Quantum watermarking based on threshold segmentation using quantum informational entropy
Jia Luo(罗佳) Ri-Gui Zhou(周日贵) Wen-Wen Hu(胡文文)YaoChong Li(李尧翀) and Gao-Feng Luo(罗高峰)
1College of Information Engineering,Shanghai Maritime University,Shanghai 201306,China
2Research Center of Intelligent Information Processing and Quantum Intelligent Computing,Shanghai 201306,China
3College of Information Engineering,Shaoyang University,Shaoyang 422000,China
Keywords: quantum image watermarking,threshold segmentation,quantum informational entropy,quantum circuit
1. Introduction
Quantum information processing is an interdisciplinary study that combines information science and quantum physics.The essence of quantum information processing is solving complex problems according to properties of quantum mechanics,which are difficult for classical methods.The most famous application of quantum computing may be the quantum integer factoring algorithm proposed by Shor and Grover’s algorithm for search of databases. The former can break the widely used RSA scheme in polynomial time, the latter can achieve quadratic speedup compared to the best classical algorithm.[1]Nowadays,other sub-disciplines complement the content about quantum information processing.[2]These subdisciplines include an emerging realm, quantum image processing (QImP), which focuses on using quantum computing to solve conventional image processing tasks.
QImP started in 1997,at that time Vlasov[3]proposed an analogue image recognition method of quantum systems.This was followed by Schutzhold’s investigation of problems of linear patterns in unstructured picture.[4]In 2003,Beachet al.[5]demonstrated that common quantum algorithms are appropriate for image processing tasks,which is generally considered to be the beginning of today’s description of QImP.Then,various models of how to store digital images in a quantum computer are proposed, such as qubit lattice,[6]real ket,[7]flexible representation of quantum images (FRQI),[8]a novel enhanced quantum representation of digital images (NEQR),[9]and a representation method for multidimensional color images, called ann-qubit normal arbitrary superposition state(NASS).[10]
Based on these models, the research of QImP has entered a fruitful stage.[11]Various types of quantum image processing tasks have been explored including quantum image scaling,[12-14]recognition,[15]edge detection,[16-18]segmentation,[19,20]and information hiding. A major thrust of current research is the quantum information hiding,[21]which is branched out into two fields, i.e., quantum image watermarking[22-25]and quantum image steganography.[26-30]Their purpose was to conceal secret message in a cover image without causing visual changes,so one must validate the proposed algorithm by some image quality measures. Many researchers are satisfied with employing the peak noise-to-signal ratio(PSNR)to evaluate similarity between quantum images.Moreover,probability-based image similarity measure was researched in Refs. [31,32], and wholly quantum-based image fidelity metric was also discussed in Refs.[33,34].
The scope of this paper is to propose a watermarking scheme based on threshold segmentation using quantum informational entropy. The threshold selection method we shall refer to belongs to the maximum entropy threshold of gray level distribution. The relative deficiency of von Neumann entropy for a pure state impels us to employ the quantum informational entropy proposed in Ref. [35]. The main idea of our scheme is to embed information to the object and the background with different ways using the key obtained by the threshold segmentation of the cover image. Therefore,after the secret message is embedded, the target pixels can be changed less and the normal use of the image will not be affected. Finally, we define a method to measure the similarity of cover image and embedded image using entropy difference.
2. Quantum informational entropy
In quantum information theory, information is stored in the basic unit, the qubit or quantum bit. The most distinct property of a qubit is the existence of superposition, which means that a qubit can be a coherent superposition of both states simultaneously. In classical systems, however, a bit must be in one state or another. Obviously, the storage and processing of information in classical or quantum systems are quite different.
