Energy-efficient joint UAV secure communication and 3D trajectory optimization assisted by reconfigurable intelligent surfaces in the presence of eavesdroppers
Huang Hailong , Mohsen Eskandari , Andrey V.Savkin , Wei Ni
a The Department of Aeronautical and Aviation Engineering, The Hong Kong Polytechnic University, Hong Kong, China
b School of Electrical Engineering and Telecommunications, University of New South Wales, Sydney, 2052, Australia
c Data61, CSIRO, Australia
Keywords: Unmanned aerial systems (UASs)Unmanned aerial vehicle (UAV)Communication security Eaves-dropping Reconfigurable intelligent surfaces (RIS)Autonomous navigation and placement Path planning Model predictive control
ABSTRACT We consider a scenario where an unmanned aerial vehicle (UAV), a typical unmanned aerial system(UAS), transmits confidential data to a moving ground target in the presence of multiple eavesdroppers.Multiple friendly reconfigurable intelligent surfaces(RISs)help to secure the UAV-target communication and improve the energy efficiency of the UAV.We formulate an optimization problem to minimize the energy consumption of the UAV, subject to the mobility constraint of the UAV and that the achievable secrecy rate at the target is over a given threshold.We present an online planning method following the framework of model predictive control (MPC) to jointly optimize the motion of the UAV and the configurations of the RISs.The effectiveness of the proposed method is validated via computer simulations.
1.Introduction
Unmanned aerial systems(UASs)originated from military usage have been widely used for strikes and battlefield intelligence due to their ability to reduce the risk to humans [1,2].A great effort has been put into the research on how to avoid the detection by ground detection systems with sensors such as radars and minimizing the probability of being shot down by ground-to-air missiles so that the UAVs can complete their missions in battlefields [3-5].Simultaneously, defense technologies to efficiently and effectively fight against UASs have also been developed [6,7].
In recent years,unmanned aerial vehicles(UAVs),a typical set of UASs, also known as drones, have found various applications in civilian domains, such as moving target tracking, surveillance,parcel delivery, etc.[8-11].Among various applications, the fundamental problems relevant to UAVs include the coordination,planning,and control of UAVs.When multiple UAVs collaboratively conduct some mission, such as surveillance, the high-level UAV resource allocation determines the performance of the UAV team[12].With an assigned task, a UAV needs to plan the path to reach the target position and conduct the mission.To this end,optimally planning the path with the objective of minimizing energy consumption or time cost is a hot topic[11].Having the reference path,the low-level control of the UAV so that it can precisely track the reference is required[13].This short paper shares some similarities with using UAVs to track moving targets [8-10,14], and the problem of interest falls into the category of path planning.However,rather than keeping following a moving target with a circle-like trajectory, this paper aims to provide secure wireless communication service to a moving target.Some other aspects of the UAV communication security against eavesdropping were addressed in Refs.[15,16].
In typical wireless communication environments, radio signals may encounter multiple objects,such as buildings,which produce signal copies due to reflection, refraction, and scattering.These copies may arrive at the receiver with different magnitudes,phases,and delays, and distort the transmitted signal.To prevent this adverse effect, researchers have developed various paradigms by exploiting the randomness of the propagation environment, such as spatial modulation [17], spatial scattering modulation [18], and media-based modulation [19].Recently, a new technology, reconfigurable intelligent surface (RIS), has increasingly attracted attention.An RIS comprises many reconfigurable elements that adjust the reflection,refraction,and scattering characteristics of the incident signals by inducing the manageable phase shifts of the elements without complex decoding, encoding, and radio frequency processing operations [20].
