Swarm intelligence based clustering and localizing methods for loitering munitions in a satellite denied environment
Hao WU, Zhonghong WU, Zhangsong SHI, Shiyan SUN, Pengfei WU,Zhi WANG
School of Ordnance Engineering, Naval University of Engineering, Wuhan 430033, China
KEYWORDS
Abstract In the networking of loitering munitions during a battle, clustering and localizing algorithms become a major problem because of their highly dynamic topological structure, incomplete connectivity,and limited energy.This paper proposed swarm intelligence based collaborative localizing, clustering, and routing scheme for an ad hoc network of loitering munitions in a satellite denied environment.A hybrid algorithm was first devised by integrating an improved coyote optimization algorithm with a simplified grey wolf optimizer under the sinusoidal crossover strategy.The performance of this algorithm was considerably improved thanks to integration.On this basis,a swarm intelligence based localizing algorithm was presented.Bounding cubes were created to reduce the initial search space, which effectively lowered the localizing error.Second, an energysaving clustering algorithm based on the hybrid algorithm was put forward to enhance the clustering efficiency by virtue of grey wolf hierarchy.Meanwhile, an analysis model was developed to determine the optimal number of clusters using the lowest possible number of transmissions.Ultimately,a compressed sensing routing scheme based on the hybrid algorithm was proposed to transmit data from a cluster head to a base station.This algorithm constructed an efficient routing tree from the cluster head to the base station,so as to reduce the routing delay and transmission count.As revealed in the results of simulation experiments, the proposed collaborative localizing, clustering and routing algorithms achieved better performance than other popular algorithms employed in various scenarios.
1.Introduction
Once the internet of things was introduced to battlefields,ammunitions became information-based, intelligent, and networked.1The most typical development can be seen in ad hoc networking of loitering munitions.As a new conceptual type of ammunitions, loitering munitions are able to cruise and stand by for a variety of operations in combat above a target area.2By virtue of networking, loitering munitions can form into an ammunition cluster, also known as networked munitions.In practical operations, networked munitions can deliver the multiplier effect of 1+1>2.For instance,a network of three KUB-BLA loitering munitions launched by Russia in the Russia-Ukraine War during 2022 instantly destroyed a troop of Ukrainian soldiers with only individual munitions,3which must be attributed to more accurate target information for munitions after networking.
Accurate position information plays a crucial part in the collaborative control and engagement of a loitering munitions cluster.Networked munitions are characterized by a highly dynamic topological structure, incomplete connectivity, and limited resources.4Hence,localizing the nodes of ammunitions is a major problem.Under normal circumstances, the nodes can be localized by virtue of Beidou/GPS and inertial navigation.However,Beidou/GPS have signals that are vulnerable to interference or interrupted by an enemy’s attack in a battlefield.Some methods have been therefore developed to address the problem of dynamic ad hoc network localization in a satellite denied environment.Most methods are based on ranging.5Normally, bilateral or trilateral measurement is adopted for localization.Nevertheless, these methods face an inevitable problem, that is, Flap Ambiguity (FA).6Additionally, most dynamic ad hoc networks rely on Beidou or GPS in the localization of nodes for clustering,which is harmful to the continuous flight of loitering munitions because of their large energy consumption.For this reason, an energy-saving, flexible and extensible clustering and localizing protocol must be urgently devised.Above all,this paper will focus on two aspects,specifically, collaborative localization and clustering protocol of an ammunition ad hoc networking.
1.1.Localization algorithms
Loitering munitions are equipped with a tactical data link for data sharing.For the purpose of high-accuracy localization,some experts recommended the use of range-based localizing methods to implement the collaborative localization of ammunitions.But requires observation equipment, which increases cost and requires more room.For this reason, this paper presents an exploration of collaborative localization for the nodes in the ad hoc network of ammunitions without additional observation equipment.
As for the range-free localizing algorithm, the DV-hop method has been widely applied in localizing the nodes of an ad hoc network.This method can estimate the location of each node based on the number of hops needed from one node to the anchor node.However, its localizing accuracy is significantly affected by observation error.In recent years, a biology-inspired optimization algorithm has been gradually applied because of its advantages such as low complexity and high accuracy.Gui et al.7put forward two improvements of DV-hop, specifically, checkout DV-hop and selective 3-anchor DV-hop.In the first improvement, the estimated location of an unknown node is adjusted to its distance from the nearest anchor node.However, more selective locations are generated for an unknown node using the number of hops needed from three optimal anchor nodes in the second improvement.According to the simulation results, selective 3-anchor DV-hop offers the best localization accuracy compared with checkout DV-hop and the original DV-hop method.Gui et al.8put forward a Distributed Connectivity based DV-hop (DCDV-hop), which could almost achieve the optimal localization for distributed networks.As revealed in the simulation results, DCDV-hop is more accurate than CCDV-hop and other methods, regardless of high complexity and if the connectivity of all nodes is ignored.Liu et al.9proposed an improved algorithm based on neural dynamics, that is,ND-DV-hop.Through error analysis,this algorithm can be used to determine the error range between an unknown node and an anchor node.Thus, the traditional localization model is transformed into algebraic equations,which are solved with a neural dynamics algorithm to obtain a solution without residual error.As revealed in the simulation, the proposed algorithm is extremely robust and accurate in the localization process.Rajakumar et al.10used the GWO algorithm for localization, and introduced the GWO-LPWSN algorithm for localizing unknown nodes.The simulation proved that this algorithm has lower computing cost and higher accuracy than Particle Swarm Optimization (PSO) and other algorithms.
1.2.Clustering algorithms
In recent years, bionic algorithms have been introduced to solve the clustering problem of a dynamic ad hoc network.11These algorithms are simple to implement, and efficient when resolving complicated optimization problems.12Additionally,local minimums can be avoided with these algorithms.13For instance, a Swarm Intelligent Optimization Algorithm (SIOA)is an intelligent optimization method that simulates the collective behaviors of social groups in nature,14and has been developed into Particle Swarm Optimization (PSO),15Grey Wolf Optimizer (GWO),16and Coyote Optimization Algorithms(COA).17With advantages such as simple implementation and effective global and large-scale optimization, SIOAs have been widely applied in various fields including multi-object optimization, data clustering and pattern recognition.18
As a novel SIOA algorithm,the concept of a GWO was put forward by Mirjalili et al.19in 2014.It features simple principles, good mining capability, and few adjustable parameters,but may easily result in a local optimum or perform poorly in resolving complicated optimization problems.Consequently, this algorithm has been studied and improved by scholars, such as, hybrid improvement.Zhang et al.20for instance, put forth a hybrid algorithm of GWO and an artificial bee colony algorithm.In the process of observing bees in an artificial bee colony, GWO was adaptively integrated to enhance the mining capability and the optimization efficiency.Zhang et al.21proposed a hybrid algorithm of biogeographybased optimization and GWO.The algorithm integrates the improved biogeography-based optimization algorithm with the GWO based on back-propagation learning to maximize the optimization.Teng et al.22introduced a hybrid algorithm of PSO and GWO to deliver better searching capability and robustness.Arora et al.23described a hybrid algorithm integrating a crow search with GWO to realize more effective global optimization.In the past two years, researchers have also used GWO algorithms to resolve such problems in different types of networks as localization,24path planning,25topological control,26and clustering.27
In 2018, Wu et al.28developed a new SIOA algorithm,COA, to simulate the life, growth, and death of coyotes in packs.With its unique search model, structure and outstanding optimization performance, COA has major advantages in resolving complicated optimization problems.However, it is still troubled by such deficiencies as low search efficiency,poor operability, and slow convergence.Additionally, COA, as a new algorithm, needs to be further improved and introduced to other fields.
1.3.Contribution of the study
This paper proposes three algorithms designed to effectively address the clustering and localizing problems of a loitering munitions ad hoc network in a satellite denied environment.These algorithms include a Swarm Intelligence based ammunition cluster collaborative Localizing algorithm(SIL),a Swarm Intelligence based Clustering algorithm (SIC), and a Compressed Sensing algorithm based on HCOGW (CSHCOGW).The main contributions of this study are as follows:
(1) A hybrid, specifically a HCOGW, of the COA and GWO algorithms is proposed.First, the improved COA is introduced.In the growth process, a Gaussian global best growth operator is proposed to enhance the search capability.In the meantime, a scheme of dynamically adjusting the number of in-group coyotes is presented.At the beginning of the search, fewer groups are used to weaken the positive feedback effect of the global best solution and reinforce the search capability.At the late stage of search, more groups are employed to strengthen the positive feedback effect of the global best solution, reinforce the mining capability, and enhance the operability of the system.Subsequently, the GWO is improved to generate a Simplified GWO (SGWO), which retains its strong local search capability and improves its operability.In the end, sinusoidal crossover strategy is adopted to organically combine ICOA with SGWO.After proving a perfect balance between the exploration and mining capabilities of coyotes in a group during their growth,this strategy enables HCOGW to resolve the problem of local optimum and embrace a strong capacity of global optimization.
(2) A localizing method, SIL, is put forward based on the HCOGW algorithm.In the HCOGW model,a lead wolf dynamically estimates the location of a prey, so that every wolf moves toward the estimated location.As revealed in the simulation results, the SIL algorithm has the best performance in terms of localization accuracy,convergence rate,computing cost,and energy consumption, compared with other algorithms such as a selective 3-anchor DV-hop,7DCDV-Hop,8ND-DVHop,9GWO-LPWSN10and DV-hop.6
(3) A clustering method, SIC, is put forward based on the HCOGW algorithm to effectively improve the service life of the network.With the highly dynamic topological structure, the scale and quantity of clusters exert a significant effect on the quality of communications.As a result, an analysis model was constructed in this paper.The optimal number of clusters was also determined.This SIC algorithm is compared with some popular clustering algorithms such as Cluster-based Location-Aided Dynamic Source Routing (CBLADSR),29Ant Colony Optimization (ACO),30EALC,31GA,32and SOCS.33As revealed in the simulation results, the SIC algorithm can deliver a highly reliable network with the shortest cluster building time.
(4) Based on the SIC algorithm,a novel method is proposed to select the Cluster Heads(CHs)using the fitness of loitering munitions.The key is to identify the CH nodes characterized by high residual energy,multiple neighbor nodes, and a short intra-cluster distance.These nodes are responsible for data summary and transmission.The simulation results demonstrate that SIC needs a small number of CH nodes, and performs better than several popular algorithms in terms of total energy consumption.
(5) The CS-HCOGW algorithm is proposed for data transmission in the clustering process.In each cluster,cluster members transmit data to the corresponding CHs, but the CS-HCOGW algorithm is not used in this process.Subsequently, each CH is transmitted to the Base Station (BS) through CS-HCOGW routing.With the proposed algorithm, the least cost routing from the CHs to the BS is determined to reduce the number of transmissions and limit the delay during routing.In the simulation, CS-HCOGW routing is compared with the clustering algorithm without Compressed Sensing (CS) and the Shortest Path Tree(SPT)34algorithm.The results reveal that CSHCOGW requires the lowest number of transmissions,which effectively lowers the energy consumption of the entire network.
2.Preliminary findings
2.1.Maneuvering scenario
A typical engagement scenario in a satellite denied environment is illustrated in Fig.1.Munitions are automatically networked and clustered in the air.The data from Cluster Members (CMs), e.g.the images or videos collected by loitering munitions or video scout projectiles, are transmitted through transmission-efficient routing to the Base Station(BS), providing battlefield information for commanders.All the ammunition nodes (CMs) are equipped with measurement and communication units.The clustering and localizing system proposed in this paper is mainly related to two phases,known as offline and online phases(Fig.2).In the offline phase,nodes are localized to determine the topographical structure of the ad hoc network.Subsequently, the online phase starts and involves the following two subsystems: clustering and data transmission.In the clustering process, each node (CM) can identify any adjacent nodes, and select a Cluster Head (CH)node for its cluster.Data transmission aims to fulfill the communications and data aggregation between CMs,CHs and the BS.