In a quantum system, the measure of informational entropy is also more complex than the classical system. It makes a big difference whether the measurement is adopted in pure or mixed quantum state. In a pure-state quantum system, the state is a coherent superposition of the basis states|0〉and|1〉,which can be described by a point on the surface of Bloch sphere.A mixed state is a statistical combination or incoherent mixture of different pure states, and its entropy can be computed by the von Neumann entropy. However, according to the principle of von Neumann entropy, the entropy of a pure state is always zero.[35]
For the quantum representation of image, for example,the NEQR model is written as
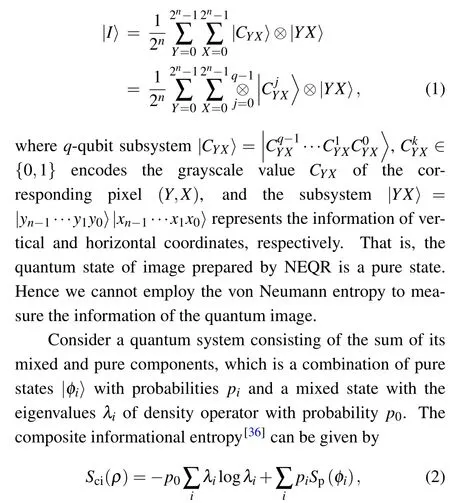

Thus, when we consider the case that there is no mixed state and the probability of pure state|φ〉is 1, this happens to be the state of quantum image,the informational entropy of quantum image|φ〉can be calculated by Eq.(3).The measurement experimental results of the grayscale value of every pixel can demonstrate the amplitude ofq-qubit subsystem. This makes it possible to simplify the representation of the quantum image to measure the quantum informational entropy of image:
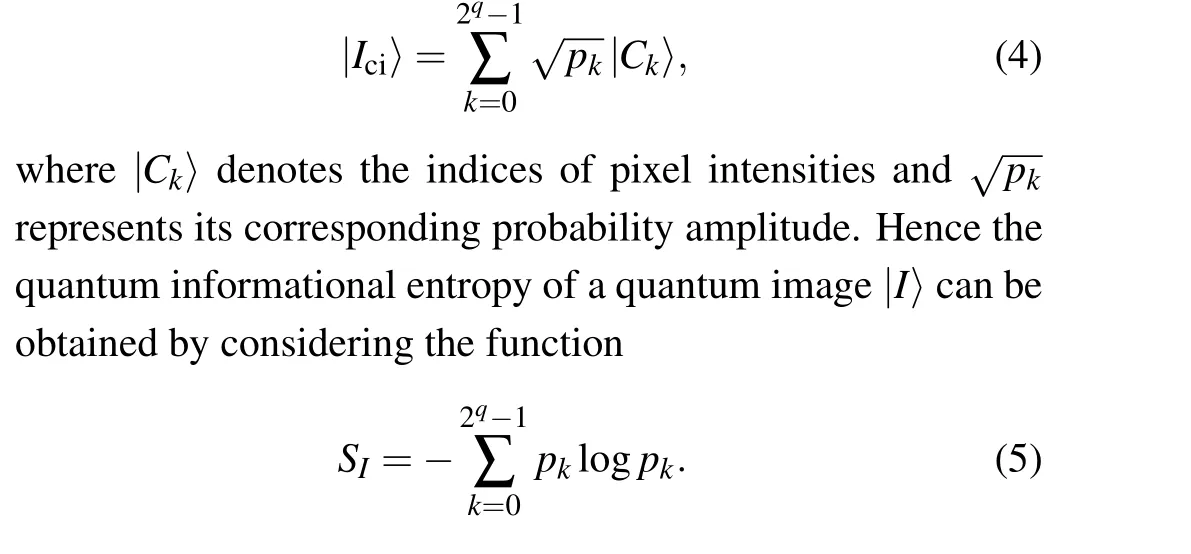
3. Thresholding segmentation
Thresholding is a process in which an appropriate threshold that transforms all the levels to black or white is selected under some criteria, so as to extract objects from a background.[37]Thus, the pixels of an image are divided into a series of classes according to the following rules:

Let us define the sum of the entropies of all classes by Eq.(10). Then we maximizeφ(S)to obtain the maximum information between objects and background distributions in the image,and the set of valuestjis the threshold.
