Optimization approach for a climbing robot with target tracking in WSNs
Jerwin Pru A Ahinv Tiwri
a Department of Robotics and Electronics Engineering, Bharati Robotic Systems, India
b Department of Robotics and Mechanical Engineering, Bharati Robotic Systems, India
Abstract Climbing robots are being developed for various applications. The confined space requires a compact locomotion system with vertical and overhead climbing ability. To achieve surface transition, Steering geometry Interaction system and static force are used. WSNs ubiquitous infrastructure and excellent coverage, they can be used for providing location information for various location-based services, especially in indoor environments. This structure is designed for a magnetic wall-climbing robot to gradually decrease the magnetic force when it is transiting between perpendicular magnetic surfaces. This paper describes the design process of a magnetic wall climbing robot, which adopts SgI and has the potential to carry materials in a confined space with an energy efficient system model. To resolve the problem of target tracking, it is essential to deploy a system model. Over the last two decades, several researchers have recommended many remote user authentication schemes. Researchers are continuously trying to enhance the security in material handling automation system by introducing several features into their work. A working prototype has been built based on the optimized dimension.
Keywords: Climbing Robot; Surface transition; Wireless Sensor Networks (WSNs); Target Tracking; Static Force; Steering Geometry Interaction (SgI).
1.Introduction
Security is the foremost concern in today's real-world application. Therefore, remote users can authenticate to the available services and get benefits easily. Authentication is one of the preliminary applications of WSNs. Climbing robots are useful machines that can be adopted in a variety of applications such as maintenance, building, inspection, Social Interaction, Entertainment and safety, mainly in the process and construction industries [1] . While Steering Geometry Interaction System (SgI) provides high positioning and turning accuracy in indoor environments, it faces significant issues in outdoor scenarios like uneven surface and different turning accuracy parameters. The confined and constrained space requires a compact locomotion system with vertical and overhead climbing abilities, as well as sufficient degree of mobility for moving inside several surveys classified and compared the performance of different locomotion strategies for confined space inspection robots [2-4] . A robot using RoboCran was proposed for ship hull. Similarly, a carriage-type robot was developed for double hull assembly line in shipbuilding[5] . However, these robots are bulky and not portable. In such case of node capturing, a sensor node under the threat vaporizes its memory contents and destructs itself and protects the valuable information from the attacker. WSNs is very useful in many real-life applications such as thread safety situations in the military, environmental, Robotics and other real-time applications as shown in Fig. 1 . An adversary may eavesdrop the channel and if possible, calculate the long-term session key and secret keys to make the entire protocol faulty. On the other hand, the alternative solution to indoor localization which utilizes ubiquitous Public land mobile networks can be quite beneficial, since the required network infrastructure and maintenance are, in most cases, readily available.

Fig. 1. The taxonomy of the WSNs applications.
However, the main drawback of the previously mentioned indoor positioning approaches is that they require the deployment of additional infrastructural elements in most indoor environments. The advantages of Hexagonal-Climber are its surface transition and turning-on-the-spot capabilities within a relatively small footprint. This paper firstly describes related work, Section 3 carries out static force analysis of SgI for different surface transition cases: horizontal-to-vertical and vertical-to-horizontal. The rest of the paper is organized as Section 4 focuses on system model, Section 5 elaborates the proposed system model and methods, Section 6 represents simulation and result in analysis, and finally, S ection 7 presents the conclusion of the work.
2.Related work
The use of space-partitioning has already proven to give good results regarding the outdoor positioning of mobile users in wide suburban areas. A two-wheeled mobile robot with seam tracking sensors was developed for shipbuilding [6] . The algorithm suggested by them works network operators can provide more accurate and stable positioning solution compared to the case when infrastructure from the single operator is used with low bandwidth ranges [7] . The wheel mechanism enables a gradual reduction of the magnetic force on the current surface while gradually increases the magnetic force on the target surface during the surface-to-surface transition.SgI enables the magnetic wheel directly touching the target surface. Therefore, the magnetic force is stronger than dual magnetic wheels. In 2010, Jiang, L G [8] developed Gait Analysis of a Novel Biomimetic Climbing Robot, which is an improvement from the wheel parallel to wheel mechanism.Kim et al. developed a robot, it can carry a payload equal to its own weight and can cling without consuming power [9] .Sensor nodes are resource stifled in nature and have restricted computational capability. Hossein Mousazadeh developed an Experimental evaluation of a hydrography surface vehicle in four navigation modes [10] . But, there also have some counter techniques that prevent the intruder from retrieving the data from the compromised nodes. Since the positioning model generally does not have a priori knowledge of base stations positions. This paper also adopts a multi-objective optimization technique to find the optimal dimension of the outer wheel and at the same time, trying to minimize the peak motor torque required for the surface transition and the weight.

