EIAS:An Efficient Identity-Based Aggregate Signature Scheme for WSNs Against Coalition Attack
Yong Xie,Fang Xu,Xiang Li,Songsong Zhang,Xiaodan Zhangand Muhammad Israr
Abstract:Wireless sensor networks (WSNs)are the major contributors to big data acquisition.The authenticity and integrity of the data are two most important basic requirements for various services based on big data.Data aggregation is a promising method to decrease operation cost for resource-constrained WSNs.However,the process of data acquisitions in WSNs are in open environments,data aggregation is vulnerable to more special security attacks with hiding feature and subjective fraudulence,such as coalition attack.Aimed to provide data authenticity and integrity protection for WSNs,an efficient and secure identity-based aggregate signature scheme(EIAS)is proposed in this paper.Rigorous security proof shows that our proposed scheme can be secure against all kinds of attacks.The performance comparisons shows EIAS has clear advantages in term of computation cost and communication cost when compared with similar data aggregation scheme for WSNs.
Keywords:Wireless sensor networks(WSNs),big data,signature aggregation,efficiency,coalition attack.
1 Introduction
With the rapid development of information technology,various new significant services continuously spring up,such as cloud computing [Sookhak,Gani,Khan et al.(2017)],social networks [Su,Xu and Qi (2016)],and Internet of things [Sun,Song,Jara et al.(2016)].To provide better services,a great deal of data are gathered by cameras,sensory nodes,sound recorders,information-sensing mobile devices,software logs and so on[Botta,De Donato,Persico et al.(2016)].Wireless sensor networks(WSNs)are the major contributors to data acquisition for more and more exciting network services based on big data.
WSNs are consisted of a large number of sensor nodes that integrated senor model,data processing model and wireless communication module.The sensor nodes can achieve various of data monitors,such as temperature,humidity,noise and light intensity,atmospheric pressure,trajectory of moving object and soil composition and so on,by embedding a variety of sensing devices.The primary goal of WSNs system is to acquire a large number of real-time data from sensors and store all data in a data center,then provide all manner of services based on the big data.Therefore,the nodes in WSNs are self-organized into a large-scale unattended intelligent or semi-intelligent distributed network system through multi-hop communication [Mahmood,Seah and Welch (2015)].Nowadays,WSNs have very broad application prospects in environmental monitoring(such as transportation,living area,safety monitoring),industrial inspection(such as work flow control,equipment diagnosis),key infrastructure assurance (such as power grids,water conservancy,fire monitoring),process control in hazardous areas.The powerful data acquisition and processing potential of WSNs have been highly valued by the military,academia and industry in many countries,therefore,WSNs possess important scientific research and practical value.However,as a new type of large-scale self-organization system,there are many challenges in WSNs,from the physical layer signal modulation and wireless receiving and sending technique,to the media access technology of data link layer and error control mechanism,to the data routing protocol of transport layer and so on[Li,Tryfonas and Li(2016)].
Because the true sensing data is the basic guarantee for realizing various complex data application services,the factual collection,secure transmission and secure storage of sensing data are the core goal of implementing the WSNs tasks [Rashid and Rehmani(2016)].To realize true sensing data transmission,more and more scholars have devoted themselves to design secure authentication protocols for WSNs.However,unlike traditional networks,WSNs possess an inherent characteristics of resource constraint and design limitation,such as low band width,short communication distance,limited energy,processing and storage.Therefore,it is a great challenge to design secure and efficient authentication protocol for WSNs for their limited resources [Di Pietro,Guarino,Verde et al.(2014)].
To address the problems caused by the limited resources,Boneh et al.[Boneh,Gentry,Lynn et al.(2003)]proposed a general aggregate signature scheme in 2003.This scheme allows anyone to generate a short aggregate signature by combining multiple signatures from different users,which can reduce nodes? energy consumption during data transmission.Since then,aggregate signature has been widely researched for its unparalleled advantage in decreasing communication cost and energy consumption.As with other communications technologies,security issue is an unavoidable issue for data aggregation,some special security attacks with hiding feature and subjective fraudulence become more threatening,such as coalition attack.Coalition attack means that attackers use one or more invalid single signatures together with other valid signatures to construct a valid aggregate signature[Bellare,Micciancio and Warinschi(2003)].Obviously,coalition attack can subtly destroy the validity and integrity of aggregated messages,and breach the security requirements of aggregate signature schemes.Therefore,to design a secure and efficient data aggregation scheme that is secure against coalition attack is of great significance to WSNs.
1.1 Motivations and contributions
Aimed to decrease the energy consumption and ensure data integrity during data transmission,we proposed a secure identity-based aggregate signature scheme (EIAS)for WSNs in this paper.The proposed scheme can achieve data integrity protection,user authentication and data aggregation by combining multiple signatures that signed on sensing data from different sense nodes into one single short aggregate signature.Hence,the proposed scheme not only could protect data integrity,but also can decrease communication cost and storage cost for WSNs.In summary,the proposed scheme has four major contributions as follows.
First,we present a system model for WSNs with data aggregation function.The data cluster nodes can authenticate sensing data from sensor nodes and aggregate them into one message before sending them to the data center,as shown in Fig.1.