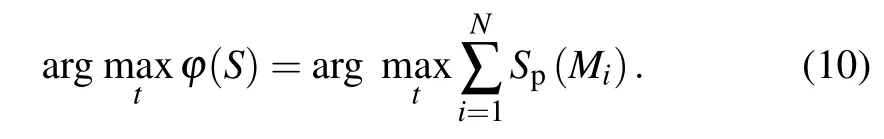
For this study,we assume that only one object is extracted in the image. Now we derive from amplitudes of two categories,one defined for intensity level from 0 tot1and the other for intensity level fromt1+1 to 2q-1. Consequentlyφ(S)to be the discriminant criterion of threshold,we have the relation
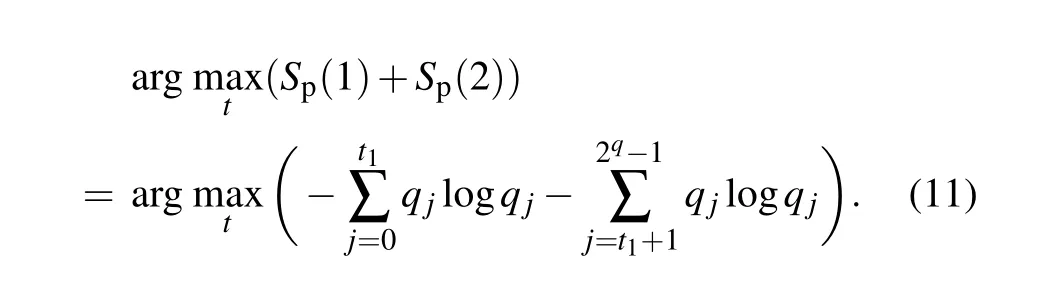
According to the methods mentioned above,the quantum image threshold procedure is shown in Algorithm 1.
4. Watermarking scheme
As discussed above,having computed the threshold value of the quantum image, it can be used in the segmentationbased watermarking process in order to find a suitable authentication key. In this section, we will show how the key is prepared. Then the proposed scheme and algorithms for the embedding phase and the extraction phase are described detailedly.
4.1. Authentication key
The information is embedded to cover image using the authentication key that is later used for the recovery process too. As we can see in Section 3,the thresholdtderived from the quantum informational entropy is acquired. On this basis,the authentication key is prepared as follows:
Step 1 Consider a cover image and calculate the thresholdt.
Since the authentication key is determined by the object and background of the cover image, we need choose a cover image firstly. Then, by adopting Algorithm 1, the thresholdtof partitioning the image to two parts is obtained.
Step 2 Depending on the threshold,one can construct the authentication key.
In order to embed the information using the key, it must be first constructed it into a Boolean-valued one. Let us define a Boolean functionB,whose mathematical formula is
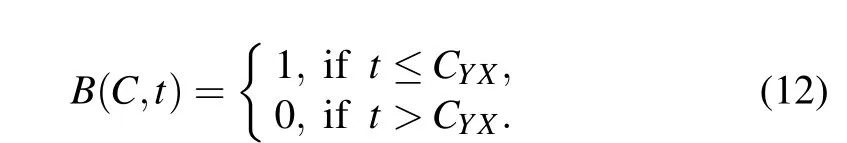
For a given gray valueCYX,the Boolean value of 1 represents that this pixel belongs to object. Similarly, the Boolean value of pixel to be 0 represents the background.
After applying the Boolean function to all the pixels in the cover image,the authentication key|Key〉is formed as follows:
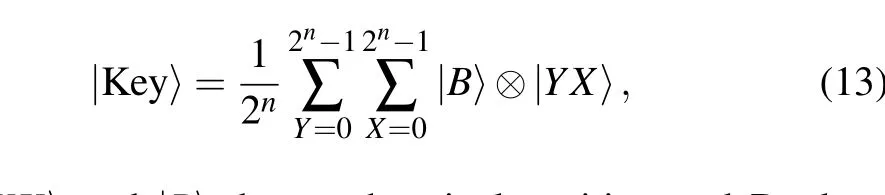
where|YX〉and|B〉denote the pixel position and Boolean value,respectively.
4.2. Embedding procedure
We can summarize the steps required to embed the watermark information onto a cover(original)image into two parts:
(1)The compound step,which is combining the cover image,the information image and the authentication key.