RISs bring an additional dimension to communication systems,and there is emerging literature investigating communication systems involving RISs for the purpose of improving communication quality and security.The paper [21] studies a system with a ground transmitter(with no line-of-sight(LoS)to the UAV),a UAV receiver, and an RIS (serving as a relay).An optimization problem that plans the UAV trajectory and configures the RIS’s reflection is studied.The paper [22] adds a receiver node to the above system.Then, both the RIS and the UAV act as relays.The authors analyze the outage probability,average bit-error rate and average capacity,and investigate the optimal UAV position for performance optimization.Mobile RISs have also been considered.The paper [23]studies a system with a set of ground transmitters,a UAV-mounted RIS,and a receiver that has no LoS to the transmitters.The altitude of the UAV, the communication schedule,and the configuration of the RIS are optimized to minimize the age of information.On top of[23], the paper [24] considers an eavesdropper deployed near the receiver, and optimizes the communication schedule,the transmit power, the configuration of the RIS and the UAV trajectory to maximize the secure energy efficiency.The paper [25] further considers the case with multiple receivers and eavesdroppers.To maximize the sum secrecy rate of the legitimate receivers, a deep reinforcement learning method is presented to design the active beamforming at the UAV,the passive beamforming at the RIS,and the UAV’s trajectory.
For the extension of wireless communication coverage, the paper [26] maximizes the worst-case signal-to-noise ratio over the locations in the considered area by designing the transmit beamforming, the position of the UAV and an RIS configuration.Moreover, the use of software-controlled RISs has been proposed to increase the reliability of vehicle-to-everything (V2X) communications[27].In particular,the paper[28]evaluates the performance of an RIS-assisted vehicular communication system with interfering vehicles operating in the same frequency spectrum under both finite and infinite block length codes.
Different from the aforementioned publications, we consider a communication system with a UAV, some RISs, and some ground targets such as ground vehicles.The scenario of interest is that in a certain period, only one target should receive some confidential data from the UAV.In this period,the other targets are considered potential eavesdroppers.We consider that some friendly RISs deployed in the surrounding environment help to secure the UAVtarget communication and improve the energy efficiency of the UAV.The rationale of such a setting is explained as follows.To avoid being eavesdropped, a direct idea is to increase the path loss from the UAV to the eavesdroppers while maintaining that from the UAV to the target.Since the path loss directly relates to the physical distance,navigating the UAV to be close to the target while far away from the eavesdroppers can achieve the objective[29].So,without the assistance of RISs, the UAV needs to make much effort in the movement to avoid being eavesdropped on.In contrast, since RISs can reflect the wireless signals,we can configure RISs in a way such that the overall achievable rates at the target are enhanced while that at the eavesdroppers is reduced.Having this one more dimension is promising to enhance the solution space of the UAV movement, which can enhance the energy efficiency of the UAV.We formulate a new optimization problem to minimize the energy consumption of the UAV, subject to the mobility constraint of the UAV and that the achievable secrecy rate at the intended target is above a given threshold.We then propose an online method to solve the problem, which jointly optimizes the motion of the UAV and the configurations of the RISs following the framework of model predictive control(MPC)[30].The UAV predicts the states of the target and the potential eavesdroppers for a certain future horizon and then determines its motion and the RISs’ configurations.The RISs are configured to increase the achievable data rate at the target or decrease the eavesdropping rate of any potential eavesdropper.Simulation results show that the proposed method outperforms the strategies that only optimize the UAV’s trajectory or RISs’ configurations.
Compared to the existing work, the main contributions of this paper are summarized as follows.We formulate a new optimization problem that deals with the scenario where multiple RISs assist the secure communication between a UAV and a moving target in the presence of eavesdroppers.We propose an MPC-based strategy to configure the RISs and plan the UAV trajectory.Extensive computerbased simulations evaluate the performance of the proposed method.
The rest of the paper is organized as follows.Section 2 formally states the problem of interest.Section 3 presents the proposed method for optimizing the UAV’s motion and the RISs’ configurations.Section 4 presents computer-based simulation results to evaluate the proposed method.Finally, Section 5 briefly concludes the paper.
2.Problem statement
Consider that a UAV transmits data to a target while avoiding the data being overheard by the other potential eavesdroppers; see Fig.1.There is a set of RISs installed on the buildings along the road to facilitate UAV-target communication.In this section, we first describe the system models and then formally state the problem of interest.