Fig.1 Engagement scenario showing a Cluster Head (CH), Cluster Member (CM), and Base Station (BS)in action with a compressed sensing.
2.2.Grey wolf optimization algorithm
The Grey Wolf Optimization (GWO) algorithm simulates the rigid leadership hierarchy and swarm predation of grey wolves.In their leadership hierarchy, grey wolves are classified into α,β, δ and ω grey wolves from higher (leader) to lower (subservient follower) class, that is, the β wolf is the pack leader,and theα wolf is the second most dominant and so on.The pack will hunt, approach, capture, encircle, attack and kill prey as a group.In the GWO algorithm, α, β, δ and ω grey wolves represent the first, second, and third best solutions,and another candidate solution, respectively.The mathematical model for grey wolf’s encirclement behavior is as follows:
where Dis represents the distance from a grey wolf to its prey;t indicates how many iterations have been conducted so far; Xpis the location vector of the prey;X is the location vector of the grey wolf.As shown in Eqs.(3)and(4),A and C are coefficient vectors.The coefficient e decreases linearly from 2 to 0 in the iteration, as given in Eq.(5).In these equations, MaxDT represents the maximum iteration; r1and r2are the evenly distributed random vectors in [0,1]; c1is the adjustable parameter,35⊗stands for the multiplication of the corresponding components for two vectors.The mathematical model of the hunting behavior is as follows:
where Disα,Disβand Disδindicate the distance from the α grey wolf to three best grey wolves,respectively.Eq.(12)defines the new position that the grey wolf ω moves to under the guidance of α,β and δ grey wolves,that is,the new solution generated by the GWO algorithm.
Compared with the classical intelligent swarm algorithms such as PSO,the GWO algorithm has the following characteristics:(A)The GWO algorithm uses the three best grey wolves(solutions) to guide the ω grey wolves in hunting.This algorithm has strong local search capability, but may be easily trapped in a local optimum while coping with any complicated optimization problem.(B) The GWO algorithm involves only two parameters, e and c1.The former is dynamically adjusted,but the latter is usually taken following the method described in Ref.28.It is therefore, highly operable since only a few parameters are adjusted.(C) The GWO algorithm is easy to implement because of its simple principles, but it is updated with the dimensional computation including Eqs.(6)–(12).Therefore,its computation is very complicated.(D)The objective function uses parallel computing, so that the GWO algorithm can be executed very quickly.
2.3.Coyote optimization algorithm
A Coyote Optimization Algorithm (COA) contains initialization parameters and four major steps including creation of a coyote pack, in-group coyote growth, birth and death of coyote pups, and group expulsion and reception.
In Step 1,the parameters are set including coyote pack size N, number of coyote groups Np, number of in-group coyotes Nc, and MaxDT, where N=Nc×Np.Subsequently, the groups in the coyote pack are randomly initialized.The randomized operation of the cthcoyote in the pthgroup in the hthdimension is defined by Eq.(13).Finally, the fitness(fit)of each coyote soc is calculated as follows:
where ubhand lbhrepresent the upper and lower bounds of the social state factor in the hthdimension for the coyote;h=1,2,...,D, where D is the search space dimension; r is a series of random numbers evenly distributed in [0,1]; and f stands for the fitness function.
Step 2 involves the process in which the best coyote,alpha,the group culture cult and two randomly selected coyotes cr1 and cr2 affect the coyotes in the group, that is, the impact of δ1and δ2on the in-group coyote growth.Among them, cult is calculated by Eq.(15).In other words, each factor is the median of the social factors of all the coyotes in the group(O is the sequence of ranked social factors).Therefore, cult is also known as median coyote.Moreover, δ1and δ2are calculated by Eqs.(16) and (17) respectively.The growth of coyotes is as follows:
where new soccis the new solution obtained for the growth of the cthcoyote in the group;and r3and r4are random numbers evenly distributed in [0,1].After the growth of coyotes in the group, their social fitness is evaluated as defined by Eq.(19).The new fitness is denoted by new fitc.
Finally, an iterative greedy algorithm is adopted for survival of the fittest as given in Eq.(20).Hence, the newly identified better coyotes take part in the growth of the other coyotes in the group, so as to speed up convergence.
In the third step,the birth of coyote pups is affected by the genes of randomly selected coyote parents and the environmental factors, which is represented by Eq.(21):
where rhstands for the random numbers evenly distributed in[0,1]; h1and h2indicate two randomly selected dimensions to ensure that pups can receive genes from their father coyotes;Rhrepresents the randomly generated variation in the decision variables of the hthdimension; Psand Paare dispersion and correlation probabilities, respectively, which decide the inheritance and variation of coyote pups,as defined by Eqs.(22)and(23).
After a coyote pup is born, its social fitness is evaluated to determine its ability to live or document its death.Specifically,there are three circumstances with regard to social fitness: (A)if a coyote in the group is inferior to the coyote pup,that coyote dies.The coyote pup lives, and its age is set to 0, that is,age = 0; (B) if several coyotes in the group are inferior to the coyote pup, the weakest and oldest coyote among them dies.The coyote pup lives, and its age is set to age = 0; (C)if all coyotes in the group are superior to the coyote pup, the coyote pup dies.
In Step 4,coyotes are expulsed and received at the probability Pein COA.The coyotes are first randomly assigned to groups, but some coyotes may leave their group and join any other group.This random expulsion and reception guarantees the diversity of coyotes in each group and the sharing of information between groups.The probability Peis calculated by Eq.(24):
As revealed in the above description,a COA has the following advantages: a good search framework, strong local search capability and some global search capability, which can better solve complex optimization problems.
Nevertheless, a COA has some disadvantages including the following:(A)The computation is very complicated because of its complex structure.(B) The iterative greedy algorithm used in the COA has poor stability and efficiency.(C)A large number of parameters need to be adjusted including Pe,Npand Nc,so that it is not greatly operable.(D)The multi-group structure may enhance the exploration capability, but the lack of information sharing between groups will lead to slow convergence in the later phase.
3.Energy-efficient swarm intelligence based localization algorithm
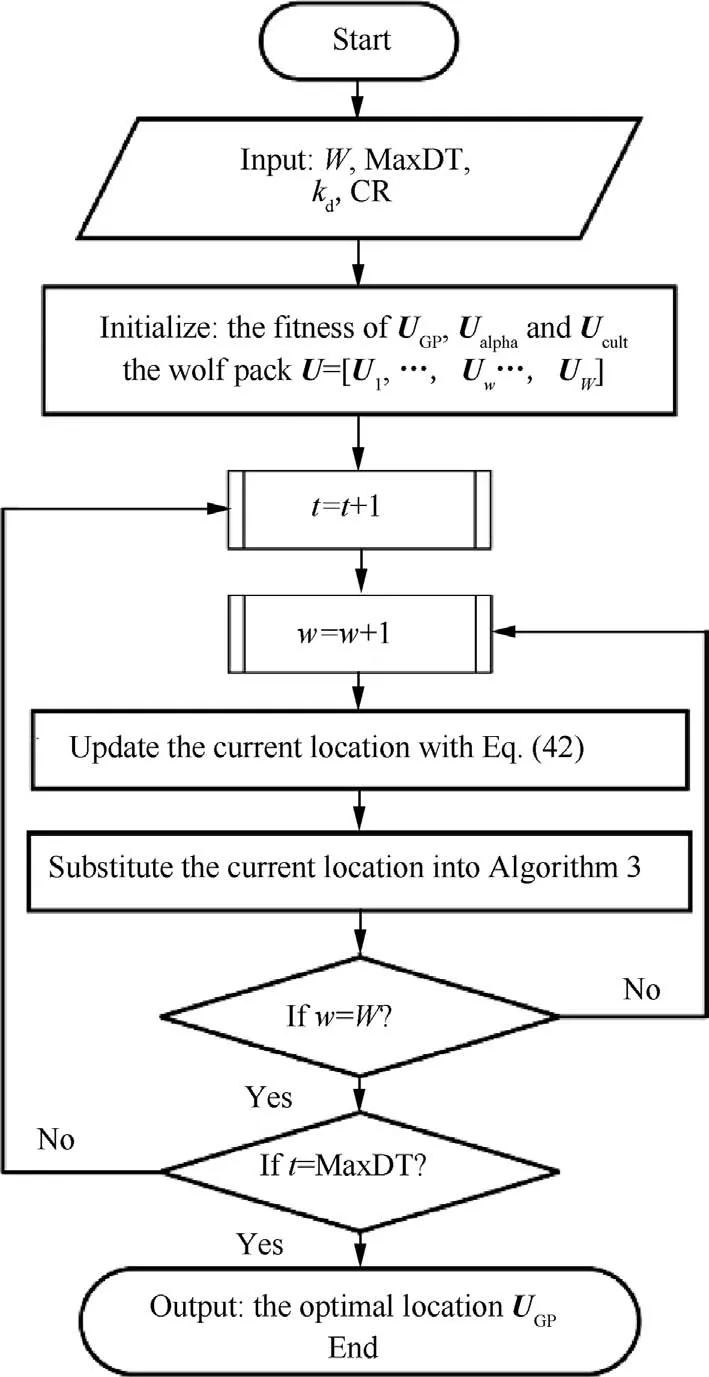
For loitering ammunition ad hoc networking, an energyefficient Swarm Intelligence based Localization algorithm(SIL) is put forward in this section.In the SIL algorithm, a boundary is established to improve sampling efficiency by reducing the initial search space.With lowered computation cost, rapid convergence is achieved.The initial location of nodes is estimated as defined in Algorithm 1.Subsequently,the existing swarm intelligence algorithms, that is, Grey Wolf Optimizer (GWO) and Coyote Optimization Algorithm(COA), are integrated to develop a hybrid optimization algorithm (HCOGW) based on sinusoidal crossover strategy, as defined in Algorithms 2 and 3.This hybrid algorithm further enhances the optimization.In the end, the SIL algorithm is used with HCOGW to optimize the results of initial localization as illustrated in Algorithm.As compared with the existing popular algorithms in a simulation experiment, the SIL algorithm has better localization accuracy and faster convergence.
3.1.Localization energy consumption
In this study,N denotes the number of patrol missile nodes,Nadenotes the number of anchor nodes,the percentage of anchor nodes is Ar=Na/N, the number of unknown nodes is Nu=N-Na, Sndenotes the set of neighboring nodes of a node within the communication range, and the node communication radius is R.There is no central node in the ad hoc network, wherein each node has the same status, and the anchor node is provided with its accurate location information at any time.
The energy model put forth by Heinzelman et al.36has been a popular method for energy consumption.A node of unknown coordinates has its transmitted and received energy denoted by ETxand ERx,respectively.The value is represented by ψ and the transmission distance by d, so that there is:
where Esand Eastand for the energy consumption because of the transmission in the transmitter circuit and the radio frequency amplifier, respectively.
3.2.Sampling area
The distance of communications between nodes is set as R.When two nodes i and j in the loitering munitions ad hoc network fall into the communication range,they can directly communicate with each other.In this case, the two nodes are onehop neighbors.If the nodes i and j are within the 2R range,they are two-hop neighbors.The maximum velocity of flight at a node is indicated by vmax.Assuming that the velocity at a node keeps at vmaxwithin the period from t-1 to t, if an anchor node is able to broadcast the scanning signal periodically, the period T is defined by Eq.(27):
where p(lt|lt-1) stands for the probability of correctly estimating the location of the unknown node;Rmaxindicates the maximum distance the unknown node moves at the velocity vmax;d(lt|lt-1)denotes the Euclidean distance between two locations ltand lt–1of the unknown node at the time t and t–1, respectively.The sampling points are filtered for the unknown node based on the information collected from its one- and two-hop anchor nodes.At the time t,the sampling particle l is subject to the following filtering conditions:
where a is the anchor node; l is the sampling particle; Sa1stands for a set of one-hop anchor nodes; and Sa2represents a set of two-hop anchor nodes.