(2) The watermark embedding circuit generation step,wherein the appropriate embedding circuit is designed to realize the content of embedding algorithm.
In the former part of the procedure, the main consideration is the combination of subsystems about color information.Assume that the secret information is a binary image and defined as
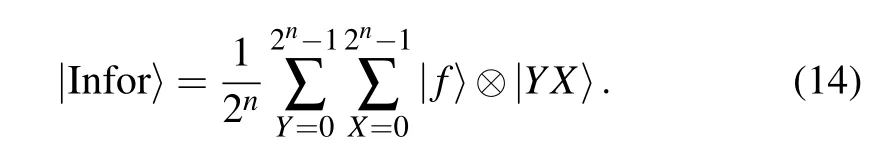
Accordingly, the composite system|CIK〉can consist ofq-qubit sequence gray value of cover image, one-qubit binary value of information image, one-qubit Boolean value of the key and 2n-qubit of the position, that is,|CYX〉,|f〉,|B〉and|YX〉, respectively. From the representation of NEQR,2n+q+2 qubits are needed to construct the composite system.
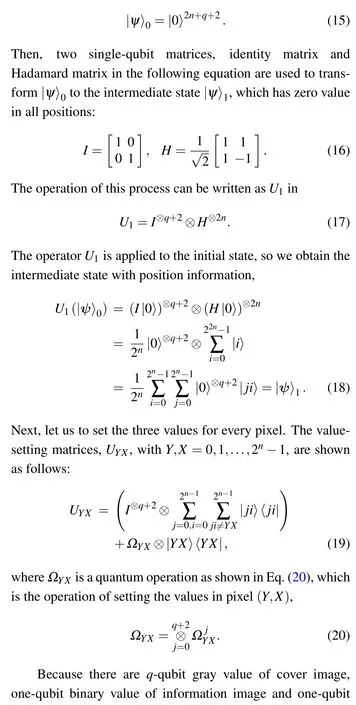
The first step is preparing 2n+q+2 qubits that are set as zero. The initial state is expressed as

The latter part of the procedure focuses on using the appropriate circuit to embed the information to the cover image.In this study, we embed the information qubit to the second least significant bit of gray value in cover image using controlled swap operation when the key value is equal to 1. If the key value is 0, the information will be hidden in the least significant bit. If we define an operatorUwhich carries out the controlled swap operation (CSO), the output form of the composite system after applyingUis demonstrated as

Obviously,from Eq.(25),the operatorUis just applied to the grayscale qubits. We only need two Fredkin(controlled swap)gates and a NOT-gate to construct the CSO model. Figure 1(a)shows the circuit realization of controlled swap operation.
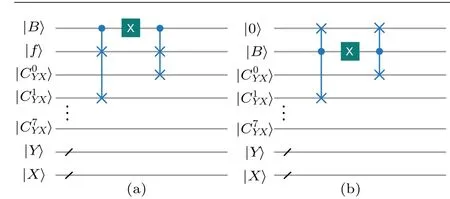
Fig. 1. Embedding and extraction circuits where (a) the information image is embedded to the cover image using two controlled swap gates and (b) the original information image is extracted from watermarked image by the reverse order of embedding circuit.
4.3. Extraction procedure
In terms of accessibility,the watermark extraction procedure is only available to the copyright owner, who uses the authentication key to authenticate the true ownership of a watermarked image.That is,if we want to extract the information image from watermarked image,it will be sufficient to use the authentication key without original image.