Letp(τ): = [x(τ),y(τ),z(τ)] denote the UAV’s Cartesian coordinates at time τ.The UAV follows the below kinematics model[31]:
wherev(τ)∈Ris the linear speed,a(τ)∈R3is the heading,andu(τ)∈R3adjusts the heading of the UAV.Here,p(τ) anda(τ) are the states of the UAV, andv(τ) andu(τ) are the control inputs.Moreover, the control inputs satisfy the following constraints:
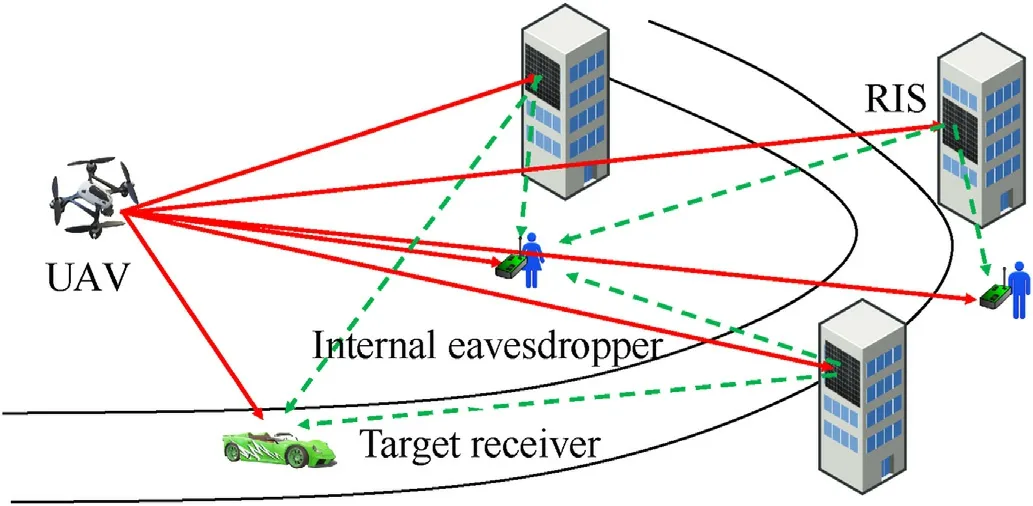
Fig.1.Illustration of the considered scenario.
whereUmaxandVmaxare given constants, and (·,·) is the inner product of two vectors.The last constraint in Eq.(2)guarantees that the vectorsa(τ) and u(τ) are always orthogonal.The model described by Eqs.(1)and (2)has been widely used to describe the motion of UAVs and mobile robots satisfying the nonholonomic constraint;see Ref.[31]and the references therein.Additionally,at any time,the UAV must keep its altitude within an allowed range:
whereZminandZmaxare given constants.Typically,Zminis larger than the heights of buildings for collision avoidance.
We consider the following model to approximate the energyconsuming powerq(τ) of the UAV [32]:
whereq0is a constant accounting for a fixed energy consumption power independent of the control inputs, and κ1and κ2are given constants.It is worth pointing out that the approach proposed in this paper is not limited to this model and can apply to any other energy consumption model.
Let pt(τ)=[xt(τ),yt(τ),zt(τ)]∈R3,pe(τ)=[xe(τ),ye(τ),ze(τ)]∈R3andpr= [xr,yr,zr] ∈R3denote the coordinates of the target, the eavesdroppern(n=1,…,N)and RISm(m=1,…,M),respectively.Here,NandMare the numbers of eavesdroppers and RISs,respectively.If eavesdroppernis stationary,pe(τ)≡pe.The RISs are stationary as they are fixed to buildings.Let nm ∈R3(||nm|| = 1)denote the normal vector of RIS m, andkru(τ),krt(τ),kre(τ) ∈R3denote the vectors from the RISmto the UAV, the target, and eavesdroppern,respectively.For instance,kru(τ)=p(τ)-pr(τ).We say the UAV(or the target,or eavesdropper n)is on the active side of RIS m if(nm,kru(τ))>0(or(nm,krt(τ))>0,or(nm,kre(τ))>0);in other words, the RIS can contribute constructively (or destructively) to the transmissions from the UAV to the target (or eavesdropper).