Figure 1:A typical structure of aggregation signature system in WSNs
Second,we present an efficient and secure identity-based aggregate signature scheme(EIAS)by using elliptic curve cryptosystem,which has efficient message signing algorithm,message verification algorithm and data aggregation algorithm.
Third,based on elliptic curve discrete logarithm problem under random oracle model,a rigorous security proof is presented to show that EIAS can resist all kinds of security attacks(included coalition attack)and ensure data integrity,which achieves the key safeguard for superior service based on WSNs.
Four,the detailed performance comparisons between EIAS and Shenet al.'s recently proposed scheme [Shen,Ma,Liu et al.(2016)] is presented in this paper.The results show that EIAS have clear advantages in computation and communication cost during the data collection and delivery.
1.2 Organization of the paper
The rest of this paper is arranged as follows.Section 2 introduces the related works that proposed recently.Section 3 introduces the preliminaries demanded in this paper and Section 4 shows the system model and security requirement.Next,we propose identity-based aggregate signature scheme for WSNs in Section 5.The security proof and analysis are presented in Section 6.The performance comparisons are discussed in Section 7.At last,conclusion and future work are drawn in Section 8.
2 Related works
In recent years,data security and data integrity are two key issues in data gathering of WSNs,and have received a considerable research attention [Kumari,Khan and Atiquzzaman(2015)],and many related security schemes have been presented for WSNs.There security schemes have their own advantages in different core applications.However,most of them have different security vulnerabilities and are not able to achieve certain security requirements under some known or unkown attacks [He,Zeadally,Kumar et al.(2017)].Das [Das (2009)] presented a password-based authentication scheme by using smart card for WSNs.However,this scheme was proven to be vulnerable to Dos attack and capture attack.Based on this work,some improved security schemes[Turkanovic and Holbl(2013);Yuan(2014);Chen and Shih(2010)]have been presented.To overcome the deficiency of Das[Das(2009)],Das et al.[Das,Sharma,Chatterjee et al.(2012)]proposed an improved two factors password-based authentication scheme for hierarchical WSNs.Unfortunately,It has been pointed out that its implementation is infeasible in practical applications [Turkanovic and Holbl (2013)].Xue et al.[Xue,Ma,Hong et al.(2013)]proposed a temporal-credential-based mutual authentication scheme for gateway nodes in WSNs.But Li et al.[Li,Weng and Lee(2013)]pointed that Xue et al.'s scheme is subject to identity guessing attack,tracking attack,privileged insider attack and weak stolen smart card attack,and then presented an improved scheme.Jiang et al.[Jiang,Ma,Lu et al.(2015)]also proposed an improved message authentication scheme with unlinkability over Xue et al.'s[Xue,Ma,Hong et al.(2013)]scheme.However,Jiang et al.'s scheme[Jiang,Ma,Lu et al.(2015)]was demonstrated that has several drawbacks,such as suffering from privileged insider attack and failing to provide proper authentication.In order to eliminate those drawbacks,Das[Das(2016)]proposed an improved three-factor user authentication scheme over Jiang et al.'s scheme.Turkanovic et al.[Turkanovi´c,Brumen and Hölbl(2014)] presented a lightweight key agreement protocol for heterogeneous WSNs.But soon later,Changet al.[Chang and Le (2016)] demonstrated that Turkanovic et al.'s[Turkanovi´c,Brumen and Hölbl (2014)] scheme cannot be secure against stolen verifier attack,impersonation attack,spoofing attack and so on.To eliminate security pitfalls,Chang et al.[Chang and Le (2016)] proposed two schemes,one is efficient scheme overcoming the weaknesses of Turkanovic et al.'s[Turkanovi´c,Brumen and Hölbl(2014)]scheme,the other is an improved scheme over the former which can provide perfect forward secrecy with less modification.However,Chang et al.'s scheme is vulnerable to session key breach attack and session specific temporary information attack.Amin et al.[Amin and Biswas(2016)]proposed an authentication and key agreement scheme for WSNs with a novel architecture.But it can not be secure against tracking attack and achieve user untraceability [Jiang,Zeadally,Ma et al.(2017)].To solve this deficiency,Jiang et al.[Jiang,Zeadally,Ma et al.(2017)]proposed a secure user authentication protocol by using Rabin cryptosystem.However,all of the above mentioned schemes focus little on data aggregation and reducing communication overhead for WSNs.
Since Boneh et al.[Boneh,Gentry,Lynn et al.(2003)] proposed a general aggregate signature scheme in 2003,data aggregation technology has been widely used for WSNs.Without doubt,the security issue of data aggregation technology is an unavoidable issue in WSNs.Recently,researchers have proposed plenty of aggregate signature scheme for WSNs [Wen,Ma and Huang (2011);Zhang and Zhang (2009);Liu,Zhu,Ma et al.(2014);Zhang,Hu,Wu et al.(2016)].Wen et al.[Wen,Ma and Huang (2011)] used bilinear pairings to constructed an aggregate signature scheme based on specified verifier.Hartung et al.[Hartung,Kaidel,Koch et al.(2016)] proposed a new fault-tolerant aggregate signature scheme by fixed number of messages in one aggregate signature.Zhang et al.[Zhang,Wu,Domingo-Ferrer et al.(2017)] proposed an identity-based aggregate signature scheme with privacy-preserving for VANETs,and this scheme provides hierarchical aggregation and batch verification to decrease communication cost.Tang et al.[Tang,Liu,Zhao et al.(2018)] proposed an aggregate signature scheme by using trust routing,in which the trust routing takes is difficult in deployment.However,it is a pity that the above mentioned schemes have one or more security flaws,especially can not secure against coalition attack[Shen,Ma,Liu et al.(2016)].As mentioned earlier,coalition attack can destroy the validity and integrity of aggregated messages.
3 Preliminaries
3.1 Elliptic curve cryptosystem(ECC)
Elliptic curve in cryptography is firstly proposed by Miller [Miller (1984)] in 1984.Soon later,based on the difficulty of elliptic curve discrete logarithm problem (ECDLP),Koblitz [Koblitz (1987)] presented an ECC instance.From then on,many cryptographic protocols and secure schemes is designed by using ECC because of its effectiveness in both computation cost and communication cost.The ECC is defined as following.