As mentioned in Subsection 4.2, the circuit model CSO is comprised by two Fredkin gates and one NOT gate, out of question, which is a reversible circuit. Exploiting this, the original information image can be restored by the inverse sequence of the embedded circuit. It is noted that an ancillary qubit with initial state|0〉is adopted to store the extracted watermark. The detailed circuit is illustrated in Fig.1(b). Thus,the operatorUrrepresents the reversibleUoperator that denotes a reversible controlled swap operation is defined as follows:
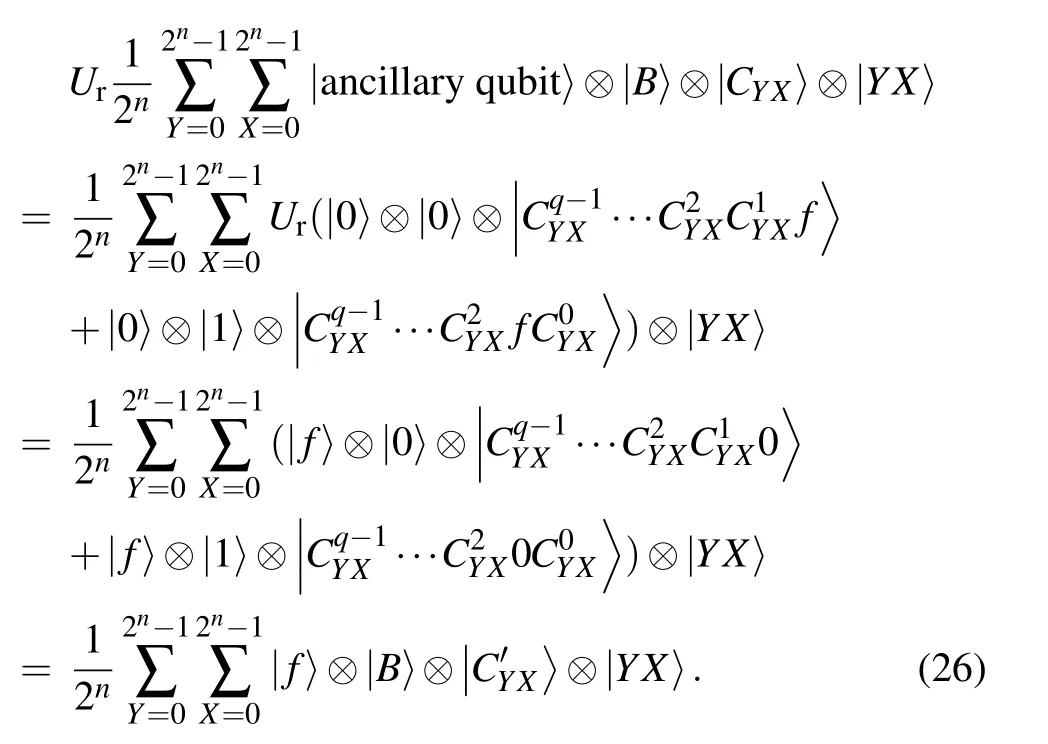
4.4. Circuits complexity
The complexity of circuit depends on what is taken as the fundamental unit. For the complex unitary operations, it can be decomposed to unary operators and binary operators.[38]Therefore, the circuit complexity of any unary gates and binary gates is considered as fundamental unit. From Fig. 1,the embedding and extraction circuits are implemented by two Fredkin gates and one NOT gate in the same way. The decomposition circuit of Fredkin gate is given as shown in Fig.2.

Fig.2. The implementation of the Fredkin gate using Hadamard(H),phase(S),controlled Not and π/8(T)gates.
Accordingly,the embedding circuit is decomposed to 35 basic gates,that is,the circuit complexity isO(1).The same is true for the extraction circuit. Compared with the complexity related to image size in the classical counterpart,our algorithm has a larger improvement than the classical algorithm.
5. Experimental simulation
To appraise the property of the proposed scheme, a set of cover image comprising of 8 images with 8-bit in depth and a size of 256×256 is employed (presented in Fig. 3). They are from the network, for example, the website: http://sipi.usc.edu/database/. However, without a physical quantum computer, the experiments are limited in simulations of quantum images and circuits as discussed in the preceding sections.
5.1. Similarity between images
The watermarking scheme aims at embedding specific content,usually the information of owner,to a cover image for copyright protection. It is important that the scheme should not change the cover image visually so that no one can distinguish whether the public image is an original image or a watermarked one.