We consider that the UAV,the target and the eavesdroppers all have a single antenna,and each RIS has a uniform linear array ofLreflecting elements that can shift the phases of the incident signals before reflecting the signals.The phase shifter matrix of RISmis denoted by, where∈[0,2π),l=1,...,L,are the control inputs of RISmthat can be adjusted remotely by the RIS controllers based on the instruction of the UAV.Suppose that the UAV-target link, the UAV-eavesdropper link, and the UAV-RIS link are dominated by the LoS channels,and follow the free-space path loss model.In contrast, the RIStarget link and the RIS-eavesdropper link follow Rayleigh channel fading because of blockages.The target (or an eavesdropper) can receive two sets of signals.The first set is the direct signal from the UAV, and the second set consists of those reflected by the RISs.At time τ, the overall channel gains at the target receiver and the potential eavesdroppern,denoted byg0(τ)andgn(τ),respectively,are expressed as Ref.[21].
where the superscriptHstands for conjugate transpose,andI0(τ)is the subset of RISs of which both the UAV and the target are on the active side.Likewise,In(τ) is the subset of RISs of which both the UAV and eavesdroppernare on the active side.Moreover,hut,hun,hum,hmt, andhmnare the channel coefficients of the UAV-target,UAV-eavesdropper, UAV-RIS, RIS-target, and RIS-eavesdropper links, respectively, given by
By Shannon’s formula, the achievable rates at the target and eavesdropper n are given by
where P is the transmit power of the UAV,σ2 is the noise power at the ground target and the eavesdroppers,and.To secure the communication between the UAV and the target, we require that the secrecy rate S(τ),which is defined as the gap between the target and the largest achievable rate of the eavesdroppers,is no smaller than a given constant γ:
problem Statement.Considering a mission time period[0,T],we plan the movement of the UAV and the configurations of the RISs,so that the energy consumption of the UAV is minimized and the communication between the UAV and the target is secured.This problem is formulated as follows:
subject to Eqs.(1)-(3), and (10).In this problem, the UAV’s trajectory, together with the configurations of RISs are the control variables, and the security is regarded as a hard constraint in the trajectory designing phase.
This problem is challenging since constraint Eq.(10) is nonconvex in both the UAV position p(τ) and the RISs’ phase-shifts Φ1(τ), ..., ΦM(τ).In the next section, we propose a method to approximately yet efficiently solve this problem.
3.Proposed solution
We observe that the objective Eq.(11) and constraints Eqs.(1)and (2) only containu(τ) andv(τ), while these variables are coupled with Φ1(τ),...,ΦM(τ) in constraint (10).From constraint(10),we understand that:1)an RIS inI0(τ)should shift its elements’phases so that the reflected signals received by the target are added constructively to the direct signal from the UAV,and 2)an RIS in(τ)should shift its elements’ phases so that the reflected signals received by eavesdropper n are added destructively to the direct signal from the UAV.Moreover,u(τ) andv(τ) are coupled in the magnitudes of the received signals, which are embedded indut(τ),dun(τ)anddum(τ)by the UAV’s positionp(τ).Thus,the UAV should be close to the target(to boost the direct signal strength received at the target) and stay away from the eavesdroppers (to reduce the direct signal strength received at the eavesdroppers).These observations motivate us to design the configurations of the RISs and the UAV’s movement alternately.
3.1.Configurations of the RISs
Givenp(τ),pt(τ),pe(τ),…,pe(τ),andpr,…,pr,we can obtain the setsI0(τ),I1(τ),…,In(τ).If RIS m only belongs toI0(τ),we configure the elements of RISmsuch that the reflected signal received at the target aligns with the direct signal from the UAV in phase, i.e.,
wherel=1,…,L.The phase of thelth element of RISmis given by
Similarly, if RISmonly belongs toIn(τ), we have
wherel=1,…,L.Eq.(14)aligns the phase of the reflected signal to the opposite phase of the direct signal received at eavesdroppern.Due to the attenuation, the reflected signals are typically much weaker than the direct signal.
If RISmbelongs to two or more ofI0(τ),I1(τ),…,IN(τ),it may be impossible to find a solution satisfying different requirements,because we have more equations than variables;or in other words,the problem is over-determined.For example,we consider that RISmbelongs to bothI0(τ) andIn(τ).We come up with several strategies to configure the elements of the RISs.The first strategy is that we follow Eq.(13) so that the reflected signal helps improve the signal received at the target.The second strategy is that we follow Eq.(14)so that the reflected signal helps reduce the signal received at eavesdroppern.The third strategy looks for a balanced solution.To this end, we construct two equations for the considered example:
In general, if RISmbelongs to more than one of the setsI0(τ),I1(τ), …,IN(τ), we have more equations than variables.In other words, the problem is under-determined.Thus, it may be impossible to find an exact solution.In this case,we can obtain a balanced solution by applying the least squares method.We can select the solution among the individual solutions and the balanced solution that makes the maximum contribution toS(τ).