Letpis a large prime number,Fpis defined as a finite field determined byp.Based on equationy2=x3+ax+bmodp,E/Epis a set of elliptic curve point overFp,wherex,y,a,b ∈Fp,(4a3+27b2)mod0.Point Θ at infinite and all point onE/Epconsist of a additive groupGp.Gpsatisfy the following essential properties[Liu,Guo,Fan et al.(2018)].
Point addition:AssumePandQbe two points ofE/Epand,a line joiningPandQwill intersectE/Epat a point-R.IfP=Q,a line joiningPandQwill be a tangent line ofE/Ep.Point subtraction:AssumePandQbe two points ofE/EpandQ=-p,the two point subtraction is express asP+Q=P -P=Θ,i.e.the line joiningPandQwill intersectE/Epat a infinite point Θ
Scalar point multiplication:AssumePbe a point ofE/Ep,mpointP's addition is defined as scalar multiplication,i.e.,m·P=P+P+···+P(mtimes),where,m ∈Zp,m >0.Order of group:Assumen >0,m ∈Zp,we callnis the order of groupGpifnis smallest number that makesn·P=Θ,
3.2 Complexity assumptions
In this subsection,the computational hard problem related to ECC is described as follows.Elliptic curve discrete logarithm problem (ECDLP):Given two random pointP,Q ∈E/Ep,Q=α · P,to calculateαfromQfor unknownα ∈RZ∗p.The probability for a probabilistic-polynomial-time (PPT)adversaryAto solve the ECDLP problem isThe hardness is that theAdvECDLPAto solve the ECDLP problem is negligible in polynomial time.
3.3 Identity-based cryptography
The identity-based cryptography was introduced by Shamir in 1984[Shamir(1984)].The identity-based cryptography can ease key management problem because the public key certificate is no longer needed.In the identity-based cryptography,each unique identity information of the users,such as identity number,email address and telephone number,can be used to generate their identical public key.The private key generator(PKG)is charge of generating and issuing the private key of each user according to its identical public key.The signature system using identity-based cryptography is called identity-based signature(IBS)system,in which signature verification only needs public parameters,signer's identity and signature pair.Thus,there is no longer requires certificates in IBS system.
4 System model and security model
4.1 System model
Wireless sensor networks(WSNs)are widely used in various fields,so system models are changed due to application requirements.According to Shen et al.[Shen,Ma,Liu et al.(2016);He,Zhang,Gu et al.(2017)],we can analysis the system model of WSNs in this paper from two aspects:roles and data.
Roles:According to Shen et al.[Shen,Ma,Liu et al.(2016);He,Zhang,Gu et al.(2017)],the system model of WSNs in this paper is considered to be consisted of four network roles,i.e.,Key Generation Center (KGC),Sensor nodes,Cluster nodes and Data Center.There are other relay roles,such as transfer stations,that only need to relay messages without authentication or aggregation.
·KGC:The KGC is in charge of generating system parameters and generating the identity key for each sensor node.The KGC is assumed to be infeasible to compromise by any adversaries.And the KGC is also assumed as a trusted role and can be trusted by all roles.
·Sensor Nodesbf:Sensor nodes are in charge of obtaining sensing and sending data to data center via cluster nodes and other relay role,such as transfer stations.Before sending data,sensor nodes should make signatures on the data.
·Cluster Nodes:Cluster nodes are in charge of signature verification and aggregation.Cluster nodes authenticate data from sensor nodes,then aggregate signatures into one aggregate signature,finally send the aggregated message to the data center via other relay roles.
·Data Center:The data center is in charge of verifying aggregated messages and storing the data.
Data:The sensory data are the core of various of services based on WSNs.Generally speaking,the data in WSNs includes the sensing data,acquisition time and other related information.To protect data integrity and authentication,sensing data must be signed.The data that have been signed by sensor nodes can be divided into two type in term of signature:One is valid data that their signature can pass verification,the other is invalid that their signature cannot pass verification.
In WSNs,the data flow from data generation to storage can be illustrated as follows:Sensor nodes periodically collect sensory data,then add acquisition time and other information to the data,then make a signature on the data.Next,sensor nodes send the signed message to the cluster nodes.Upon receiving messages from sensor nodes,cluster nodes verify the signatures then aggregate these signatures,then send the aggregated message to data center via other relay roles.Other relays roles in the systme only relays messages without verification or aggregation.The data flow is illustrated in Fig.1.
4.2 Security model
Security requirements in WSNs mainly are integrity,authenticity,availability and flexibility,etc.In our system model,our main concern is the data integrity protection during the data collection and delivery process under the premise of improving the verification efficiency and reducing the communication cost [He,Kumar and Chilamkurti (2015)].Therefore,providing message authentication,being secure against modification attack,data tampering attack,impersonation attack,relay attack are the main security requirements for the security system in WSNs[Liu,Zhong,Chang et al.(2016)].
According to the network model of WSNs system and the definitions of adversary? ability,we define the security model by a game played between a challengerCand adversaryAunder the random oracle model for the proposed scheme.In the game,the adversaryAcan ask for any queries as follows.
Initialization-Oracle:In this query,the challengerCwill generate the public parameters and the private key of the system.ThenCsends the pubic parameters to the adversaryA.h-Oracle:WhenAmakes this kind query,Cselects a number Υħ∈RZ∗q,and sets a tuple(Δ,Υħ)into Oralc-ListhLand answersAwith Υħ.
Sign-Oracle:WhenAmakes this query with message{datai},Ccreates a reply message{σi,Ri,Ui,IDi,datai}toA.
In this game,Acould break the signature scheme∇only if it can forge a valid request message.Assume(A)is the probability thatAcan break the signature scheme∇in this game.
Definition 1A signature scheme for WSNs can be determined to be secure if the probability(A)is negligible for any PPT adversaryA.
5 The proposed scheme(EIAS)
In this section,we present an Identity-based signature scheme with message aggregation by using ECC.The proposed scheme no longer needs any bilinear paring operations.The proposed scheme consists of five phases:system initialization phase,identity key generation phase,message signing phase,message aggregation phase and aggregation verification phase.For simplicity,the notations and corresponding descriptions are listed in Tab.1.

