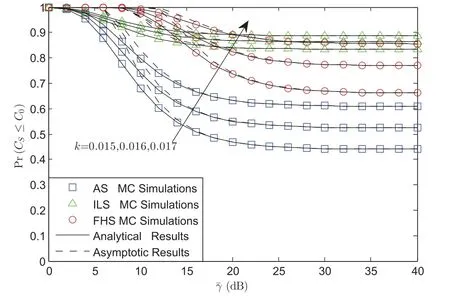
Figure 2:SOP vs. for different shadow fading and impairments’level with=0 dB and γ0=0 dB
Fig.3 represents the SOPvs.for differentand impairments’level under AS scenario.From this figure, we can find that the SOP with lowerwill lead to a lower SOP for the quality of the eavesdroppers gets better.For the reason that a more powerful eavesdropper will derive this phenomenon.
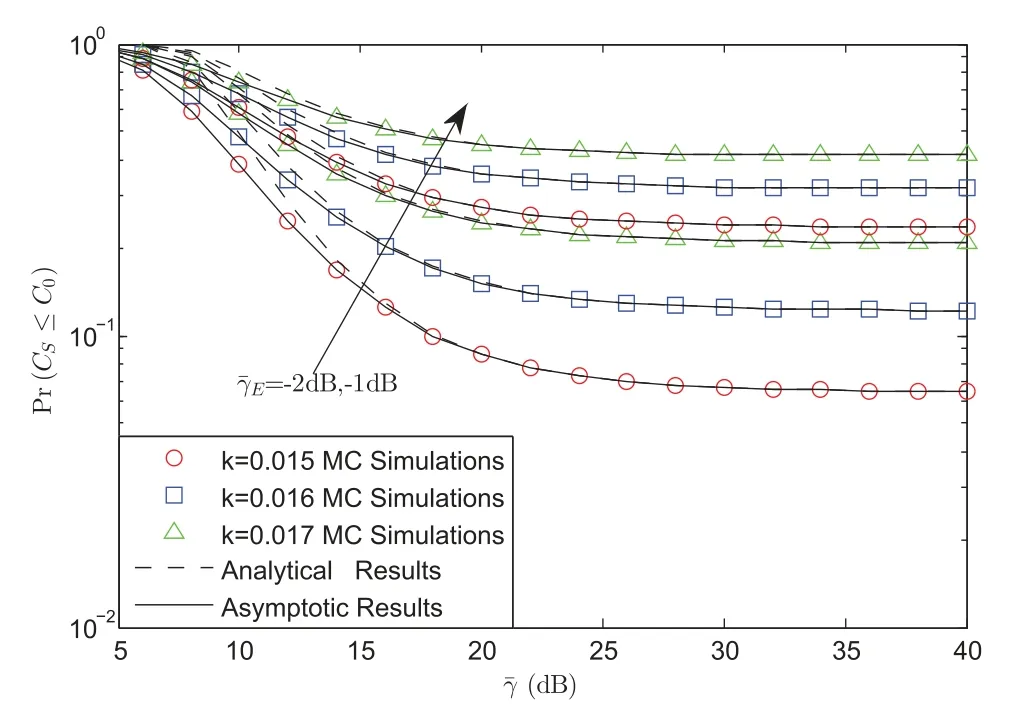
Figure 3:SOP vs. for different and impairments’level with γ0=0 dB under AS scenario
Fig.4 plots the SOPvs.γ0for differentand impairments’level under AS scenario.It can be derived that,the SOP will be always 1,which means the system is in outage state all the time when the threshold grows to the special value.It can be also seen that this value just has the relationship with the HIs level.In addition, we find that a lower HIs level will bring a larger value.At last, it can be derived that the value forhas no impact on this value.
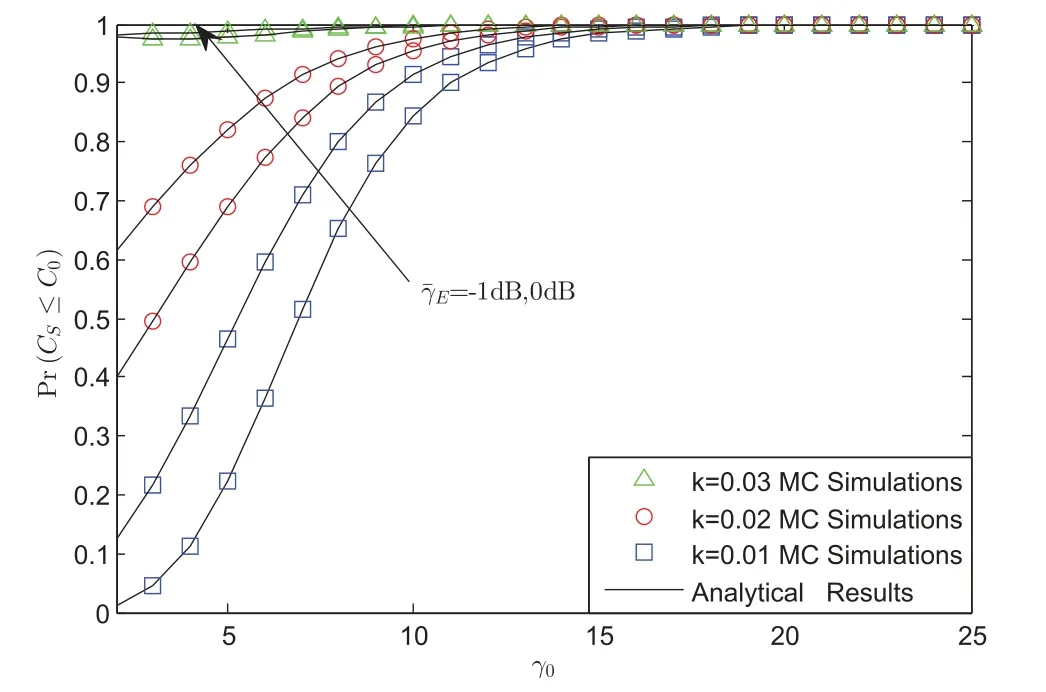
Figure 4:SOP vs.γ0 for different and impairments’level under AS scenario
5 Conclusions
This paper investigated the SOP for an integrated satellite UAV relay network with HIs.Especially,the closed-form and asymptotic behaviors for the SOP were derived.Firstly, it was derived that the SOP would have worse performance with threshold being larger;Secondly,it was found that the SOP would be larger with a larger;Thirdly,it was seen that the HIs’level had a great impact on the SOP.A larger impairments’level brought a larger SOP;Finally,the channel fading also influenced the SOP.
Acknowledgement:The authors wish to express their appreciation to the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding Statement:This work is supported by the Natural Science Foundation of China under Grant No.62001517.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
 Computer Modeling In Engineering&Sciences2023年6期
Computer Modeling In Engineering&Sciences2023年6期
- Computer Modeling In Engineering&Sciences的其它文章
- Finite Element Implementation of the Exponential Drucker-Prager Plasticity Model for Adhesive Joints
- A Review of Electromagnetic Energy Regenerative Suspension System&Key Technologies
- Arabic Optical Character Recognition:A Review
- Survey on Task Scheduling Optimization Strategy under Multi-Cloud Environment
- A Review of Device-Free Indoor Positioning for Home-Based Care of the Aged:Techniques and Technologies
- Topology Optimization for Harmonic Excitation Structures with Minimum Length Scale Control Using the Discrete Variable Method