We summarize the RIS configuration procedure in Algorithm 1.We determine the RISs’ phase shifts in sequence.I0,I1, …,Inare initialized as empty sets.First,RIS 1 is assigned to the suitable sets amongI0,I1,…,INif both the UAV and the target or eavesdroppernare on the active side of the RIS.Then,we determine the individual solutions and/or the balanced solution.We evaluate the value ofSin Eq.(10)for each candidate under the currentI0,I1,…,IN,and take the candidate that maximizesS.Then, we proceed with the next RIS,given the phase shifts of the preceding RISs.Therefore,we only determine the phase shifts of one RIS in each round.Since each RIS can belong to at most(N+1)of the setsI0,I1,…,INwhile there areMRISs, the worst-case computational complexity of Algorithm 1 isO(MN).

Algorithm 1
3.2.Design of the UAV’s motion
Now, we design the UAV’s movement by determining the control inputsuandv.We assume thatuandvonly take the predefined candidates in the following sets
Considering constraint Eq.(2),we have||ui||≤Umax(i=1,…,|U|)and 0 ≤vj≤Vmax(j=1,…,|V|).Note that the setUis defined in the UAV body fixed frame,and any candidate ofUlocated within a disk of radiusUmaxcentered atp(τ)and perpendicular to a(τ);see Fig.2.Therefore, these control inputs satisfy constraint Eq.(2).
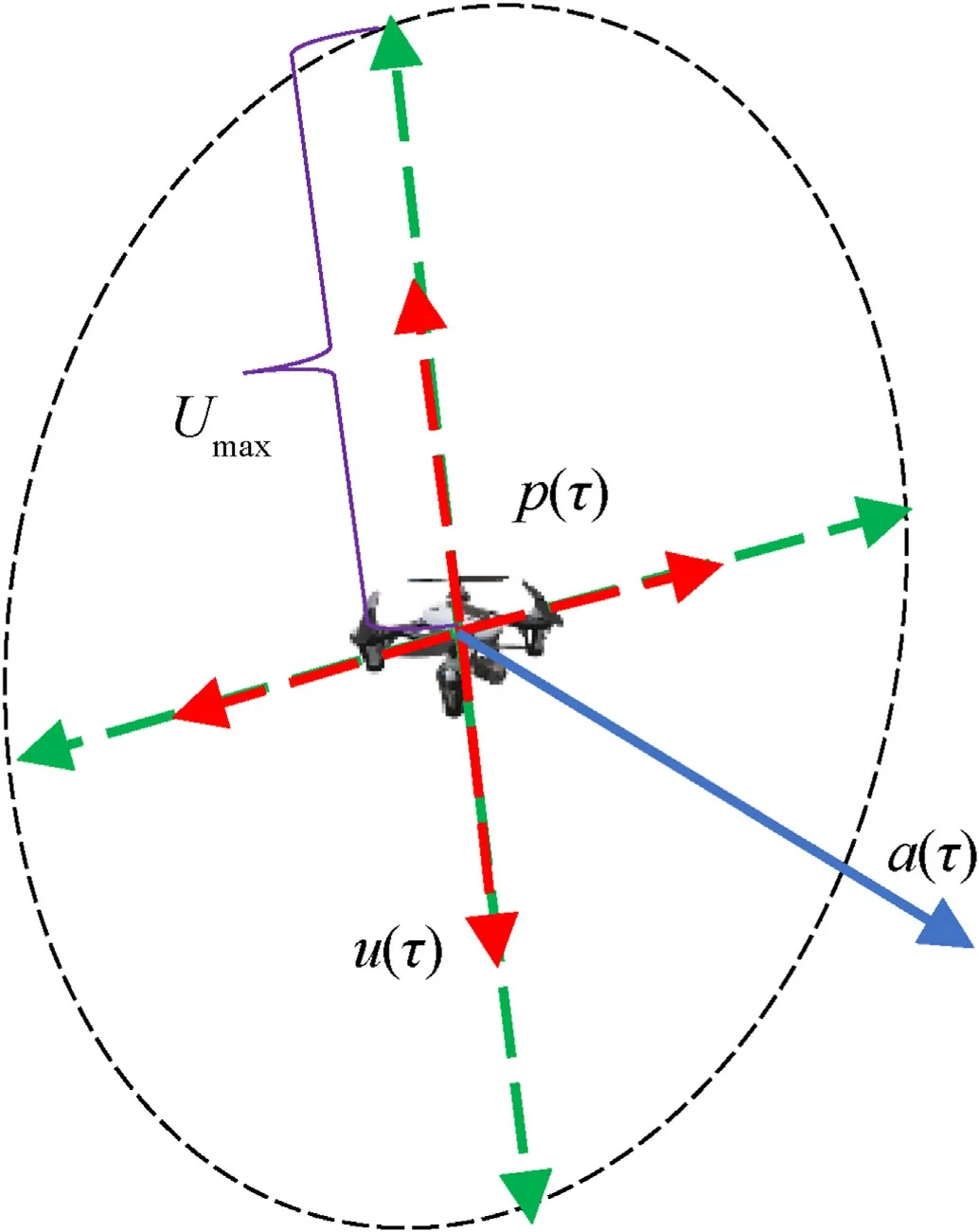
Fig.2.Candidates of the input u(τ).
Let δ be a given constant representing a small time slot.We assume that the control inputsuandvare updated at the instants 0,δ,2δ,…and remain unchanged during a slot time δ.Moreover,we assume that at the current time instant τ0, the positions of the target and the eavesdroppers are predictable1Though the position estimation and prediction is an interesting problem itself,it is out of the scope of this paper.for the futureKtime slots [τ0,τ0+Kδ], where τ0= 0,δ, 2δ, …,Kis a given integer, and.The problem of interest becomes
subject to Eqs.(1)-(3), and (10).Different from Eq.(11), the objective function Eq.(16) only evaluates the energy consumption of the UAV for a predictable future period of time.
Our approach to solving problem Eq.(16)subject to Eqs.(1)-(3)and (10), consists of the following two steps:
· Step 1:Shift and rotate thestandardtree(defined subsequently)withp(τ0) anda(τ0) to obtain a new tree.