Table 1:Notations used and Description
Next,the five phases are described as following subsections.
5.1 System initialization phase
In this phase,the KGC is in charge of generating system parameters.First,the KGC defines the security parameterλ(such as security level on 80 bits),then selects an elliptic curveEp(a,b)defined by equationy2=x3+ax+bmodp,wherepis a large prime,a,b ∈Fp,and then selects a pointPonEp(a,b)as a generator of groupGwith orderq,whereGis a point set including all point on and the point at infinity Θ.Next,the KGC selects a keys ∈Z∗qas its private secret key,and calculatesPpub=sPas its public key.Next,it selects three secure hash functions,h1:G × {0,1}∗→Zq,h2:as cryptographic hash function used in scheme.At last,the KGC publics system public parametersparas={Ep(a,b),p,q,P,h1,h2,h3,Ppub}.
5.2 Identity key generation phase
In this phase,the KGC generates the identity key for each sensor node.Assume current sensor node's identity withIDi∈{0,1}∗is in the registration process,the KGC selects a random numberui∈Z∗q,and computesUi=uiP,ξi=h1(Ui,IDi),si=ui+ξis.At last the KGC sends{Ui,si}as identity keyIDkeyto the sensor nodeIDiin a secure way.
5.3 Message signing phase
When the sensor nodes have obtained sensing data.Assume a node with identityIDihasdatai.The node selects a random numberri∈Z∗q,computesRi=riP,ρi=h2(Ri,Ui,IDi,datai),σi=si+ρiri.Then the nodeIDisends message{σi,Ri,Ui,IDi,datai}to the cluster nodeIDj.
5.4 Message aggregation phase
In this phase,the cluster node authenticates messages from sensor nodes,then aggregates these authenticated messages into one aggregated message,finally sends the aggregated message to the data center.
·Message verifying
On receiving a message{σi,Ri,Ui,IDi,datai},the cluster nodeIDjcomputesξi=h1(Ui,IDi),ρi=h2(Ri,Ui,IDi,datai),then verifies it satisfies the verification equation Eq.(1).