3.3.Creation of bounds

Eq.(30) indicates the communication area of the anchor node Aki.For all 1 ≤i ≤m,any unknown node p in(BCi)has:
For (xi, yi, zi), Eq.(31) can be constructed as:
Thus,

With Eqs.(34) and (35), we obtain:
If a loitering munitions node has n one-hop anchor nodes,its bounding box can be created as:
where xminand xmaxstand for the upper and lower bounds of x,respectively.Other coordinates can be estimated in a similar way.As for two-hop anchor nodes,R in Eq.(37)can be simply replaced by 2R.
Let the feasible region of Nube FRuas shown in Fig.3(a).The intersection of the bounding cubes FRuis formed by the minimum upper coordinate and maximum lower coordinate of each cube:
where Buand Blare the upper and lower bounds of Nu,respectively, and defined by:
where diis the estimated distance from the anchor node Akito the unknown node.As shown in Fig.3(b), no intersection of the bounding cubes exists in the pseudo-intersection period.duidenotes the distance from Akito the boundary of the cube where it is located.

Fig.3 Intersection and pseudo-intersection of bounding cubes.
Let Bl= (xl,yl,zl)Tand Bu= (xu,yu,zu)Tbe the upper and lower bounds of the region, respectively.The pseudointersection of the bounding cubes should comply with the following rules:

3.4.Distance estimation
The estimated and actual values of unknown nodes are assumed to be (xei,yei,zei) and (xri,yri,zri), respectively.The localization error can be expressed as:
Estimating the location of unknown nodes can be regarded as an optimization problem, and then resolved by minimizing the objective function.The objective function of localization error is defined as:
where dijand ^dijrepresent the actual and observed distances between the unknown node and the anchor node, and K indicates the number of neighboring nodes.
A multi-hop algorithm does not require other observation equipment on loitering munitions, so that it is economically advantageous.As shown in Fig.3, Nustands for unknown nodes.In the feasible region of Nt, Ak1, Ak2and Ak3are three anchor nodes adjacent to Nt, while h1,Nt,h2,Nt,h3,Ntare the largest number of hops to three anchor nodes, respectively.
The radius to construct the feasible region is R ∙hi,Nt.The feasible region can be defined by the bounding cubes as follows:
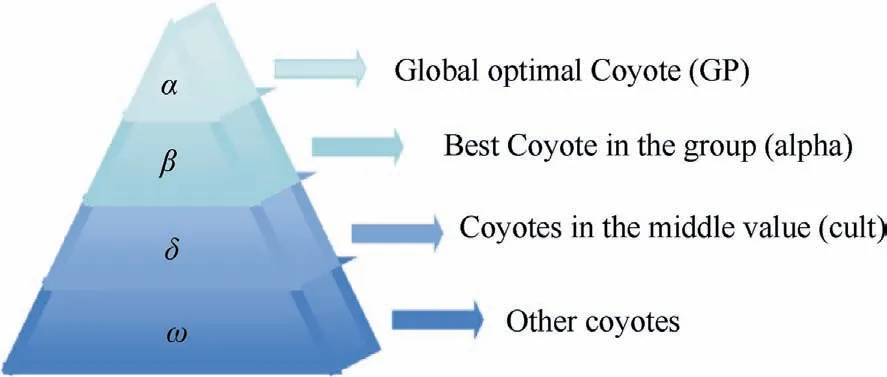
Fig.4 Comparison of hierarchies of the Grey Wolf Optimizer(GWO) and a Simplified GWO (SGWO).
Localization is an iterative process.Localizing an unknown node will require the use of at least three anchor nodes.After being localized, the node will be used as an anchor node to localize other unknown nodes.The process is repeated until all nodes are localized.The network search process is as presented in Algorithm 1.
3.5.A hybrid algorithm of coyote optimization with a grey wolf optimizer based on sinusoidal crossover strategy
Three algorithms are presented in this section, specifically, an Improved Coyote Optimization Algorithm(ICOA),Simplified Grey Wolf Optimization(SGWO),and a Hybrid Coyote Optimization algorithm with Grey Wolf optimizer (HCOGW).
Among them, ICOA involves a Gaussian global best growth operator and a scheme of dynamically adjusting the number of coyotes in groups.Enlightened by the best strategy and Gaussian distribution in the global best harmony search algorithm proposed by Omran et al.37, we make an improvement to the growth of coyotes in groups and put forward a Gaussian global best growth operator.This intends to improve the social fitness of coyotes after growing up, enhance the information sharing between groups,and speed up the convergence of the algorithm.The global best operator makes full use of the state information of the global best coyotes in the coyote pack.It helps coyotes grow toward such global best coyotes,so as to enhance the mining capability.Meanwhile, the information in each group can be shared with other groups by virtue of a global best solution.A Gaussian distribution is also known as normal distribution.Compared with the uniformly random distribution [0,1] in COA, it can widen the search range and improve the global search capability to some extent.For the growth of coyotes in groups, best operator and Gaussian distribution random factor are introduced into Eq.(18) to obtain Eqs.(44) and (45).
In Eq.(44),GP is the current global best coyote,and δ3represents the difference between any other randomly selected coyote (cr1 ) in the group and GP.In Eq.(45), rn1and rn2are the random numbers generated by the Gaussian (normal)distribution with the mean value 0 and the variance 1, respectively.Moreover, new soc1indicates the new state (new solution) generated when every coyote grows under the joint effect of δ2and δ3.
Based on Eqs.(44) and (45), search capability is improved at the early stage of searching compared with COA.This is attributed to the existence of greater differences between individuals and an increased range of the scaling factor(Gaussian random number).However, the search range shrinks during the late stage of searching because of reduced differences between individuals and the lower values of δ2and δ3.Regardless of the Gaussian random number, the mining capability is reinforced.Furthermore, a global best solution is adopted to enhance the mining capability.Meanwhile, the global best solution obtained in a group will exert an effect on the growth of coyotes in the next group.This information sharing can generate positive feedbacks, which greatly speeds up the convergence.In addition, the fitness and survival for the fittest coyotes are calculated in parallel for all the adult coyotes in the group, which improves the speed and stability of the algorithm.
The COA is poorly operable since it requires the adjustment to multiple parameters.Comparatively, the improved COA involves two parameters Ncand Np, that have a major impact on the optimization process.When N is fixed, if Ncis certain, Np=N/Nc.The greater Np, the lower Nc.Then, the growth process requires few operations,but the effect of a global solution increases group by group,resulting in high mining capability.In contrast,a lower Npleads to more operations for growth,and the effect of a global solution diminishes together with a decrease in mining capability.To improve the operability of COA, the parameters Npand Ncare dynamically adjusted in this paper.If N=100,Npand Ncmust be the factors of 100.According to Ref.38, each group has no more than 14 coyotes.Hence,Nccan be only four,five or ten.Moreover,Nccannot be less than three,since the growth of coyotes in a group requires at least three coyotes, including two randomly selected coyotes and the best coyote in the group.When Nc=4,the range of coyotes available is limited.For this reason, the most likely values of Ncmust be five or ten.
At the late stage of searching, Nc=5, so that Np= 20.Hence, there are many groups involved.This strengthens the positive feedback of the global solution, and improves the search capability.At the early stage of searching, Nc=10, so that Np=10.Because there are fewer groups,this undermines the positive feedback of the global solution, but enhances the global search capability.Consequently, dynamically adjusting the number of coyotes in a group can improve the operability and reach a better balance between exploration and mining.After dynamic adjustment, coyotes are randomly grouped, so that the expulsion and reception of coyotes by groups can be eliminated from the process.In other words,the parameter Pewill not be adjusted, resulting in better operability as well.
Additionally, the GWO algorithm is simplified.The GWO search is introduced in this paper to further address the problems of COA including inefficient search and easily falls into the local optimum.Hence,a simplified GWO search algorithm is put forward by integrating Eqs.(6)–(12) with in-group coyotes in COA.It is further simplified as presented in Eqs.(46)–(48).
In these equations,tempcrepresents the state of the cthcoyote in the current group; NX1, NX2and NX3indicate the growth of coyotes in the group under the guidance of GP,alpha, cult, respectively.As shown in these equations, the adjustable vector C in Eqs.(6)–(8)is removed.This can retain the advantages of GWO and overcome its limitations.In other words, removing C in the SGWO algorithm causes no adjustment to c1and no calculation of the vector.For this reason,the SGWO algorithm can improve the operability and lower the complexity of computation while guaranteeing the strong mining capability.For further simplification of calculation,SGWO searches for the best solution directly following the guidance of global best, in-group best, and median coyotes(in-group culture) in GWO.It does not require searching for the second and third best coyotes in the group.In this way,SGWO can be efficiently integrated with COA.For better understanding, the hierarchies of grey wolves in GWO and SGWO are compared as shown in Fig.4.