· Step 2:Select the control sequence(i.e.,Ksets of control inputs at time instants τ0,τ0+δ,…,τ0+(K-1)δ)that minimizes Eq.(16) while satisfying constraints Eqs.(3) and (10).
InStep 1, the standard tree refers to the full tree rooted at the origin of the coordinate frame and pointing to the positiveX-axis.There are|U|·|V|possible control inputs at any instant,and we have(|U|·|V|)Kcontrol sequences in the tree.The standard tree can be constructed in advance and stored at the UAV.Then,at instant τ0,a new tree describing the UAV’s movement in the futureKslots can be quickly obtained.InStep 2, we need to ensure that a control sequence is feasible.For this purpose,we evaluate the nodes in the tree.If a node fails to satisfy Eq.(3)or Eq.(10),the node and its child nodes are removed.To verify the constraint Eq.(10), the RISs are configured by Algorithm 1.Then, from the feasible control sequences, we can find the one that minimizes Eq.(16).Since many nodes may be discarded, the practical computational complexity can be much smaller than the worst-caseO(MN|U|K|V|K).At each instant τ0= 0,δ, 2δ, …, the UAV executes the above steps and applies the control inputs to the instant τ0+ δ.This method follows the framework of model predictive control(MPC)[30],which is an effective method to control a process while satisfying a given set of constraints.
Remark III.1.The presented approach is centralized.Specifically,the UAV has access to configure the RISs,and a real-time connection between the UAV-RISs is required.In the presented approach, the eavesdroppers’ channel state information is known.For external eavesdroppers,the location and the channel state information may not be known.To secure the UAV-target communication in the latter case,a possible solution is to configure the RISs that have the UAV and the target both on the active side according to Eq.(13)and configure other RISs so that the reflected signals are in the null space of the equivalent channel[33].The latter has the chance to interfere with external eavesdroppers.Also,in many practical scenarios, some approximate estimates of the eavesdropper’s achievable rate and other parameters can be known to the UAV.For example, the UAV can potentially utilize radar sensing techniques to locate the potential eavesdroppers and accordingly estimate the achievable rates at the eavesdroppers.