If not,IDjdeclines the message{σi,Ri,Ui,IDi,datai}.Else,IDjaccepts.Becauseσi=si+ρiriandsi=ui+ξis,the correctness of verification equation(1)can be proved as the following:

Therefore,the verification equation(Eq.(1))is correct.
·Message aggregation After receivingnmessages{σ1,R1,U1,ID1,data1},{σ2,R2,U2,ID2,data2},···,{σn,Rn,Un,IDn,datan},the cluster nodeIDjcan aggregate these messages for saving communication cost and computation cost for later delivering and verification.It computesand sendsas the aggregated message to the data center.
5.5 Aggregation verification phase
When the data center receives the aggregated message{σj,{Rjk,Ujk,IDjk,datajk}k={1,2,···,n}}from the cluster nodeIDj,it computes each message in the aggregated messages asξi=h1(Ui,IDi),ρi=h2(Ri,Ui,IDi,datai),Then it checks whether the following aggregation verification equation(Eq.(2))holds or not.

If holds,it accepts these messages.Or,it drops these messages.
Becauseσi=si+ρiri,si=ui+ξis,λj=h3(U1+ξ1Ppub+ρ1R1,U2+ξ2Ppub+andt he correctness of verification equation(Eq.(2))can be proved as the following:
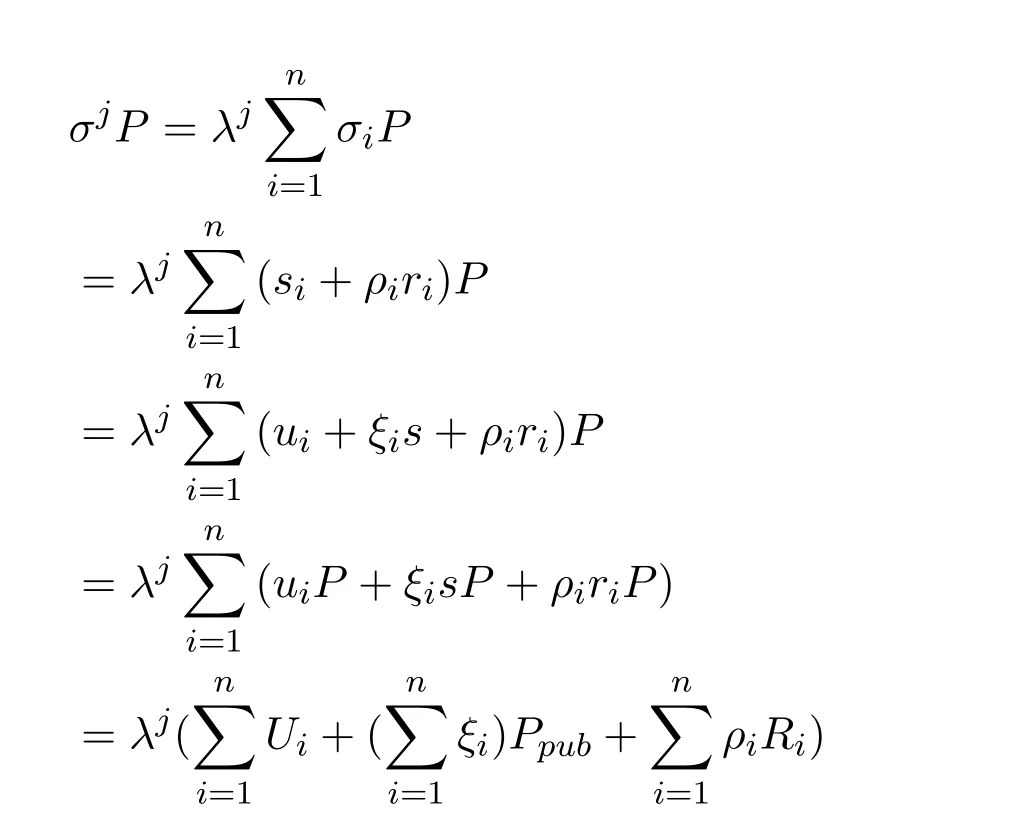
Therefore,the verification equation Eq.(2)is correct.
6 Security proof and analysis
In this section,we firstly present the security proof that the proposed scheme (EIAS)is secure against adaptive chosen ciphertext attacks,then we demonstrate that EIAS can satisfy the security requirements of WSNs system.
6.1 Security proof
In this subsection,the proposed identity-based signature scheme for WSNs is assessed on the security under the random oracle model.
Theorem 1The proposed scheme is existentially unforgeable against an adaptive chosen-message attack under the random oracle model.
Proof.Assume an adversaryAcan forge a signature{σi,Ri,Ui,IDi,datai}on the sensordatai.Let(P,Q=xP)be an ECDLP instance for two random pointPandQonE/Ep.Ccan solve the ECDLP problem with non-negligible probability by runAas subprogram.Initialization.The challengerCruns system initialization procedure,definesPpub=Q=xPas system public key,and obtainsparas={Ep(a,b),p,q,P,h1,h2,h3,Ppub},and sets two oracle-lists.The two lists arehL1with form of<Ui,IDi,τ1>andhL2with form of<Ri,Ui,IDi,datai,τ2>respectively.hL1consists of the queries and answers ofh1-Oracle.hL2consists of the queries and answers ofh2-Oracle.The two lists are empty at their initialization.At last」sends params toA.
h1-queries.WhenAmakes this query with message{Ui,IDi},Cchecks if the tuple<Ui,IDi,τ1>is inhL1.If so,Csendsτi=h1(Ui,IDi)toA.OrCselectsτ1∈RZ∗q,then adds<Ui,IDi,τ1>tohL1.Finally,CanswersAwithτ1.
h2-queries.WhenAmakes this query with messages<Ri,Ui,IDi,datai>,Cchecks if the tuple<Ri,Ui,IDi,datai>is inhL2.If so,Csendsτ2=h2(Ri,Ui,IDi,datai)to
A.OrCselectsτ2∈RZ∗q,then adds<Ri,Ui,IDi,datai,τ2>tohL2.Finally,CanswersAwithτ2.
Sign-queries.WhenAmakes this query with messagedatai,Cchoosesσi,ξi∈RZ∗p,computesUi=σiP -ρiRi-ξiPpub,thenCadds<Ri,Ui,IDi,datai,σi>tohL2,nextCanswersAwith{Ri,Ui,IDi,datai,σi}.
According to the designation of EIAS,all theA's answers to the Sign-queries are valid:message{Ri,Ui,IDi,datai,σi}could meet the signature verification equation(Eq.(3)).
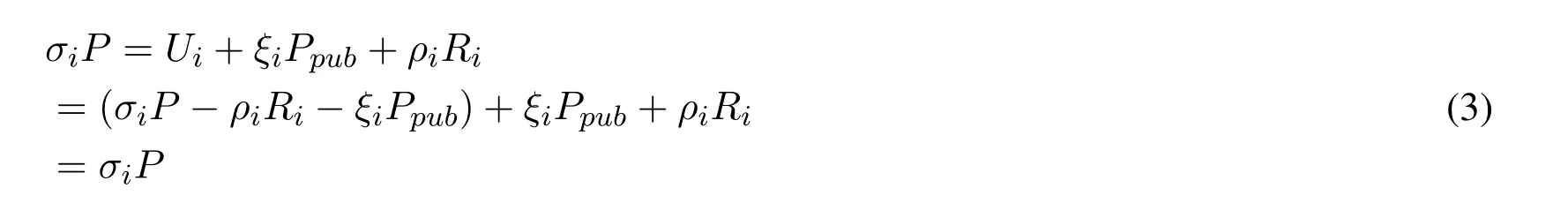
Output.At last,Acan output a message{Ri,Ui,IDi,datai,σi}in non-negligible probability.the message can be verified by Eq.(4).