There is a great deal of available quantum image processing literature to utilize the PSNR metric to evaluate the fidelity of watermarked images. It is most easily defined by means of the mean squared error(MSE),we can define it for twom×nimages(cover image and watermark image)as
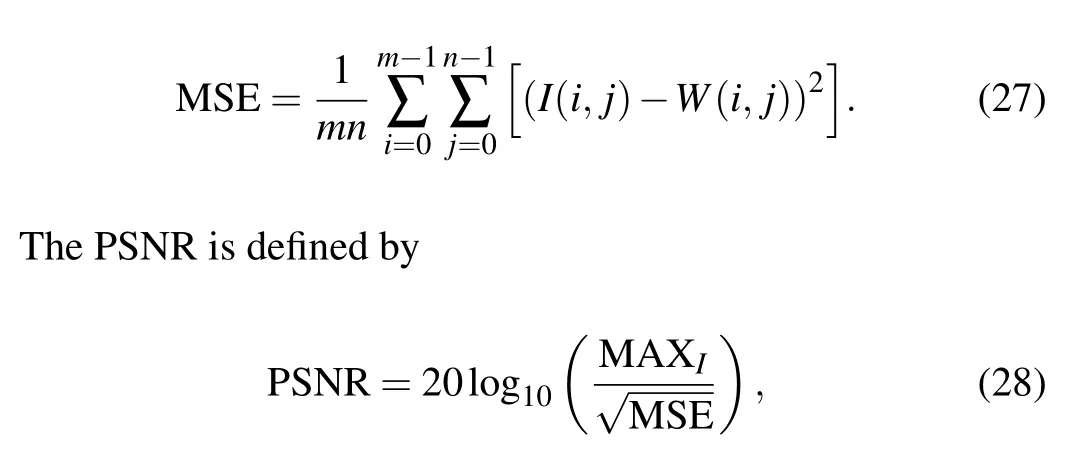
where MAXIis the maximum pixel value of imageI.
Fig.3. Images for simulation: (a)cameraman,(b)tulips,(c)barbara,(d)carnev,(e)airplane,(f)pepper,(g)mandrill,(h)fiore.
Now we present a method to measure the similarity between watermarked image and cover image based on the quantum informational entropy. As mentioned before, the informational entropy is represented by Eq.(4), which can denote the information contained in an image, and we know that the process of watermark embedding will cause changes in image information. Therefore, the method is suitable for evaluating the similarity of images.
ConsiderSandS'as the quantum informational entropy of the cover image and the watermarked one, respectively,which can be given as follows:

wherepiandp'iindicate the probability amplitude of the original gray value qubits and the manipulated one, respectively.Then,we quantify the similarity between two images using the entropy difference(ED),
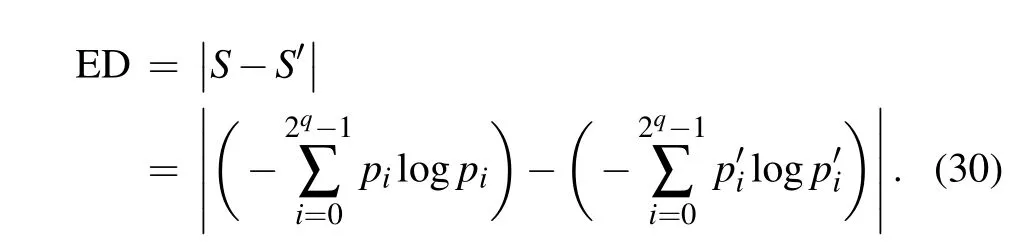
It would be obvious that the closer the ED is to 0, the more similar the two images being tested.
Since the probabilities must sum to one, the experiment can be simulated based on statistic of image pixels. We count the number of pixels in a classical image with particular intensity values, then the corresponding probabilities are obtained by dividing the total number of pixels. The results of PSNR and ED are summarized in Table 1, where the binary image‘Rice’is considered as the information image. In addition,for comparison,we give other entropy differences of image pairs in Table 2.