4.Simulation results
We construct some urban-like environments with RISs attached to buildings and several stationary eavesdroppers,see Figs.3(a)and 4(a).The tallest building is 45 m.Each RIS hasL=64 configurable elements.Other system parameters areP= 20 dBm, α = -10 dB,κ = 2.5, σ2= -80 dBm, λ = 10-2 m,λ,Zmax= 100 m,Zmin=50 m,γ=2.5 bps/Hz,V={4,8}m/s,κ1=κ2=10,andU={(0,0, 0), (0,1, 0), (0, 0,1), (0, -1, 0), (0, 0, -1)}.
We consider three baselines for comparison.The first one follows[32]and optimizes the trajectory of the UAV only,denoted by“Trajectory, no RIS”.The UAV’s trajectories in the considered cases are shown in Figs.3(b) and 4(b), respectively.The second one adopts a trajectory the same as the target’s, denoted by “No trajectory,RIS”.The third one adopts the same trajectory as the second baseline without configuring the RISs,denoted by“No trajectory,no RIS”.
From Figs.3(d) and 4(d), we can see the proposed method and the “Trajectory, No RIS” baseline consume relatively lower energy thanks to the optimization of the UAV’s trajectory.For the second and third benchmarks, the energy consumption depends on the target’s trajectory, which is not controllable.From Figs.3(c) and 4(c), we can see that only the developed method, i.e., “Trajectory,RIS”, achieves the instantaneous secrecy rate requirement (i.e.,above γ).The“No trajectory,RIS”baseline comes after,but there are some instants at which the instantaneous secrecy rate falls below γ.
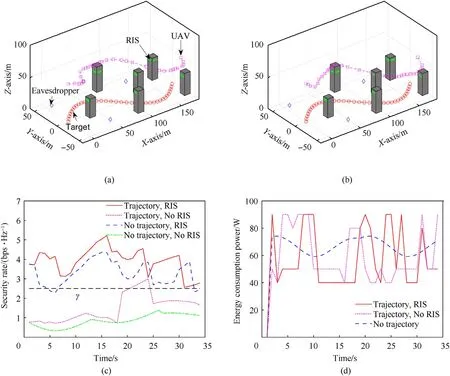
Fig.3.Case 1: (a) The UAV’s trajectory by the proposed method; (b) The UAV’s trajectory obtained by the first baseline; (c) Secrecy rate; (d) Energy consumption power.
These case studies demonstrate the effectiveness of the developed method.Moreover, looking at Fig.3(c) (or Fig.4(c)), we find that configuring RISs is more likely to obtain a high secrecy rate than optimizing the UAV’s trajectory.The main reason is that the latter mostly helps large-scale components of the propagation channels,while the former helps to align the phases of the received signals.
5.Conclusions
In this paper,we considered a communication system involving the new RIS technology.We investigated the problem of securing the UAV-target communication assisted by RISs in the presence of eavesdroppers.We formulated an optimization problem to minimize the UAV’s energy consumption while satisfying the secrecy rate requirement.We developed an MPC-based online method to plan the UAV’s 3D trajectory and configure the RISs.Via simulations,we found that optimizing RISs’configurations is promising to achieve better performance than optimizing the UAV’s trajectory.Analytical study of such a performance gap is our future research direction.
Declaration of competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgements
This work received funding from the Australian Government,via grant AUSMURIB000001 associated with ONR MURI Grant N00014-19-1-2571.
- Defence Technology的其它文章
- The interaction between a shaped charge jet and a single moving plate
- Machine learning for predicting the outcome of terminal ballistics events
- Fabrication and characterization of multi-scale coated boron powders with improved combustion performance: A brief review
- Experimental research on the launching system of auxiliary charge with filter cartridge structure
- Dependence of impact regime boundaries on the initial temperatures of projectiles and targets
- Experimental and numerical study of hypervelocity impact damage on composite overwrapped pressure vessels