If not hold,Cabandons the current game.
On the basis of the forgery lemma[Pointcheval and Stern(1996)],another valid message{Ri,Ui,IDi,datai,σ∗i}can be generated ifAdoes a repetition of the game by using anotherξ∗i.Under these circumstances,this message can meet equation(Eq.(5)).

It can deduce a new equation with Eq.(4)and Eq.(5)as following.

From Eq.(6),we could obtain equation Eq.(7).

Therefore,Ccan solve the instance of the ECDLP problem by the output of Eq.(7)(i.e.,(δi-δ∗i)·(ξi-ξ∗i)-1).But,it is in contradiction with the hardness hypothesis of ECDLP problem.Therefore,it can draw a conclusion that EIAS is secure against adaptive chosen message attack under random oracle model.
Theorem 2Assumeh3is a collision resistant hash function,the aggregate signature of EIAS is secure and valid only on the condition that each individual signature is valid.
Proof.Assume the aggregate signatureσjis a valid,thenλjcan be calculated byλj=and the aggregation verification equation is held as following.
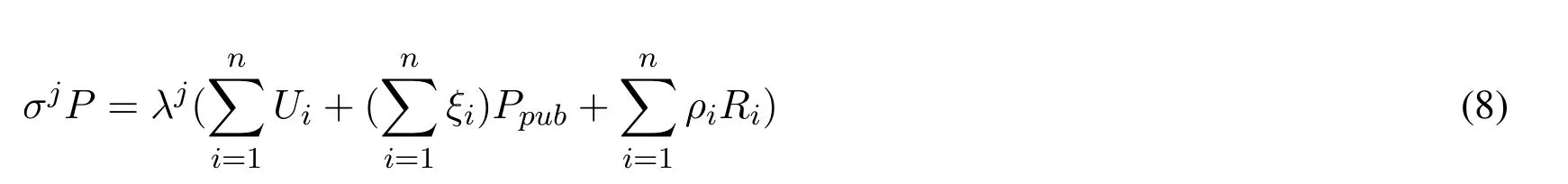

From Eq.(9),it can derive the following equation.

wherei=1,2,···,n.Therefore,it illustrates that each signatureσiin thenmessages is valid.
Next,we analyze the validity of the aggregate signature fromnvalid single signature.If thensignature{σ1,R1,U1,ID1,data1},{σ2,R2,U2,ID2,data2},···,{σn,Rn,Un,IDn,datan}are valid,we can getσi=si+ρiri,si=ui+ξis,λj=h3(U1+ξ1Ppub+
Then the aggregation verification equation(Eq.(2))can be deduced as following.

Therefore,the aggregate signatureσjis proved to be valid.
If an adversary modifies the aggregate signature with one invalid message{R∗i,U∗i,ID∗i,data∗i}instead of one valid message,it is impossible to make the sameλjaccording toh3's collision resistance.That is,the modified aggregate signature cannot satisfy the aggregation verification equation(Eq.(2)).
Through the above security analysis,we can draw a conclusion that the aggregate signature is valid only on the condition that each individual signature is valid.
6.2 Security analysis
In this subsection,the security requirements are analyzed on the basis of Theorem 1.
·Message authentication:When receives a message{Ri,Ui,IDi,datai,σi},the cluster node can check its validity and integrity according to Eq.(1).If Eq.(1)is hold,it proves the message is valid according to Theorem 1.Therefore,EIAS for WSNs can satisfies the security requirement of message authentication.
·Modification attack:If a adversary has modified the message{Ri,Ui,IDi,datai,σi}as{R∗i,U∗i,ID∗i,datai,σ∗i},the cluster node can easily distinguish the invalid message{R∗i,U∗i,ID∗i,datai,σ∗i}because it cannot make the verification equationσiP=Ui+ξiPpub+ρiRitrue.Therefore,EIAS is secure against modification attack.
·Impersonation attack:In EIAS,when an adversary impersonates a sensor node to send a message{R∗i,U∗i,ID∗i,data∗i,σ∗i}to the cluster node.According to Theorem 1,the probability of that the forged message{R∗i,U∗i,ID∗i,data∗i,σ∗i}can pass the verification equation Eq.(1)can be negligible.Therefore,EIAS is secure against impersonation attack.
·Relay attack:As definition of the system model,the sensor nodes add the current time intodataiwhen they generate the sensing data.If an adversary relay an outdated message{Ri,Ui,IDi,data∗i,σi}with modified time indata∗i,the modified time can pass the check on time freshness,however the message can not meet verification equationσiP=Ui+ξiPpub+ρiRiaccording to Theorem 2.Therefore,EIAS is secure against relay attack.
7 Performance comparison
In this section,we present the performance comparison among EIAS and Shen et al.most recently proposed scheme (SE-IAS for short) in term of computation cost and communication cost.
To evaluate performance fairly and objectively,we construct the two authentication schemes on the security level of 80 bits. As SE-IAS uses bilinear pairing,we construct its cryptographic operations as following: A bilinear pairing:G0×G0→G1.G0is an additive group,is its generated point on a super-singular elliptic curve:y2=x3+xmod,is it order.is a 512-bit prime-number,= 2159+217+1 is a 160-bit Solinas-prime-number. As EIAS are ECC-based authentication scheme,we construct its cryptographic operations as following:Gis an additive group on a non-singular elliptic curveE:y2=x3+ax+bmodp,its generated point isP,its order isq,wherea,b ∈ Z∗qandp,qare two 160-bit prime number. We implement the corresponding cryptographic operations on the following environments:hardware is formed by an Intel-i3 3110M processor,clock frequency is 2.40 GHz,and memory is 4 GB,operation system is windows 7. The execution times of these cryptographic operations are shown in Tab. 2.The names of cryptographic operations is abbreviated as column Abbr. in Tab. 2.