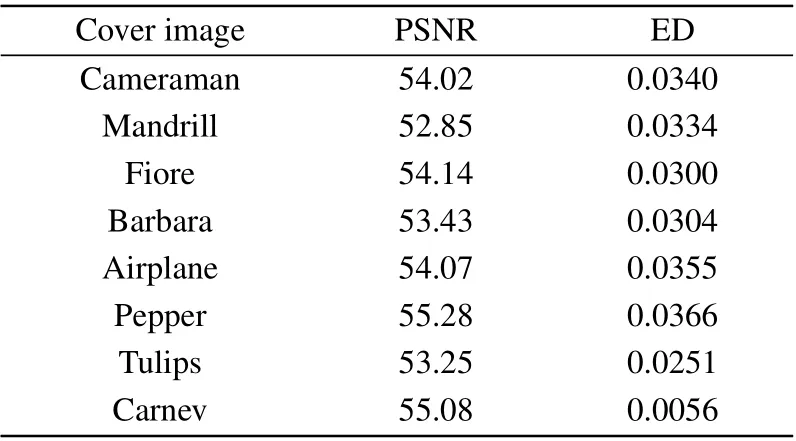
Table 1. The results of PSNR and ED.

Table 2. The entropy difference of two images.
5.2. Capacity
The capacity of quantum watermarking scheme is defined as the ratio of the number of secret qubits and the number of cover image pixels.Thus,the capacity of the proposed scheme is given as follows:

wherenis the qubits representing the size of cover image.Therefore,the capacity of the proposed scheme is 1 bit in every pixel.
5.3. Security
It is necessary to analyze the security under the attack of the illegal Eve for a quantum image watermarking algorithm.There are some types of attack such as intercept-resend attack and denial of service attack.[39,40]The simplest type of possible attack is the intercept-resend attack, where Eve measures the quantum states (photons) sent by sender and then sends replacement states to receiver, prepared in the state she measures. As we know that the quantum image is expressed in a superposition state,if the image is collapsed into another state once Eve measures it,the receiver cannot get the correct result when measuring. Thus the receiver will notice the presence of Eve and abort the communication.
For a denial of service attack,due to the good imperceptibility between original image and watermarked image, Eve cannot discover the presence of watermark. If Eve attempts to cut off all communication channels at a great cost,the receiver can obtain the watermarked image from public space or by routing communication via alternate links. Consequently,the proposed algorithm has good security to resist on Eve attacks.
6. Conclusion
A watermarking scheme for quantum images based on maximum entropy threshold segmentation is proposed. Because the quantum representation of image is pure state, the entropy of the threshold problem employs the quantum informational entropy. After applying the threshold value to segment the cover image, a binary image which uses as the authentication key to embed and extract information image is obtained. Therefore,the modification of the image object will be smaller than the background, which is useful in the field about health information system and so on. For example, the sensitive information of the patients and the doctors can be embedded to the medical data instead of widely distributing on the open network. The embedded quantum circuit designed in the proposed scheme consists of two Fredkin gates and a NOT gate,and the verification quantum circuit is also the same composition. Obviously, the complexity of the quantum circuits used in our scheme is quite low. Finally, to assess the performance of the investigated scheme,an entropy difference measure together with other commonly used metrics is used.
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant No. 6217070290), the Shanghai Science and Technology Project (Grant Nos. 21JC1402800 and 20040501500), the Scientific Research Fund of Hunan Provincial Education Department (Grant No. 21A0470), the Hunan Provincial Natural Science Foundation of China(Grant No. 2020JJ4557), and Top-Notch Innovative Talent Program for Postgraduate Students of Shanghai Maritime University(Grant No.2021YBR009).
- Chinese Physics B的其它文章
- Quantum walk search algorithm for multi-objective searching with iteration auto-controlling on hypercube
- Protecting geometric quantum discord via partially collapsing measurements of two qubits in multiple bosonic reservoirs
- Manipulating vortices in F =2 Bose-Einstein condensates through magnetic field and spin-orbit coupling
- Beating standard quantum limit via two-axis magnetic susceptibility measurement
- Neural-mechanism-driven image block encryption algorithm incorporating a hyperchaotic system and cloud model
- Anti-function solution of uniaxial anisotropic Stoner-Wohlfarth model