At last, ICOA and SGWO are organically integrated by the sinusoidal crossover strategy, in order to achieve a balance between exploration and mining in the growth of coyotes in the group.The goal of the crossover strategy is to obtain a new solution by making two solutions cross each other at a certain probability.When the probability is zero,the dimension values of two solutions are not exchanged.When the probability is 1, all the dimensions values of two solutions are exchanged.However,no new solution is generated in both situations.Thus,the crossover of two solutions can achieve the best effect only at an appropriate probability.The sinusoidal function probability model is used to achieve the satisfying exploration and mining.In other words,the sinusoidal function is employed to adaptively control the crossover probability CR (which fluctuates around 0.5 gently in the early phase,but dramatically in the late phase),which takes into account the diversity and convergence of coyotes in a group.39The probability is calculated by
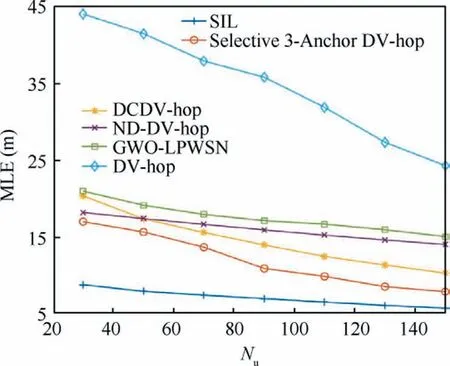
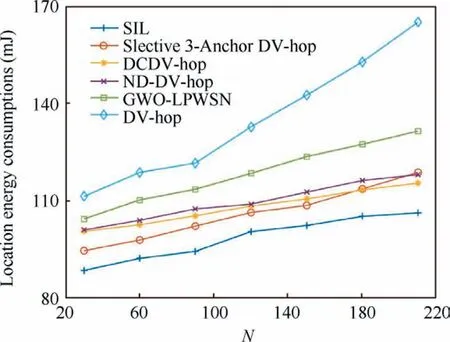
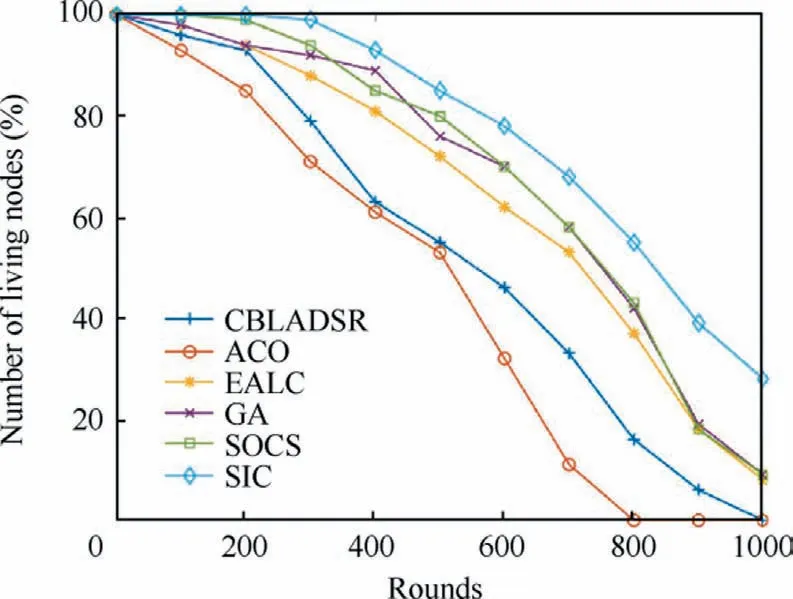
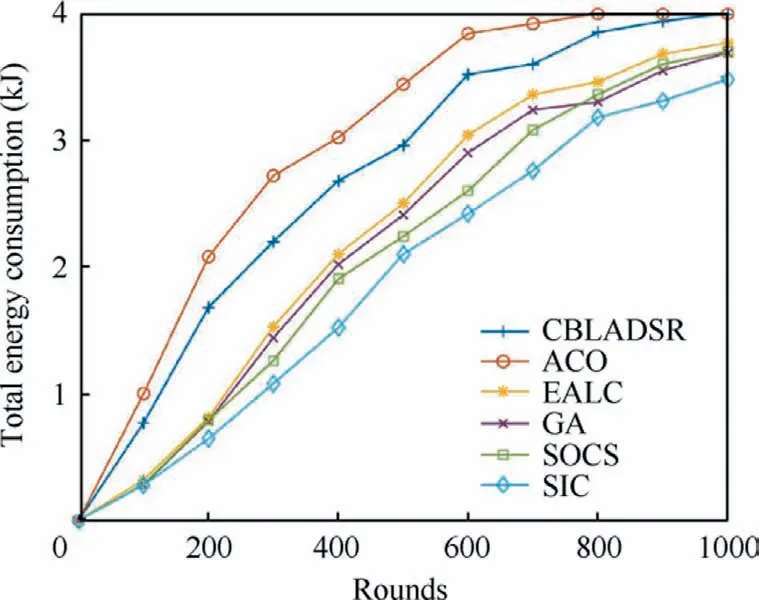
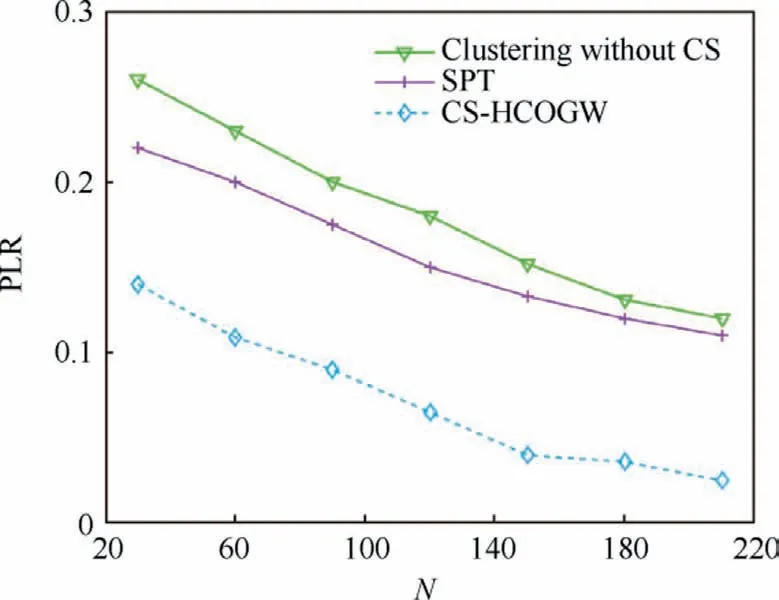
The sinusoidal crossover strategy used in this paper is as defined in Algorithm 3.At the probability with rand The HCOGW algorithm under the sinusoidal crossover strategy is as given in Algorithm 3. Algorithm 3.Hybrid coyote optimization with grey wolf optimizer(HCOGW); GP.Input: parameter CR, pack size Output: Global best solution GP 1.Let t = 0, and randomly initialize the coyote pack and assign coyotes to different groups 2.Calculate the social fitness of coyotes, and obtain the current global best coyote GP 3.while (t = 1 to MaxDT) do 4.for t = 1to MaxDT do 5.if t>MaxDT/2 6.Nc = 5 7.else 8.Nc = 10 9.end if 10.t = t + 1 11.Dynamically adjust the parameters e and CR based on Eqs.(5) and (49)12.Group randomly 13.Calculate the in-group best coyote alpha and the group culture cult based on Eqs.(16)–(18)14.Calculate the growth of coyotes in the group based on Eqs.(44) and (45)15.Select the cth coyote in the pth group 16.for j = 1 to D do 17.if rand < CR 18.Calculate Eqs.(46), (47), and (48)19 new /3 20.else 21.Adopt Eq.(45) with Gaussian global best growth operator(continued on next page)cj = NX1,j+NX2,j+NX3,j * (continued)Algorithm 3.Hybrid coyote optimization with grey wolf optimizer(HCOGW); GP.22.end if 23.end for 24.Conduct the parallel control of boundaries, and the parallel computation of social fitness for each coyote 25.Make a greedy choice to keep the best coyote and update the global best coyote GP 26.Randomly select the father coyote and the variation caused by environmental impact based on Eq.(21),and give birth to a new coyote.Calculate its social fitness, compare it with the oldest coyote with the poorest social fitness,and retain the better one 27.if the newborn coyote survives 28.age = 0, and update the global best coyote GP 29.else 30.The newborn coyote dies 31.end if 32.Update the age of coyote, age = age + 1 33.end for 34.end while 35.return GP The sinusoidal crossover strategy organically integrates two search methods to satisfactorily balance the exploration and mining capabilities during the growth process. As revealed in Algorithm 3, the HCOAG algorithm is different from COA in the following aspects.(A) The sinusoidal crossover strategy is integrated with the Gaussian global best growth operator and SGWO in the growth process.(B)Parallel computation is carried out for the fitness of coyotes in a group.(C) The parameters are dynamically adjusted.(D)The process of coyotes being expulsed and received by groups is discarded.In addition,the convergence analysis of HCOGW is described in detail in the appendix. Fig.5 Localization flow chart of SIL algorithm. As a method for breaking down a network structure,clustering is driven by multiple factors such as the task at hand,communication, calculations and resources.It is intended to balance the computational pressure among nodes, and to reasonably allocate the network resources.The nodes with better resources can undertake more computational tasks, so as to improve the stability of network.In ammunitions ad hoc network, clustering is crucial to the effective management of network topology.In this section, clustering and Cluster Head(CH)selection is a key step designed to lower energy consumption.This step is taken to balance the use of resources and extend the service life of the network.Additionally, a clustering scheme based on a coyote and grey wolf hybrid operation is proposed together with the CH selection algorithm and the efficient routing transmission algorithm. In the clustering scheme, loitering munitions are formed into several groups and distributed in the air.It is assumed that there are N loitering munitions in the area.The cluster set Csis defined as, where Nprepresents the number of clusters and Ncis the number of ammunition nodes in the cluster.The network diagram is defined as G(V,E) with V for the vertex set of ammunitions and E for the edge set.If the Signal-Noise Ratio (SNR) between ammunitions i and j is lower than the specified minimum threshold, i and j are neighboring nodes. This section particularly describes the channel model between ammunitions.A loitering munition is a ‘‘combination” of an Unmanned Aerial Vehicle (UAV) and a munition, so that its channel model is mainly based on the UAV to UAV (U2U)channel model for a UAV.When the ammunition node i transmits a signal to j, the power received by j from i can be expressed as where Pi,jrepresents the transmission energy from i to j;indicates the power gain of small fading channel;di,jis the distance between two nodes;γ stands for the average loss index on the path.The signal–noise ratio from i to j is: where NwGrepresents the additional Gaussian white noise.The U2U channel is normally controlled by the Line-of-Sight(LoS)link.Hence,the loss on the path from i to j may be regarded as the transmission in free space, and expressed as: where f0stands for the carrier frequency of the U2U channel,and csis the speed of light. Subsequently, a UAV to Base Station (U2BS) channel model is proposed in this paper.In this model,the channel link probably has a LoS or non-LoS (NLoS) link.The probability parameters include the height of the loitering munition and the angle of elevation between the loitering munition and the ground or ship base station.It is assumed that the height of ammunition is zi,and the distance from the estimated location of ammunition to the BS is ri,BS,so that the probability of LoS is defined by: where di,BSstands for the distance from i to BS; φ and ψ1are the parameters related to air conditions.The loss on the path between i and BS is expressed as: where ς is the loss index on the path; f0stands for the carrier frequency; csis the speed of light; ϱLoSand ϱNLoSare the additional path loss with LoS and NLoS, respectively. The energy consumption of nodes occurs mainly in the process of transmitting and receiving signals.In this section, the same energy model as described in Ref.40 is adopted, that is, the free space multipath fading channel based on the distance d between the transmitter and the receiver.Moreover, the distance threshold for the transmission of 1-bit data is denoted by dth.Thus, energy consumption can be expressed as: where Eelecis the parameter of electronic energy consumption,which depends on the energy consumed per bit from the transmitter to the receiver; εfs∙d2and εfs∙d4are the energy of the amplifier in two situations, and their values depend on d.The energy consumption of receiving 1-bit data is: It is assumed that the average number of clusters in the entire munitions ad hoc network is Np;the average energy consumed by each cluster is ENp; the average number of nodes in each cluster is N/Npwith N the total number of nodes.The average energy consumed by one round of communication is defined by: where cgrstands for the mass parameter of the communication channel.The average energy consumption of each cluster is: where ECHis the energy consumption of cluster head; ECMfsand ECMmprepresent the energy consumed by Cluster Member(CM) nodes in the free space and multipath amplification model, respectively; Γ and 1-Γ stand for the fraction of member nodes transmitted by the free space and multipath models, respectively.Hence, ECHcan be expressed as: where dBSis the average distance from the CH node to the base station.Moreover, ECMfsand ECMmpare defined by: where dCHfsand dCHmprepresent the average distance from CM to its corresponding CH in the free space and multipath models,respectively.With regard to d ≥dthin Eqs.(56),(60),(61)and (62) are simultaneously solved to obtain: Eq.(58) is substituted into Eq.