Fig. 2. Orthographic projection of SgI: SgI consists of one magnetic wheel,outer wheel, gear and protector.

Fig. 3. Surface transition analysis of SgI (horizontal to vertical).

Fig. 4. Surface transition analysis of SgI (vertical to horizontal).
3. Optimization analysis for the surface transition process
The structure of SgI is depicted in Fig. 2 . It consists of a magnetic wheel tire, an outer wheel rim, a gear and a protective guard with multiple sensors for analyzing and decision making.
The surface transition between horizontal to vertical and vertical to horizontal surfaces is illustrated in Figs. 3 and 4 . It starts at the horizontal surface, where both the magnetic wheel and outer wheel is rotating. When the outer wheel touches the vertical wall, it stops rotating if the static frictional forces are sufficiently high.
In such a situation, the outer wheel will be stuck at the transition point. However, the magnetic wheel will continue to rotate as its attached spur gear [11] drives through the internal teeth of the outer wheel. The particular direction of the force acting normal to the magnetic wheel spur gear tooth surface.The outer wheel starts to rotate when the magnetic wheel is lifted further from the horizontal surface.
Ignoring friction force, if the transmitted torque ofiwheel isMiand the radius of the pitch isPi, then, the normal tooth surface loadFis expressed as:

4.Static force computational analysis of system model
The purpose of static force analysis is to compute the required motor torque for 2 main surface transition cases:(1) vertical-to-horizontal, (2) horizontal-to-vertical. Given the magnetic wheel, two stages are involved in the static force analysis: (1) computing the sliding coefficient on Target surface (Ts), when the wheel is being driven through the transition point; and (2) computing tangential gear force and required motor torque. The energy loss in the gearbox and gear chains are ignored in the analyses. This work considers receiver and transmitter for serial data transmission system between a server and robot Elambda= 40 per bit and amplifier dissipatesEmod= 90perbit/m2. The energy efficient system will transfer the data and the data saved to local server. It is a many-one mappingM: C1 → C2 where C1 = { 0, 1 }∗and C2 = { 0, 1 }n. The deterministic algorithm generates a fixed output of sizen, where the input is C1 and C2, where C1 ∈Aand C2 ∈B. TheTsis defined as Eq. (2) . IfTsis negative sign, sliding will happen on outer wheel during the surface transition. In this case, a higher friction coefficient is required to avoid surface transition failure [12] . Friction coefficient could be increased by knurling the wheels, coating a thin layer of rubber.

WhereMc1andMc2are friction coefficient on the original and target surface withEnEncoder positioning respectively.They are computed as follows for different surface transition cases. The surface transition between horizontal to vertical and vertical to horizontal surfaces friction coefficient calculation is illustrated in Figs. 5 and 6 . According to wheel movement, encoder and other sensor reading packet data will sent to server for analysis.
Case 1 (Horizontal-to-Vertical):
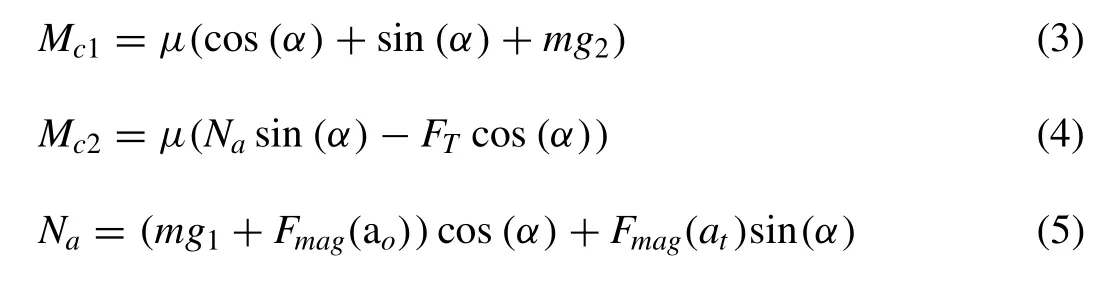

Fig. 5. Surface transition for horizontal-to-vertical.

Fig. 6. Surface transition for vertical-to-horizontal.
Case 2 (Vertical -to- Horizontal):
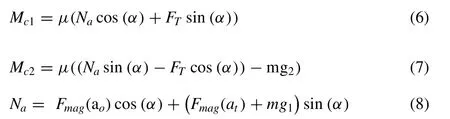
The magnetic wheel is pulling down by magnetic force(Fmag(ao)), inner diameter =Sid) at the biting point, which is a function of ao(the distance between the magnetic wheel and the original surface). The magnetic wheel is also pulled to the target surface byFmag(at),which is a function ofat(the distance between the magnetic wheel and the target surface and the wheel rotates αdegrees). Moreover, at the biting point, the magnetic wheel is pulled up by the tangential gear force (FT) and supported by reaction force (Na) and forceMc1. The surface area or the force of gravity affect the coefficient of friction only the two surfaces (mg1,mg2) that are in contact [13] . As it tends to rotate with respect to both walls,Mc1andMc2is preventing the rotation and calculating the movement using Encoder (En).Mc2is the reaction force, as the outer wheel tended to move against the target wall. The tangential gear force (FT) contact surface is illustrated in Fig.7 for surface transition cases and computed as:

Fig. 7. Illustration of gear contact surface.
Case 1 (Horizontal-to-vertical):

This suggests that once the magnetic wheel has been lifted up to the sign changing point, the magnetic force/gravity force on the target surface tend to pull the magnetic wheel to the target surface. Therefore, the motor torque is computed as:

To calculate the receiving and transmitting cost for transmitting a k-bit message [14] over a distance ‘d' are shown below:
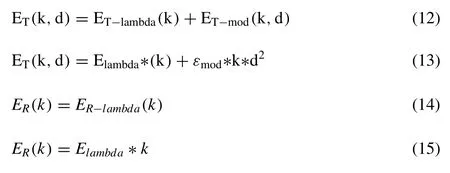
The important property of partitioning principle is the probability of correct space selection. As expected, the obtained results have shown that with the increase in the number of spaces, the probability of misclassification gradually increases. The particular target system model uses the coefficients ( Elambda, Emod, k ) which are used for calculating energy efficient system [15] . It saves the data lost by reducing distance ‘d' because the sensor will cover particular frequency distance, if the distance greater than actual distance then the data loss will happen, so solving this data loss it will calculate only particular distance, within that system it will sent continuous data.

Table 1 Algorithm for position estimation and transmitting data to the server.
5.Static Force computational analysis of system model
WSNs are normally generic and dynamic in nature. It means that the number of sensor nodes can vary in the network throughout its lifetime. Since sensor nodes are resource constrained in nature, they have limited computational power and eventually, some nodes may become faulty due to power drainage and hardware failure. Moreover, they can be physically destroyed or be stolen by an attacker. Kalman filter (KF)[16] and the complementary filter does linear filtering and uses data separation approaches to reduce the mean squared error while tracking a target with random motion with precise angles. As previously mentioned, in this research, partitions are made strictly on geometrical bases, without considering building's inner (logical) structure. Particle Filtering is appropriate for nonlinear and non-Gaussian dynamic systems. The proposed algorithm for position detection and signal handling data to server station is described in Table 1 . Regardless of the data loss issues, the addition of nodes is highly desirable and has to be limited within the mentioned security protocols of the WSNs. A registration phase is initiated when a node is added to the network. After successful registration,the user initiates authentication with the newly added sensor node. The network remains in working mode and undisturbed during the entire process of node addition, registration and authentication. However, this is the subject of a further research.
Before things get started, the authorized person needs to fix the environment using a setup server. The phase runs offline where each regular sensor nodeSjis provided with an identity and a pre-shared key, generated randomly and stored securely in the memory of position data as well asSj. This method supports network shared memory control by multihop transmission [17] for Websocket connectivity to avoid the data mismatch. Our design facilitates nodes to be dynamically appended to the system without provoking any alterations in the established security states. As sensor nodes are resource stifled and having restricts limited computational capability,they can eventually stop operating due to energy drainage or hardware malfunction. For every sensor node added in the network, a new registration phase is initiated and the node is added to the network. It further computes the login request packet is given by ( 16 ). The userUichoosesIDias identity and seleted proper codexjit will sent the sends the registration request message.

Fig. 8. Tracked path of the target.

When a node gets connected, at last, the values ofUiandIDiis stored inxjmemory. A registration phase is initiated when a node is added to the network. After successful registration, the user initiates authentication with the newly added sensor node. The network remains in working mode and undisturbed during the entire process of node addition,registration and authentication. In the verification part of the registration and authentication phase, the timestamp values will be different due to modification by the attacker. Suppose, the modified time authentication values areA3c,A4c}. NowAxc/ =Ax,Ax= { 1 , 2, 3 , 4 } . As a result, authentication will be aborted and further any sort of communication will be denied. The operation achieved by 17.

The pictorial representation of sensor node registration with the gateway. As sensor nodes are resource stifled and having restricted limited computational capability, they can eventually stop operating due to energy drainage or hardware malfunction. For every sensor node added in the network, a new registration phase is initiated and the node is added to the network, the sensor nodes and communication nodes are coordinated by an algorithm [18] . Therefore, nothing is required to do a change in the structure of the scheme.
6.Result and discussion
The target is prepared and validated on the boundary of the sensor network and sending theINFO_TO_WSpacket, the data is transmitted to the server station using the generated path as shown in Fig. 8 . Moreover, our design presents a greater level of protection and functionality features while minimizing computational cost and storage cost. As a result,the attacker is unable to retrieve the secret values stored in them. Since nodes can be added dynamically, some malicious nodes can be destroyed without disturbing, an emergency stop will start.