Table 2:The execution time of cryptographic operations
According to the definitions of these cryptographic operations,the size ofis 64 bytes andpis 20 bytes.Therefore,the element inG0is 128 bytes and the element inGis 40 bytes.We define the sizes of an identity of node and a one-way hash function result as 10 bytes and 20 bytes respectively.
7.1 Computation cost comparison
In this subsection,EIAS is compared with SE-IAS scheme in terms of computation cost.For simplicity,let Identity Key Generation Phase,Message Signing Phase,Message Aggregation phase and Aggregation Verification Phase be abbreviated asIKP,MSP,MAPandAVPrespectively during later analysis.
As far as Shen et al.'s SE-IAS,the computation cost inIKPconsists of one Map-To-Point function operation and one scalar multiplication operation related to the bilinear pairing,therefore the total execution time ofIKPis 1TH+1TPM;the computation cost inMSPconsists of two scalar multiplication operations related to the bilinear pairing,one point addition operation related to the bilinear pairing and one Map-To-Point function operation,therefore the total execution time ofMSPis 2TPM+TPA+TH;the computation cost fornmessages inMAPconsists of 4npairing operations,nMapToPoint function operations,one scalar multiplication operation related to the bilinear pairing,(n-1)point addition operations related to the bilinear pairing,and one one-way hash function operation,therefore the total execution time ofMAPis 4nTBP+nTH+(n-1)TPA+1TPM+1Th;the computation cost fornmessages inAVPconsists of (2n+1)pairing operations,nMapToPoint function operations,4nscalar multiplication operation related to the bilinear pairing,npoint addition operations related to the bilinear pairing,and one one-way hash function operation,therefore the total execution time ofAVPis (2n+1)TBP+4nTPM+nTH+1Th.
As far as EIAS,the computation cost inIKPconsists of one scalar multiplication operation related to the ECC and one one-way hash function operation,therefore the total execution time ofIKPisTEM+Th;the computation cost inMSPalso consists of one scalar multiplication operation related to the ECC and one one-way hash function operation,therefore the total execution time ofMSPisTEM+Th;the computation cost fornmessages inMAPconsists of 3nscalar multiplication operations related to the ECC,(3n-1)point addition operations related to the ECC,and (n+1)one-way hash function operations,therefore the total execution time ofMAPis 3nTEM+(3n -1)TEA+(n+1)Th;the computation cost fornmessages inAVPconsists of (n+5)scalar multiplication operation related to the ECC,(2n+2)point addition operations related to the ECC,and(n+1)one-way hash function operations,therefore the total execution time ofAVPis(n+5)TEM+(n+1)Th+(2n+2)TEA.
The total execution time ofIKP,MSP,MAPandAVPin SE-IAS and EIAS can be calculated according to Tab.2.The results are shown in Tab.3.
As shown in Tab.3,the computation cost time of SE-IAS inIKPandMSPare 3.975 ms and 6.630 ms.However,the computation cost time of EIAS inIKPandMSPare both 0.754 ms,which can decrease by 81% and 88% when compared with the time of SE-IAS.The computation cost comparisons inIKP,MSP,MAP( aggregating 50 messages)andAVP(verifying aggregate signature with 50 messages)illustrated in Fig.2 and Fig.3,which can vividly show that our proposed scheme takes a large advantage on computation cost over SE-IAS scheme.

Table 3:The computation cost comparison of the two schemes

Figure 2:The computation costs of theIKP andMSP phase in the two schemes
The Fig.4 demonstrates the computation costs for aggregating or verifying different number of messages in MAP andAVP.Where,MAP of SE-IAS demonstrates the computation cost for aggregating different number of messages inMAPof the SE-IAS scheme,AVPof SE-IAS demonstrates the computation cost for the data center to verify different number of messages inAVPof the SE-IAS scheme,MAPof EIAS and AVP-IAS have similar meaning with the former two.As shown in Fig.4,EIAS is more efficient than SE-IAS scheme regardless of the number of messages.
In summary,compared with SE-IAS scheme,EIAS has much lower computation cost in each phase than AVP-IAS.
7.2 Communication cost comparison
Next,the communication cost is analyzed between EIAS and Shen et al.'s SE-IAS in this subsection.