(63) to obtain: Normally,the total energy consumption of an ad hoc network depends on the number of clusters in the network.The optimal number of clusters should be chosen to lower energy consumption and achieve a balanced network.Thus, a mathematical model will be built to determine the optimal number of clusters in this section.The volume of the cubic network area in the air is defined by: where M is the length of such cubic network area.The average volume occupied by each cluster is determined by: The cluster area can be expressed as fXYZ(x,y,z).Let the position of CH be the centroid of the cluster area.The estimated spatial distance from a node to CH is calculated by: Assuming that the cluster area is spherical, fRθf(r,θ,φ) is a constant of the cluster area.The radius of such sphere and the density of nodes can be expressed as: Then, Eq.(67) may be rewritten into: Eq.(70) is substituted into Eq.(64) to obtain the optimal number of clusters Nopt p in the ad hoc network as follows: The probability of selecting the optimal number of CHs is defined by: In this section,the HCOGW algorithm is adopted for the clustering of the munitions ad hoc network.The goal is to assign N ammunition nodes to the preset or optimal number of clusters.The correlation between wolf pack and ammunition clusters is presented in Table 1. In the clustering process,the nodes with the shortest Euclidean distance are assigned to the same cluster.This ensures the shortest distance of data transmission and reduces the energy consumption.Nevertheless, it is very difficult to locate the nodes in a highly dynamic topological situation such as ammunition networking.To resolve such a difficulty, the HCOGW algorithm was developed to measure the distance between nodes.First,the sum of square errors in Eq.(74)is minimized to determine the geographical position of ammunition for grouping: Table 1 Similarity between wolf packs and ammunition clusters. Algorithm 5.Clustering Based on HCOGW.Input: Number of clusters Noptp and wolf pack size U Output: The final centroid position of each cluster Cg,g = 1,2,..., M 1.Initialize the position of wolf pack U= U1,...,Uw,...,UW[]2.Initialize the parameters α and CR 3.Initialize the number of clusters Cg ←∅4.repeat 5.Cg ←C′g 6.for each wolf w=1,2,...,W do ■do 8.Update the wolf-to-cluster association using Table 1 9.end for 10.end for 11.while(t=1 to MaxDT)do 12.for each wolf w=1 to W do 13.for each wolf, h=1 to D do 14.Update the position of each wolf defined by Eq.(12).15.Evaluate the new position of wolf w defined by Eq.(75).16.Update the values of (α, CR)17.Calculate the in-group best wolf alpha and in-group culture cult 18.Use Eqs.(44) and (45) to calculate the growth of coyotes in each group 19.Use the Gaussian best growth operator for the growth of some coyotes, and the simplified grey wolf optimization algorithm for the other coyotes in a group, based on the sinusoidal crossover strategy 20.Calculate the social fitness of each coyote, and conduct the greedy selection to retain the best coyote and update the global best coyote GP 21.Randomly select the father coyote and the variation under environmental impact to generate a newborn coyote based on Eq.(21), calculate its social fitness, and determine its life or death 22.Update the age of coyote and the global best coyote GP 23.end for 24.end for 25.t=t+1 26.end while 27.Return GP /*the position of GP is the final centroid position*/28.until (Cg =C′g) /*no change in the cluster centroids */■7.for each cluster Noptp = C1,C2,...,Cg,...,CM In this section, the HGWO algorithm is mainly adopted to select the CH of the network as given in Algorithm 3.In Algorithm 6,the best solution is GP.In the first round,the position of wolf is updated with Eqs.(46)–(48).Subsequently,the position of wolf is updated using the fitness.The fitness is determined as follows: Fig.6 Flowchart of SIC algorithm. Case 1. Case 2. Case 3. where k stands for the number of iterations, and fit0indicates the poorest fitness. Case 4. In the CH selection, several fitness functions are normally employed in a bid to maximize the fitness function.The fitness model mainly takes into account such functions as In-Cluster Distance (ICD), Number of Neighboring nodes (NoN), and Remaining Power of ammunition node (RP): where three coefficients coef1,coef2and coef3are 0.2,0.3, and 0.5, respectively, in terms of their priority.The average distance from the node of a coyote to the initial CH is the fitness function (ICD), which is defined by: where‖Un-CHg‖denotes the distance from the node of the coyote to the cluster head CHg,and Ngindicates the number of ammunition nodes in the cluster with CHmas its cluster head.The NoN function of fitness is expressed as: where ERCHgstands for the remaining power level of the current cluster head CHg, 1 ≤g ≤M.The cluster selection process is detailed in Algorithm 6. Algorithm 6.CH Selection Based on HGWO.Input: Cluster Cg and wolf pack size U Output: Cluster head CHg, g = 1,2,..., M 1.Initialize the position of wolf pack U= U1,...,Uw,...,UW[]2.Initialize the parameters e and CR 3.Calculate the fitness (fit) of each coyote 4.Choose the three best solutions Uhw,GP,Uhw,alpha, and Uhw,cult 5.while (t++ The cluster maintenance strategy adopted in this paper is classified into intra- and inter-cluster topology maintenance. (1) Intra-cluster topology maintenance In a clustered network model, the intra-cluster topological structure may be changed by adding a new node into the network, having an interrupted link between CH and member nodes, or changing the CH node of the cluster. (A) Adding a new node into the network As shown in Fig.7, a new node continuously broadcasts a request message for joining to the network.After receiving such a message, the CH node determines whether to accept the new node according to Algorithm 5.If rejected, the new node continues to broadcast.If accepted, the new node will receive a reply message from the CH node.The new node will send a joining message to the CH node.After the new node joins the cluster, Algorithm 6 is used to judge whether the new node becomes a new CH node.If not, the CH node will renew the member list of the cluster.If yes, the new node will broadcast the Chead message of its becoming the CH node to others. (B) Link interruption If a CH node j in the network broadcasts the Chead message,but does not receive the Renew data packet from a node i in the cluster’s member list,or the member node i in the cluster does not receive the Chead packet broadcasted by the CH node j after the time t, the member node i and the CH node j conclude that their link has been interrupted.The specific maintenance strategy is as follows: Fig.7 Intra-cluster topology maintenance for adding a new node to the network. Fig.8 shows how a member node i, whose link to the CH node j is interrupted makes an attempt to join another cluster.If the node i does not receive the Chead message from the current CH node, it will broadcast a request message.Another CH node determines whether to accept the node according to the clustering algorithm.If yes, the CH node sends a reply message to the node.After the node confirms joining the cluster,it officially joins the cluster.If no reply is received from the CH node, the node will be regarded as an invalid node. (C) Changing CH of a cluster Because of different motion speeds and remaining energies of nodes in the network, some CH nodes may become incompetent after a while.The procedure of topology maintenance for changing a CH node is illustrated in Fig.9. As shown in Fig.9, the CH node broadcasts the Chead message to the member nodes of the cluster in periods t.After receiving the Renew data of member nodes, the CH node renews the member list.The proposed cluster selection algorithm is used to judge whether to generate a new cluster head.If yes,the node is elected as the new cluster head.Then the new cluster head begins to broadcast the Chead message and renew the member list. (2) Inter-cluster topology maintenance The inter-cluster topological structure may be changed for the following reasons: a member node moves from a cluster to another cluster, causing the structural change of both clusters; a CH node moves into the communications coverage of another CH node,resulting in the massive overlapping of both clusters. (A)A member node moves from a cluster to another cluster At this moment,the member node moves to a new position.The value from Eq.(74)is taken to find out whether it satisfies the requirements of minimization.If not, the node is guided outside the boundary of the cluster through Eq.