Fig. 9. Perspective view.
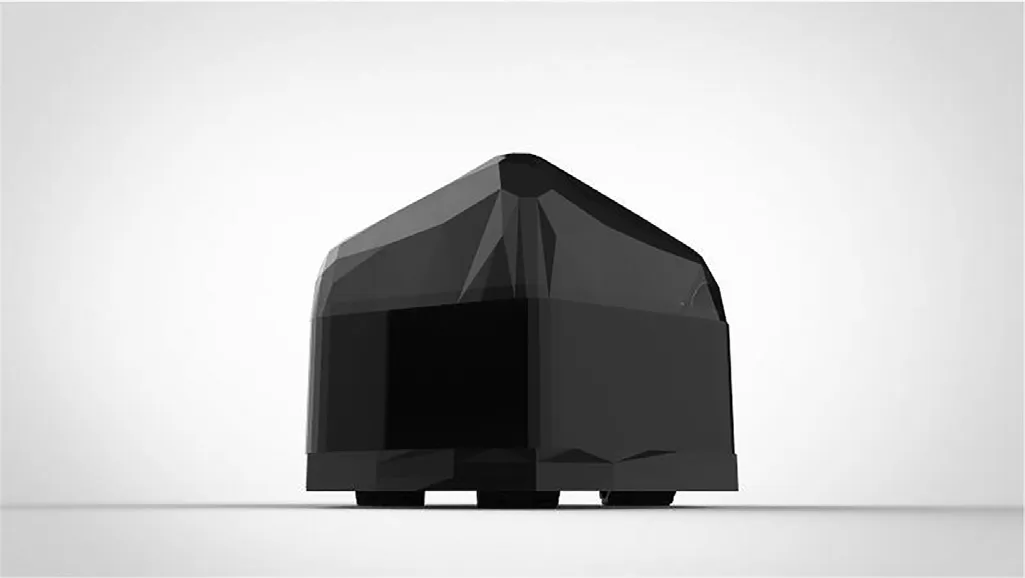
Fig. 10. Prototype model.
We consider the authentication phase because most of the operations are performed in this particular phase. We calculate the overhead incurred by the sensor nodes and the gateway node but the main focus is given on the computation performed by the sensor node since it is resource constrained in nature and have limited computational power. We now consider the cost of messages exchanged from one principal agent to another in the different phases of our authentication process. The aim is to exploit the network lifetime of a power measured wireless sensor network. A prototype called “Hexa-Climber”was developed based on the data obtained from the various analyses. From the encoder installed on each motor,the velocity of each motor is closed-loop controlled.
The experiment in Fig. 9 illustrates its surface transition ability for the critical cases and hexa-climber arrangement.This wheel mechanism enables a gradual reduction of the magnetic force on the current surface while gradually increases the magnetic force on the target surface during the surface-to-surface transition. As a result, dual magnetic wheel enables a smoother surface transition compared with the conventional magnetic wheels which may get stuck at the transition point. For safety and security purpose electrical emergency stop connected with the system. It starts on a horizontal surface (climbs a vertical wall ( Fig. 10 shows Hexa-Climber model. The magnetic force is strong enough to hold the robot on vertical and overhead positions.
7.Conclusions
The performance of the scheme confirms that the storage overhead has been reduced significantly requiring very less amount of memory overhead. Many climbing robots have been developed to assist human operators in the confined or dangerous environment. After analyzing the state-of-the-art obstacle crossing problems for the magnetic wheel is driven robots, it was found that SgI is a promising wheel structure to enable a climbing robot to transit between surfaces and carry a relatively high payload. The developed position and target tracking algorithm are efficient to track the particular running target in the sensor network and transmit the real-time data to the server station. Multi-objective optimization was adopted to find the optimal dimension of the outer wheel and at the same time, trying to minimize the peak motor torque and the weight of the outer wheel for the surface transition. A working prototype was built based on the optimized dimension and its performance was evaluated.
 Journal of Ocean Engineering and Science2018年4期
Journal of Ocean Engineering and Science2018年4期
- Journal of Ocean Engineering and Science的其它文章
- Development of current-induced scour beneath elevated subsea pipelines
- The effect of gravity and inclined load in micropolar thermoelastic medium possessing cubic symmetry under G-N theory
- New analytic solutions of the space-time fractional Broer-Kaup and approximate long water wave equations
- Efficient numerical scheme based on the method of lines for the shallow water equations
- Comparing the force due to the Lennard-Jones potential and the Coulomb force in the SPH Method
- Iterative algorithm for parabolic and hyperbolic PDEs with nonlocal boundary conditions