Figure 3:The computation costs of theMAP andAVP phase in the two schemes

Figure 4:The computation costs of MAP and AVP for different number of messages
According the previous analysis,the sizes of,p,G0,Gand one-way hash function result have been defined as 64 bytes,20 bytes,128 bytes,40 bytes and 20 bytes respectively.We define the sizes of an identity of node and a one-way hash function result as 10 bytes and 20 bytes respectively.For simplicity,the data in messages is not considered in the communication cost comparison because it is the same to every scheme.
As far as EIAS:The message sent by sensor node to cluster node consists of{σi,Ri,Ui,IDi,
datai},which includes two elements inG(Ri,Ui∈G,40×2 bytes),one identity(IDi,10 bytes)and one hash function's output(σi∈Zq,20 bytes).Therefore,the size of message is 110 bytes;The aggregated message(Assume aggregatekmessages)sent by cluster node to the data center consists ofwhich includes 2×kelements inG(Ri,Ui∈G,40×2×kbytes),kidentities(IDi,10×kbytes)and one hash function's output(σi∈Zq,20 bytes),therefore,the size of aggregated message is 90×k+20 bytes.As far as SE-IAS:The message sent by sensor node to cluster node consists of{Ui,Ti,IDi,datai},which includes two elements inG0(Ti,Ui∈G0,128×2 bytes)and one identity (IDi,10 bytes),therefore,the size of message is 266 bytes;The aggregated message (Assume aggregatekmessages)sent by cluster node to the data center consists ofwhich includeskelements inG0(Ti∈G0,128×kbytes),kidentities (IDi,10 bytes)and one elements inG(U ∈G0,128×1 bytes).Therefore,the size of aggregated message is 138× k+128 bytes.Tab.4 shows the communication cost comparison results of a message sent by a sensor node to a cluster node and a aggregate message (50 messages are aggregated)sent by a cluster node to the data center.In the former process,EIAS has decreased by 43% compared with SE-IAS.In addition,EIAS has decreased by 35%compared with SE-IAS during the later process.The communication cost of the aggregate message in the two schemes(EIAS and SE-IAS)can be illustrated in the Fig.5 as thekchanges.It vivid shows that EIAS has very obvious advantages than SE-IAS in decreasing communication cost.As a result,EIAS incurs much lower computation and communication cost than SE-IAS,and is more suit for the WSNs environment.
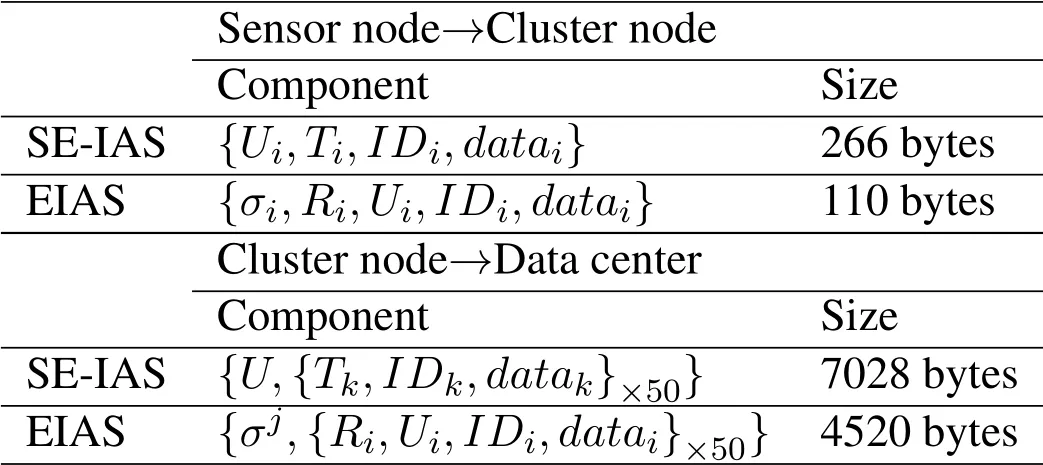
Table 4:The comparison of communication cost
Tip:The size ofdataiis excluded in the comparison.

Figure 5:The computation costs of MAP and AVP for different number of messages
8 Conclusion and future work
WSNs are the major contributors to big data acquisition,but data acquisition cannot be played optimally because nodes are limited in computation and power.Therefore,to design secure and efficient signature schemes for data collection and aggregation in WSNs is very urgent.To solve this issue,we propose a new and efficient identity-based data aggregation authentication scheme in this paper.The proposed scheme constructs data aggregation signature using ECC,and it decreases the computation costs in message signing phase,message aggregation phase and aggregation verification phase and does not use any complex bilinear pairing operation,which is very suitable for resource-restricted WSNs environment.The security proof and analysis show that our proposed scheme meets the security requirements for WSNs data integrity protection,and is secure against forgery attack,coalition attack and other security attacks with hiding feature and subjective fraudulence.The performance comparison demonstrates EIAS has clear advantages in term of computation cost and communication cost when compared with similar data aggregation scheme for WSNs.
Although EIAS is more efficient and secure than similar schemes,lightweight signature scheme is more favored.Therefore,to design secure lightweight signature aggregation scheme is our next work.
Acknowledgement:The work was supported in part by the National Natural Science Foundation of China (61572370),and the National Natural Science Function of Qinghai Province (2019-ZJ-7065,2017-ZJ-959Q),the MOE (Ministry of Education in China)Project of Humanities and Social Sciences (17YJCZH203)and the Natural Science Foundation of Hubei Province in China(2016CFB652).
 Computers Materials&Continua2019年6期
Computers Materials&Continua2019年6期
- Computers Materials&Continua的其它文章
- Development of Cloud Based Air Pollution Information System Using Visualization
- A Learning Based Brain Tumor Detection System
- Shape,Color and Texture Based CBIR System Using Fuzzy Logic Classifier
- LRV:A Tool for Academic Text Visualization to Support the Literature Review Process
- Application of Image Compression to Multiple-Shot Pictures Using Similarity Norms With Three Level Blurring
- On Harmonic and Ev-Degree Molecular Topological Properties of DOX,RTOX and DSL Networks