(75).The node sends a request message for joining to another CH node.The CH node determines whether to accept the node according to the proposed clustering algorithm.If yes, the CH node replies to the node, and the node joins the cluster after giving a response.The specific maintenance procedure is given in Fig.10. (B) A CH node moves into the coverage of another CH node With the motion of CH nodes,a CH node may easily move into the communications coverage of another CH node.In this case, the cluster and CH must be renewed according to Algorithms 5 and 6. Transmission-efficient routing means that the routing involves the lowest number of transmissions.A wireless ad hoc network is characterized by the equality of nodes since there is not a central architecture.Therefore, any node is capable of forwarding, integrating and computing information, and will not affect the entire network if it fails. If two nodes are far away from and unable to communicate directly with each other, they may forward the control and data messages through a multi-hop relay to complete the entire communication process.Nevertheless, this process is troubled by long time delay and massive amounts of data transmission.Especially in a loitering munition ad hoc network,ammunition nodes need to transmit the information obtained from reconnaissance in the frontier to the ground base station, and then gather the information on the overall situation.This may drain the battery in the ammunition very quickly.Therefore,a Compressed Sensing scheme based on HCOGW (CS-HCOGW) is introduced in this paper for the ad hoc network of ammunitions.This scheme can considerably reduce the number of data transmissions to balance the load of data flow in the entire network.If CS-HCOGW is not used,the nodes of a cluster member often transmit data to their cluster head. A minimum cost algorithm is developed to connect all CHs to the base station.The cost is represented by the number of hops.These CHs use such backbone routing path to transmit data to the base station. Fig.8 Intra-cluster topology maintenance for link interruption. Fig.9 Topology maintenance for changing cluster head of a cluster. In the GWO algorithm, the backbone routing path is updated by the fitness of nodes.Enlightened by the GWO algorithm, we classify all nodes into three categories, that is,GP,alpha and cult,and use them to construct the main frame tree.The routing scheme is presented in Fig.11. Fig.10 Topology maintenance for moving a node between clusters. Fig.11 Example of transmission-efficient routing: BS, base station; CH1 to CH4, cluster heads 1 to 4; CM, cluster members. The CS-HCOGW routing is as shown in Algorithm 7.In Rows 1–4, the position of a wolf is assumed to be the matrix Ui×jwith i as the number of wolves, and j as the joint sparse Kl.Each matrix has a randomly selected integer [1,Nl] with Nlrepresenting the number of columns in Φ.Moreover, R stands for the support set of the column ΦT,which is initialized at the beginning of the algorithm.Three wolves with the best performance in the vector (1×Kl) are denoted by UGP,Ualpha,and Ucult.In the fourth row,the three best fitness values are initialized.Then initialization parameters are updated at all positions.For each row i in the matrix U,a search set C1is created, and.Subsequently, the submatrix ΦCis created from the CS matrix Φ in Rows 6–12.In the 13th row,the sub-matrix L is created,and L=ΦIis a column of the matrix Φ.The cost function measured by the fitness fit( L ) is as follows: Rows 15–23 are used to find the best wolf.Among them,are three best solutions.At last, the position of the wolf is updated by Algorithm 4. ? The proposed SIL and SIC algorithms are based on the HCOGW algorithm.The computational complexity of HCOGW can be expressed by O(W ∙kd∙MaxDT), where W stands for population size; kdis the dimensions of space; and MaxDT indicates the largest number of iterations.The computational complexity of HCOGW varies in three phases.In the first phase of population initialization, the complexity is O(W ∙kd).In the second phase, the fitness of all nodes is calculated, so that the complexity is O(W ∙kd∙MaxDT).In the third phase, the population location is updated in two stages,that is, crossover and variation.The complexity in the phase is O(W ∙kd∙MaxDT).The overall complexity is therefore O(W ∙kd∙(2MaxDT+1)). Since the SIL process is dominated by the HCOGW algorithm, its computation complexity is also O(W ∙kd∙(2MaxDT+1)).The SIL process has the same complexity as the CS-HCOGW process.In the phase of initialization, the algorithm complexity is O(W ∙kd).Thereafter, it takes time to update three optimal positions in each iteration,so that the complexity O(W ∙kd).After reaching the largest number of iterations, the overall complexity of the algorithm is O(W ∙kd∙MaxDT). The proposed SIL and SIC algorithms were used in a simulation experiment with MATLAB to evaluate their performance in various scenarios.The performance of the SIL algorithm was first tested and compared with that of selective 3-anchor DV-hop, DCDV-Hop, ND-DV-Hop, GWO-LPWSN and DV-hop.Subsequently, the performance of the SIC algorithm was evaluated and compared with that of CBLADSR, ACO,EALC, GA and SOCS. Note: CBR, defined; IEEE, Institute of Electrical and Electronic Engineers; LoS, line-of-sight; MAC, defined; NLos,non-LOS; SINR, defined; U2U, Unmanned Aerial Vehicle(UHV) to UHV. The simulation environment settings in this paper is shown in Table 2.In the set network coverage area,the moving speed of the loitering munitions is 0–100 m/s, and the direction ranges between 0–360°.A simple loitering munitions motion model is established.The maximum velocity component of the nodes is denoted by vmax.At the time t, the coordinates of the node can be defined as: where rand is an evenly distributed random number and rand ~U(-1,1). In a satellite denied environment, the satellite signal receiver carried by the loitering munitions is normally unable to receive the navigation signals.The anchor nodes can only be the nodes of the munitions equipped with the additional signal receiving device.These nodes can receive the absolute position messages from the BS through the tactical data link.However,not all nodes are equipped with the additional signal receiving device for the purpose of small size and low cost.In the simulation process, a certain proportion of loitering munitions nodes with absolute coordinates (i.e.anchor nodes) are launched considering the practical environment of a battlefield.However, the cost will be dramatically increased by a large number of anchor nodes.According to Ref.41, the anchor nodes are therefore evenly distributed in the network,and take up 20% of total nodes.The goal is to reduce the localization error and achieve the reasonable cost control. Performance evaluation was conducted with some typical indicators such as Mean Location Error (MLE), localization success rate,and localization time of each node.The performance of several localizing algorithms is summarized in Table 3.Evidently, the SIL algorithm has the best localization accuracy.Its MLE is 6.52 m, which satisfies the requirements for accuracy under the massive networking conditions of loitering munitions.This algorithm can locate more nodes in the same period than other algorithms, so that it is timelier than the others.In addition, the SIL algorithm is characterized by a lower number of iterations, which reduces the complexity of computation and saves the energy of localization. In the localization of unknown nodes, the SIL algorithm performs better than other algorithms.This fact must beattributed to shortened localization since the bounding cubes are constructed to reduce the initial search space.Additionally,sinusoidal crossover strategy is integrated with Gaussian global best and simplified GWO in the growth process.The HCOGW algorithm facilitates the identification of unknown nodes, and optimizes their coordinates.The mining capability of COA is considerably improved while enhancing the capability of global search for coyote life and death.In other words,Gaussian best growth and GWO search in the HCOGW algorithm utilize the global best coyote as the guide to better obtain the global optimal solution.Then this global optimal solution plays a role in the growth of the next coyote group.In this way, a positive feedback mechanism is formed. Table 2 Simulation parameter settings. Meanwhile,two common network structures are selected in this paper, that is, uniformly random distribution and Ushaped distribution.Fig.12 presents the distribution of actual locations in two networks with the DV-hop and SIL algorithms.Evidently, the proposed SIL algorithm considerably improves the localization accuracy. (1) Mean Location Error(MLE)affected by the number of unknown nodes As shown in Fig.13, an increasing number of unknown nodes reduces localization error.More nodes contain more anchor nodes, which helps improve the accuracy of localization.Meanwhile,more and more unknown nodes are localized and then taken as anchor nodes in the localization of other unknown nodes.As shown in Fig.13,the SIL algorithm keeps the lowest MLE. (2) MLE affected by the number of anchor nodes Fig.14 shows the decrease of MLE with the increasing number of anchor nodes.When there are more anchor nodes,the distances from anchor nodes to unknown nodes are shortened, causing the decrease of MLE in all algorithms.Among them, the SIL algorithm has the best performance since the bounding cubes are created to improve the validity of samples. (3) Energy consumption of localization Fig.12 Localization results in two networks with DV-hop and SIL. Fig.13 MLE varying with the number of unknown nodes. In Fig.15, the proposed SIL algorithm has the lowest energy consumption in the localization of nodes compared with other algorithms.This must be attributed to two factors.First, the SIL algorithm needs fewer anchor nodes to localize more unknown nodes.In other algorithms, an anchor node can transmit its location as soon as it falls into the communication range.However, the SIL algorithm requests an anchor node to broadcast its location only, since the location update,optimization and hop count of nodes are performed at each target node.Moreover, the communication cost is calculated by the number of transmitted control data packets in the process of collaborative localization.Hence,the energy consumption of the SIL algorithm is significantly reduced.Second, the SIL algorithm converges very fast, which is a major cause for reduced energy consumption. In this section, the performance of the clustering algorithm is comparatively analyzed.The optimized clustering algorithm based on HCOGW is compared with the common clustering algorithms based on swarm intelligence optimization including CBLADSR,29ACO,30EALC,31GA32and SOCS.33The results are then analyzed. (1) Number of clusters As for clustering algorithms, the number of clusters is highly decisive to the energy consumption of a network.Having an optimal number of clusters can effectively reduce the energy consumption.Fig.16 demonstrates the correlation between the number of clusters and the total number of nodes,revealing that the performance of the proposed algorithm SIC is noticeably better than other clustering algorithms because it can realize a small number of clusters.A model is built to analyze the optimal number of clusters for the minimum energy consumption of the network.The lower number of nodes in a cluster implies more clusters exist.More nodes in a cluster increase the data transmission within the cluster.In other words,if the number of clusters is not optimal,some nodes will not be assigned to clusters, and even a single node becomes a cluster,which increases the number of clusters significantly.To optimize the number of clusters, the proposed SIC clustering scheme can prevent a single node from becoming a cluster,and optimize the network topology. (2) Cluster building time Fig.14 MLE varying with the number of anchor nodes. Fig.15 Energy consumption comparison of algorithms. Cluster building time refers to the time needed by the clustering algorithm for CH selection and cluster generation.It exerts an effect on the computation complexity of the clustering algorithm.In the clustering process, each CH node broadcasts a message and declares itself as the CH in the network at the beginning of each round.The other nodes in the cluster broadcast their own position and remaining energy.In the SIC algorithm, the number of transmitted control packets depends on the CH selection and the distance between each node and the BS.Because it takes more time to build a cluster,cluster building will consume a tremendous amount of energy and shorten the service life of the network.The battery in a loitering munition contains limited energy, so that the cluster building time must be short.China Ordnance Academy and Xi’an Institute of Modern Control Technology released the key technical indicators of the intelligent munitions cluster network.Accordingly,the networking is similar between loitering munitions and unmanned aerial vehicles in a battlefield,so that the networking time of loitering munitions should be less than 60 s(which is needed for the cluster to form a relatively stable structure and allow the normal communications between clusters).42The proposed SIC algorithm has a cluster building time not exceeding 30 s even with the increasing number of nodes,so that it satisfies the requirement for the networking time in a battlefield. Fig.16 Number of clusters and total number of nodes in six algorithms. As shown in Fig.17, the SIC algorithm needs the shortest cluster building time with the increasing number of nodes in the network compared with the other five algorithms.This must be attributed to the improved COA in the HCOGW algorithm, which prevents the coyote pack from being trapped in local optimum.In this way, CH and relay nodes are obtained by the SIC algorithm to save more energy.As a result,the SIC algorithm features shorter cluster building time and reduced routing selection delay. (3) Number of living nodes After each round,some loitering munitions will be disabled when their batteries run out.Fig.18 shows a variation curve formed by the percentage of living nodes and the service life of the network.It is evident that the SIC algorithm keeps a larger number of living nodes than other algorithms after the same rounds, implying a more stable network.Meanwhile, it is also proved that the proposed SIC algorithm consumes the least energy among these six algorithms. (4) Total energy consumption The comparison of the SIC algorithm with the other five algorithms in terms of total energy consumption is illustrated in Fig.19.The SIC algorithm is obviously superior to other algorithms, which must be attributed to its optimal clustering and optimal number of clusters. (5) CH duration The life of a cluster is how long it takes for the cluster to form and reshuffle.Cluster life is an indicator of the cluster’s stability,and depends on the duration of the CH.After selecting a CH, the CH is responsible for its own cluster.Hence, a CH node plays a more important role than other nodes.In the meanwhile, the fitness of the CH node diminishes with the time.The CH node will be incompetent after its fitness reaches a certain threshold.As shown in Fig.20, the duration of the CH for all algorithms decreases with the increasing number of nodes.This fact must be attributed to the frequent clustering since the fast motion of nodes constantly causes the change of the network’s topological structure.Evidently, the cluster life under the SIC, SOCS and GA algorithms is much longer than that under the ACO,EALC and CBLADSR algorithms.In general,the SIC algorithm has the best performance in terms of cluster life. Fig.17 Correlation between cluster building time and total number of nodes. Fig.18 Variation of number of living nodes with rounds. (6) Packet loss rate The Packet Loss Rate(PLR)refers to the proportion of the data packets lost in the transmission in the total packets transmitted.It is normally tested within the throughput.The PLR is associated with the packet length and the transmission frequency.Fig.21 shows the variation of PLR with the number of nodes under several clustering protocols.As revealed in Fig.22,the PLR of SLC is within 5%,regardless of additional nodes in the transmitted data.With the increase of ammunition nodes, SIC has retained the best performance under the centralized routing protocol.Moreover, CBLDASR, ACO,and SOCS have similar performance,while the clustering routing based on GA performs better than EALC. This section presents a simulation experiment for the performance of CS-HCOGW routing.The loitering munitions nodes are assigned to several clusters.Each cluster has a CH.Fig.22 shows the clustering of nodes and the data transmission path under 2D conditions.In the figure, the CH and BS are represented by a red square and triangle,respectively and a red link indicates the shortest routing path from a CH to the BS for the inter-cluster transmission link. Fig.19 Variation of total energy consumption with rounds. Fig.20 Variation of cluster head duration with a change in the number of nodes. In most cluster routing algorithms,each CH node transmits data to the BS or the nearest CH.In a dynamic ad hoc network,the distance between CHs may be long,which consumes much energy to maintain data transmission.Meanwhile, the rapid movement of nodes makes it very difficult to maintain the link between CHs.The proposed algorithm CS-HCOGW uses relay nodes to transmit data to other CHs and the BS.It can lower the load of CHs,while extending their service life.Furthermore,the CH nodes near the BS become deceased prematurely because of‘‘shortest path routing”in the mainstream clustering methods, which leads to a routing loophole problem.In CS-HCOGW,CM nodes are taken as relay to transmit data to the BS, so as to achieve an energy balance between nodes. As shown in Fig.23, CS-HCOGW is compared with the clustering algorithm without CS and the Shortest Path Tree(SPT) algorithm.It is revealed that CS-HCOGW obviously needs a much lower number of transmissions than the other two algorithms.Among them, the proposed routing scheme requires a lower number of transmissions than the clustering scheme without CS.The proposed algorithm CS-HCOGW employs the CS technique for compression of CHs, reducing the number of transmissions.The inter-cluster data transmission is conducted through the main routing tree.Moreover,the proposed algorithm needs a lower number of transmissions than the SPT algorithm because of its cluster structure.In the proposed algorithm, CM nodes transmit data to the corresponding CH that is often at the center of a cluster.However,the nodes in SPT normally transmit data to the nodes adjacent to BS. Fig.21 Variation of PLR with the number of nodes. Fig.22 Data transmission path of a compressed sensing algorithm based on a hybrid coyote optimization algorithm with a grey wolf optimizer routing. At last, three routing algorithms are compared in terms of PLR as shown in Fig.24.The PLR of CS-HCOGW routing algorithm is noticeably lower than that of the other routing algorithms for two reasons.First, CS technology is adopted in the proposed algorithm, which reduces the quantity of data transmitted.Secondly, taking the member nodes as the information relay does not rely only on the CHs for data transmission.The PLR is therefore reduced because of lower pressure on CHs. Fig.23 Variation of the number of transmissions with the number of nodes. Fig.24 Variation of packet loss rate with the number of nodes. This paper addresses the clustering and localizing problem of a loitering munitions ad hoc network in the air under satellite denied conditions.For this purpose, the SIL and SIC algorithms are proposed.In the SIL algorithm, bounding cubes are created to reduce the initial search space, so as to improve sampling efficiency and lower computational cost.Subsequently, the HCOGW algorithm is taken to solve the coordinates of unknown nodes.The proposed algorithms are compared with some popular algorithms including selective 3-Anchor DV-hop, DCDV-Hop, ND-DV-Hop, and GWOLPWSN,as well as the traditional algorithm DV-hop.In summary,the proposed algorithms deliver more accurate localization and faster convergence for large ammunition networks,and achieve better numerical stability and robustness for the networks with a highly dynamic topological structure.In the SIC context, a Hybrid Coyote Optimization algorithm with a Grey Wolf optimizer (HCOGW) based on a sinusoidal crossover strategy is proposed and applied in the clustering process of the ad hoc network.Energy consumption can be reduced since the SIC takes into account a number of problems including the number of clusters, cluster size, cluster stability, and number of transmissions.Compared with popular algorithms such as CBLADSR, ACO, EALC, GA, and SOCS, the SIC algorithm demonstrates the best performance in terms of cluster building time, number of clusters, service life of clusters,and energy consumption.In the end,the CS-HCOGW routing is proposed to reduce the number of data transmissions in the loitering munitions ad hoc network. The present study has some limitations.First, because the munitions nodes are far away from the base station,this paper proposes a compressed sensing method based on multi-hop communications to reduce the transmission power of the nodes.However, due to the multi-hop communication, the number of hops for data transmission from each cluster head to the base station in this method may increase, and we will improve the performance of the loitering munitions network by multiple antennas in the future.Second,this paper is mainly simulated by MATLAB,and there may be some shortcomings in the parameter setting and other aspects,so we will consider adopting network simulation software or semi-physical object to carry out the simulation in the future. Declaration of Competing Interest The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper. Appendix A.This section presents the convergence analysis of the HCOGW algorithm. Following the principles of random functional analysis given in Ref.43, the convergence of the HCOGW algorithm is analyzed.Based on the description of Algorithm 3 and the flow chart of the HCOGW algorithm in Fig.6,three operators are used to generate new solutions, that is, a Gaussian global best growth operator, a simplified GWO search algorithm,and a life-or-death operator.The Gaussian global best growth operator is similar to the DE/rand-to-best/1/bin mutation operator of Differential Evolution(DE),42while the simplified GWO search algorithm acts like the DE/best/1/bin mutation operator of DE.The life-or-death operator is equivalent to the mutation operator of a genetic algorithm.New solutions are processed with the greedy algorithm following the survival-of-the-fittest strategy.They are compared with the original solution to preserve the better solution.For the minimum optimization problem,the HCOGW evaluation function sequence is monotonically non-increasing.In order to prove the convergence of the HCOGW algorithm,the following definition is first given: Definition 1.It is assumed that Q(t) represents the intermediate group of X(t), Vc,j(t+1)∊Q(t+1), so that the HCOGW search operators are defined as follows: The Gaussian global best growth operator and the simplified GWO search operator are defined by The life-or-death operator is defined by Assuming that f1(X)is the minimum optimization function,the solution spaceand Lj≤xj≤Uj,j=1,2,...,D} is a bounded subspace of a D-dimensional Euclidean space RD. Definition 2.The hybrid strategy of two operators means using the simplified GWO search operator and the Gaussian global best growth operator for each component of the individual vectors in a population at the probability CR/D and (1-CR/D), respectively.Each group is reshuffled and transformed with the life-or-death operator to identify the poorest coyote.Therefore, it is a random mapping in the solution space,ψ1:Ω×S →S2, and can be defined by: where(Ω,M1,μ1)is a complete probability measure space;Ω is a non-empty abstract set with its elements ω1as the basic events; M1is the σ-algebra formed by some subsets; μ1is the probability measure of M1.Moreover, Xmoddenotes that a coyote is GP or alpha or cult, and F (X, Xc, Xj, Xk, Xmod) is determined by Eqs.(A1) and (A2). Like DE,the HCOGW algorithm uses the greedy algorithm to update the population.In each iteration, the current population is subject to the mapping ψ′, resulting from the random mapping ψ1of the three operators and the mapping reversal ψ2of the greedy choice.Therefore, there is.Under the effect of the mapping ψ′, the fitness of GP in each iteration of the HCOGW algorithm forms a monotonically non-increasing sequence {f1(XGP(t ))}1≤t≤MaxDT.Similarly, ψ′can be further redefined as Bt+1=ψ′(ω1,Bt)=ψ2(ψ1(ω1, Bt)), where Bt+1and Btare the optimal individual of X(t+1)and X(t),respectively.Hence, the following theorem is obtained with Theorem 1 given in Ref.24: Theorem 1.The random mapping ψ′generated from one iteration of the HCOGW algorithm is a random compression algorithm. Based on Lemma 2 defined in Ref.24, it is concluded that the HCOGW algorithm is asymptotically convergent, which becomes Theorem 2. Theorem 2.If ψ′is a random compression operator for the HCOGW algorithm, ψ′has a unique random fixed point, so that the HCOGW algorithm is asymptotically convergent. While proving the asymptotic convergence of the HCOGW algorithm, a new solution is generated with three operators as specified in Ref.44.Among them, an operator similar to the mutation operator of DE has its global convergence as follows:Theorem 3.If λ1:S×S →RDis defined as the distance on S,and satisfiesis a complete separable metric space. In this similar way as given in Ref.44, Theorem 3 is easily proved. Any new group generated from each iteration of DE must be better than its father group.For the ψ′mapping generated by the HCOGW algorithm in Theorem 1, there is a variable 0 ≤K0<1,which is a non-negative real number, and makes: Based on Eqs.(A4)and(A5),ψ′mapping is a compression operator, which has an exclusive fixed point ξ with ψ′(ξ)=ξ. The sequence {Xi}(i=1,2,3 ∙∙∙) is the optimal solution obtained from the HCOGW algorithm after each iteration.As discussed before, {Xi} is a monotonically non-increasing sequence, and asymptotically convergent.At any initial state X0, the sequence {Xi} obtained after mapping always converges.According to the definition of convergence, {Xi} converges at the fixed point ξ.The fixed point is exclusive, so that the mapping of the HCOGW algorithm is globally converge.Additionally, {Xi} is a monotonically non-increasing sequence, and certainly converges into the global optimal solution.


4.Energy-efficient swarm intelligence based clustering algorithm SIC
4.1.System model
4.2.Channel model
4.3.Energy consumption of cluster head
4.4.Optimal number of clusters
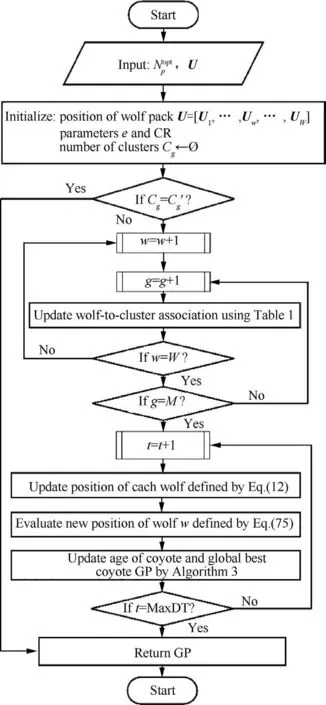
4.5.Clustering algorithm



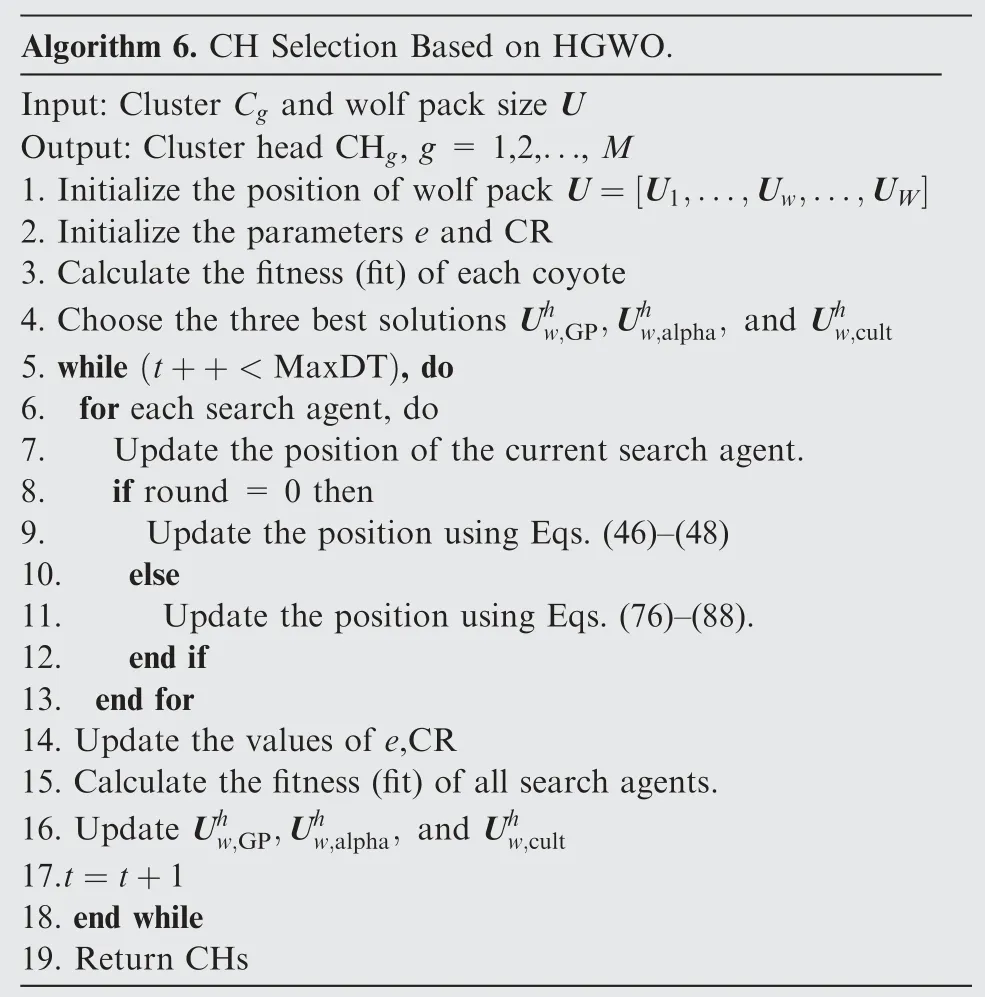
4.6.Cluster head selection
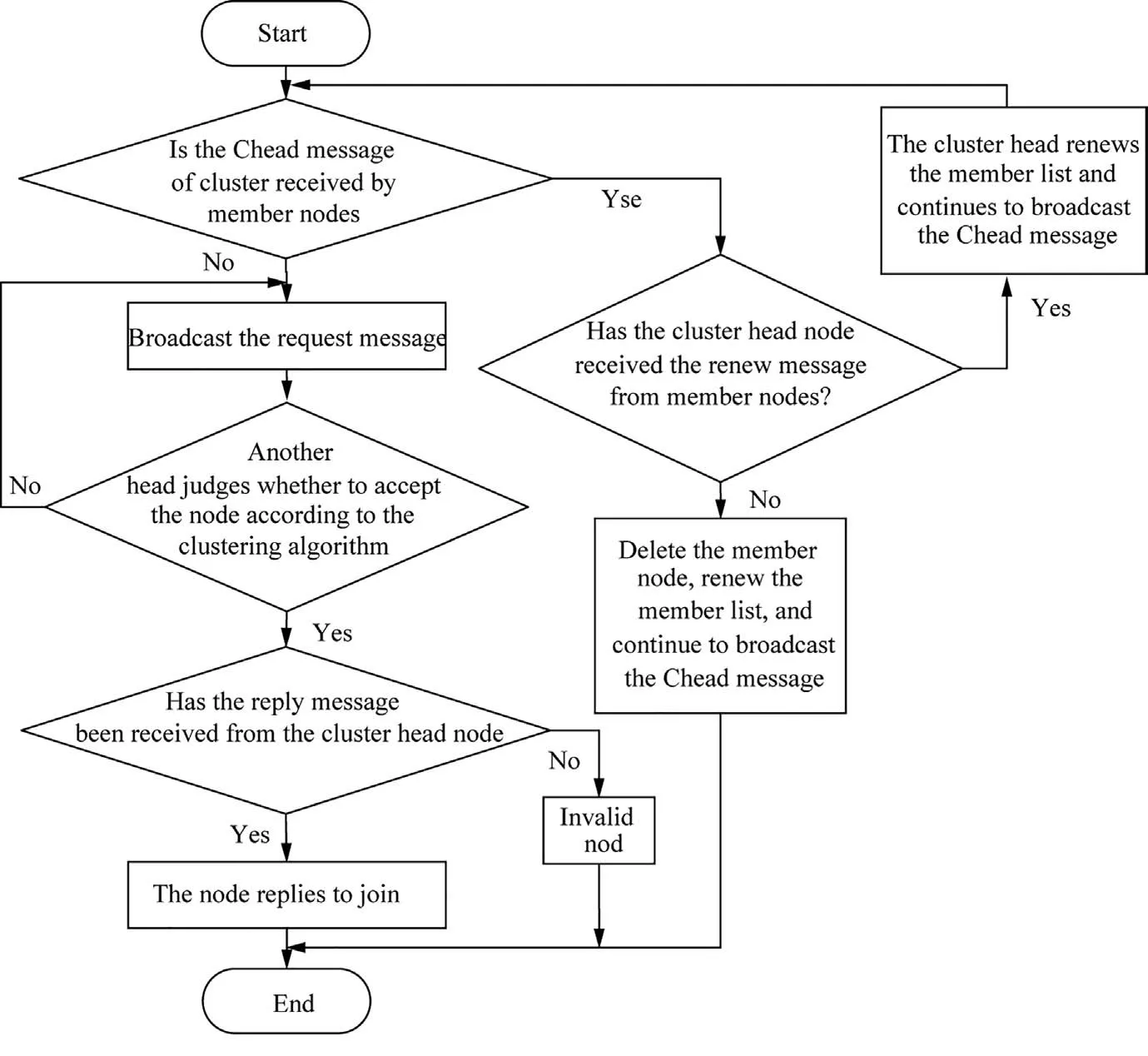
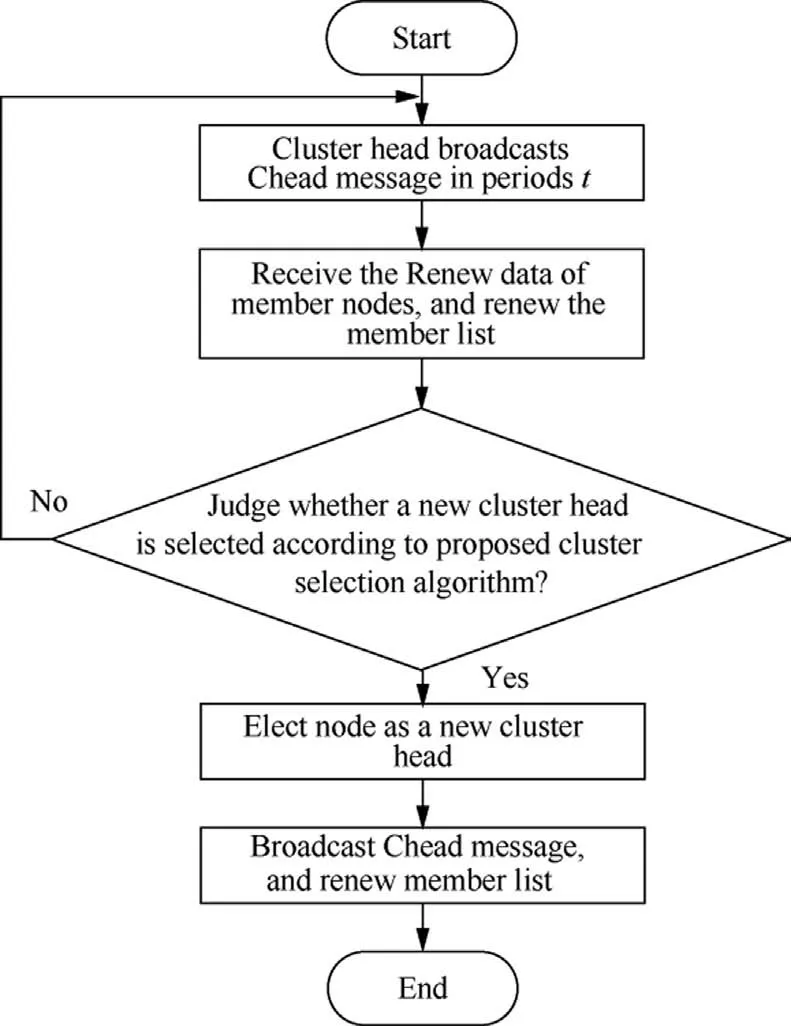
4.7.Cluster maintenance
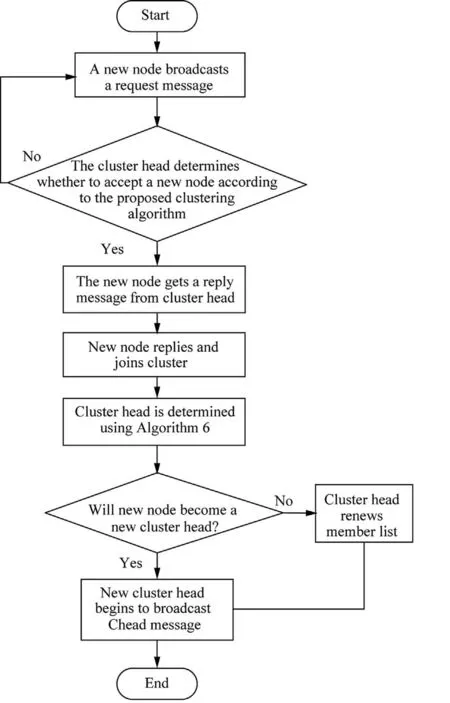
4.8.Transmission-efficient routing




4.9.Computation complexity analysis
5.Performance evaluation
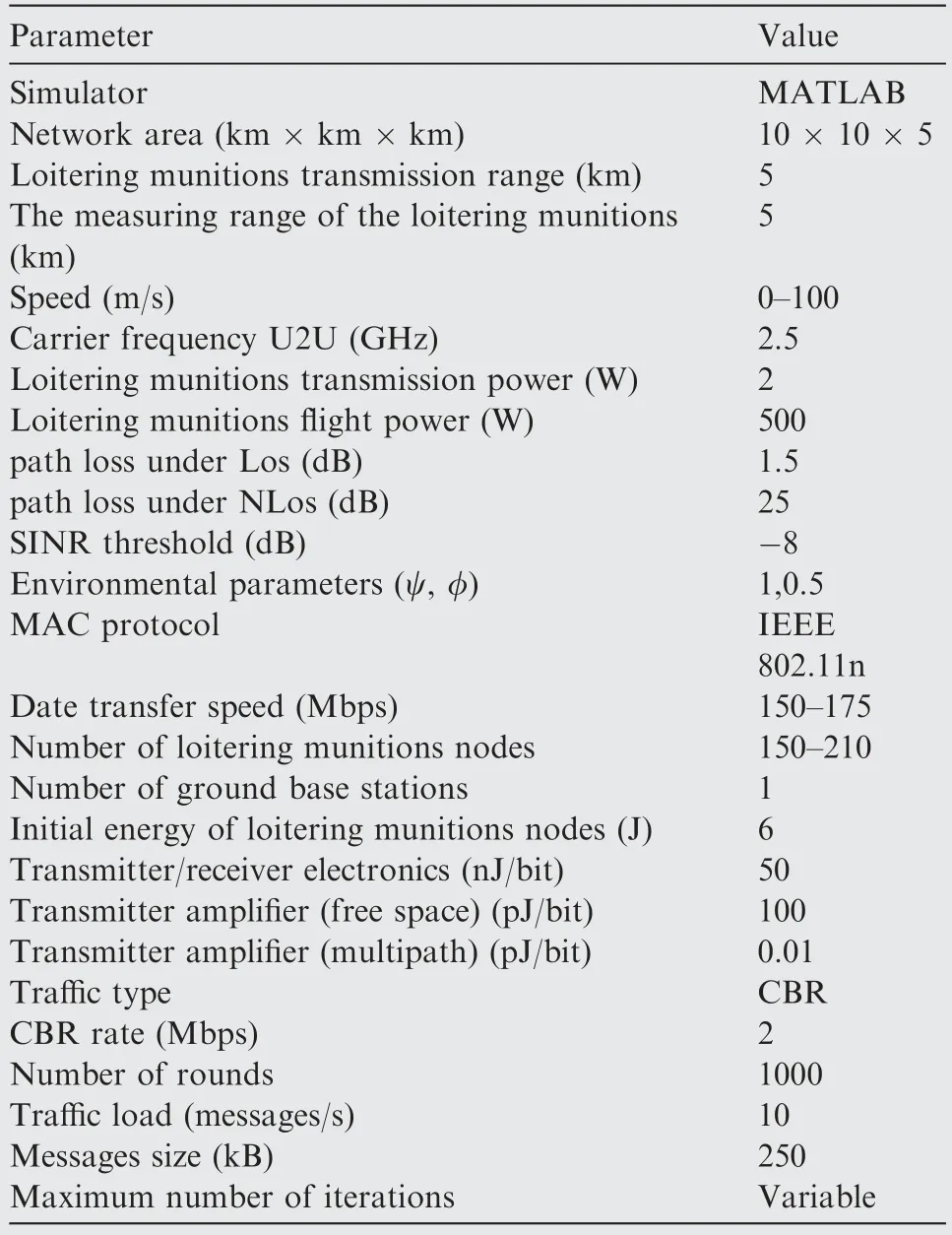
5.1.Simulation environment
5.2.Simulation results and discussion on localization
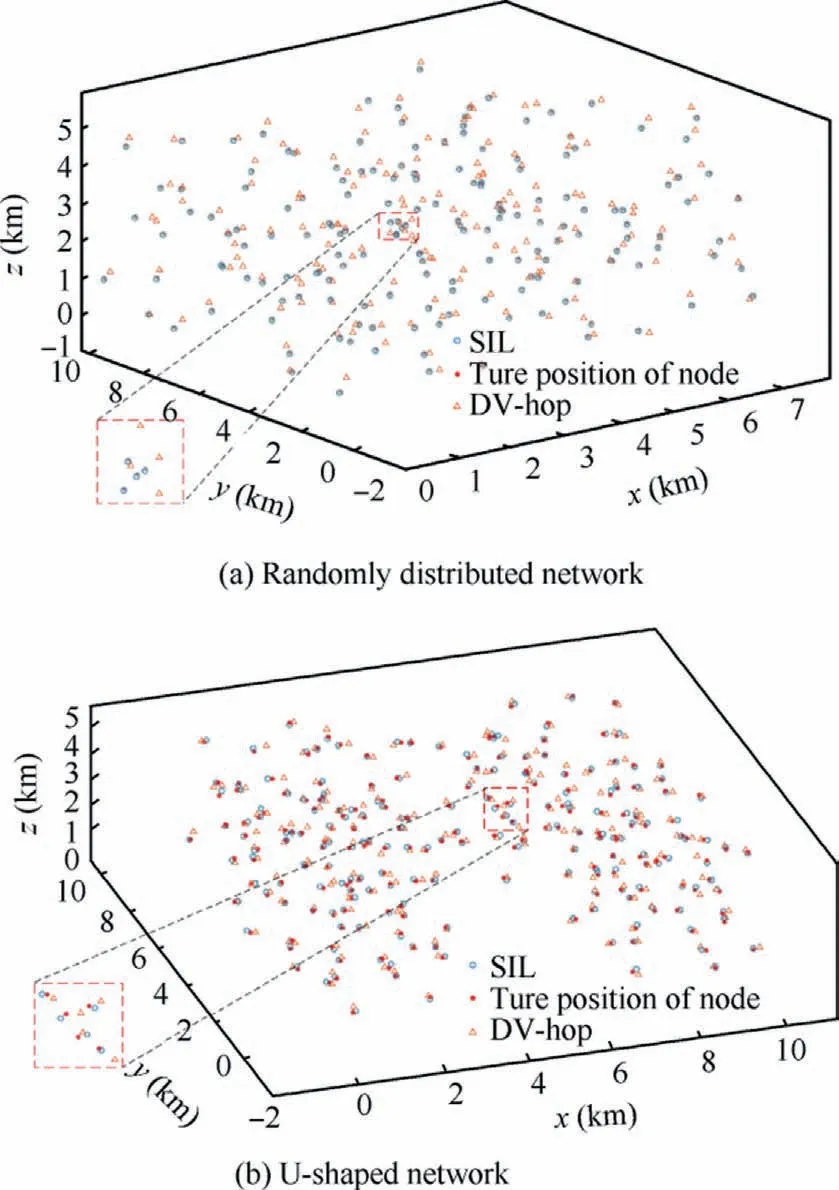
5.3.Simulation results and discussion on clustering



5.4.Simulation results and discussion on routing



6.Conclusions

 CHINESE JOURNAL OF AERONAUTICS2023年10期
CHINESE JOURNAL OF AERONAUTICS2023年10期
